- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (WiNG)
- Re: Wing Ap410 Captive portal
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Wing Ap410 Captive portal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-23-2020 08:46 AM
Hi,
I want to implement two Wifi with captive portal on three AP410. On one AP410 i got working everything ok, this AP is work as controller. DHCP, Captive Portal, Radius. But on other two AP only work DHCP, but i can’t connect with webpage to authorization.
Can you tell me what i miss? Any sugestion?
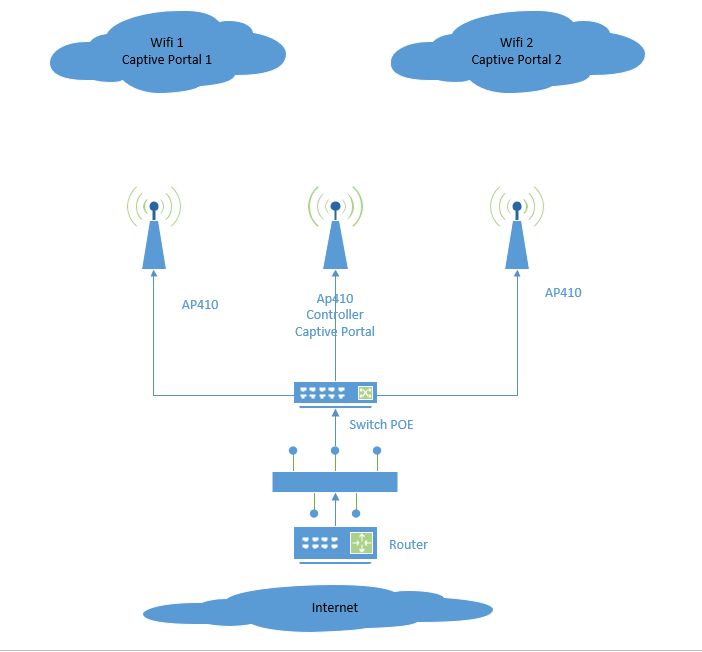
My configuration:
!
! Configuration of AP410 version 7.3.0.0-038R
!
!
version 2.7
!
!
client-identity-group default
load default-fingerprints
!
ip access-list BROADCAST-MULTICAST-CONTROL
permit tcp any any rule-precedence 10 rule-description "permit all TCP traffic"
permit udp any eq 67 any eq dhcpc rule-precedence 11 rule-description "permit DHCP replies"
deny udp any range 137 138 any range 137 138 rule-precedence 20 rule-description "deny windows netbios"
deny ip any 224.0.0.0/4 rule-precedence 21 rule-description "deny IP multicast"
deny ip any host 255.255.255.255 rule-precedence 22 rule-description "deny IP local broadcast"
permit ip any any rule-precedence 100 rule-description "permit all IP traffic"
!
mac access-list PERMIT-ARP-AND-IPv4
permit any any type ip rule-precedence 10 rule-description "permit all IPv4 traffic"
permit any any type arp rule-precedence 20 rule-description "permit all ARP traffic"
!
ip snmp-access-list default
permit any
!
firewall-policy default
no ip dos tcp-sequence-past-window
no stateful-packet-inspection-l2
ip tcp adjust-mss 1400
!
!
mint-policy global-default
!
wlan-qos-policy default
qos trust dscp
qos trust wmm
!
radio-qos-policy default
!
aaa-policy default-onboard
authentication server 1 onboard self
!
captive-portal default-onboard
server host guest-access.net
webpage internal org-name Startowa
use aaa-policy default-onboard
webpage internal registration field city type text enable label "City" placeholder "Enter City"
webpage internal registration field street type text enable label "Address" placeholder "123 Any Street"
webpage internal registration field name type text enable label "Full Name" placeholder "Enter First Name, Last Name"
webpage internal registration field zip type number enable label "Zip" placeholder "Zip"
webpage internal registration field via-sms type checkbox enable title "SMS Preferred"
webpage internal registration field mobile type number enable label "Mobile" placeholder "Mobile Number with Country code"
webpage internal registration field age-range type dropdown-menu enable label "Age Range" title "Age Range"
webpage internal registration field email type e-address enable mandatory label "Email" placeholder "you@domain.com"
webpage internal registration field via-email type checkbox enable title "Email Preferred"
!
captive-portal default-onboard2
connection-mode https
server host guest-access.net
webpage internal org-name Startowa
webpage internal login description Proszę wpisać Login i Hasło
webpage internal login header Witamy w sieci Startowa Gosc
use aaa-policy default-onboard
webpage internal registration field city type text enable label "City" placeholder "Enter City"
webpage internal registration field street type text enable label "Address" placeholder "123 Any Street"
webpage internal registration field name type text enable label "Full Name" placeholder "Enter First Name, Last Name"
webpage internal registration field zip type number enable label "Zip" placeholder "Zip"
webpage internal registration field via-sms type checkbox enable title "SMS Preferred"
webpage internal registration field mobile type number enable label "Mobile" placeholder "Mobile Number with Country code"
webpage internal registration field age-range type dropdown-menu enable label "Age Range" title "Age Range"
webpage internal registration field email type e-address enable mandatory label "Email" placeholder "you@domain.com"
webpage internal registration field via-email type checkbox enable title "Email Preferred"
!
wlan wlan1
ssid ST-EDU
vlan 2
bridging-mode local
encryption-type none
authentication-type none
no multi-band-operation
no protected-mgmt-frames
use captive-portal default-onboard
captive-portal-enforcement
!
wlan wlan2
ssid ST-Gosc
vlan 3
bridging-mode local
encryption-type none
authentication-type none
no multi-band-operation
no protected-mgmt-frames
use captive-portal default-onboard2
captive-portal-enforcement
!
smart-rf-policy default
no select-shutdown
no smart-sensor
smart-sensor auto-trigger
smart-sensor band smart-band-5GHz
!
radius-group ST-Gosc
guest
policy vlan 3
policy ssid ST-Gosc
rate-limit from-air 100000
rate-limit to-air 100000
!
radius-group default
!
radius-user-pool-policy default
user Gosc password 0 654321 group default
user r.duszczyk password 0 123456 group default
!
radius-server-policy default
use radius-user-pool-policy default
!
dhcp-server-policy default
dhcp-pool DHCP-EDU-Vlan2
network 10.10.10.0/24
address range 10.10.10.20 10.10.10.200
default-router 10.10.10.11
dns-server 10.10.10.11
dhcp-pool DCHP-Gosc-Vlan3
network 10.10.11.0/24
address range 10.10.11.20 10.10.11.200
lease 0 1
default-router 10.10.11.11
dns-server 10.10.11.11
!
!
management-policy default
telnet
no http server
https server
rest-server
ssh
user admin password 1 bffa8-----------------------------------7199 role superuser access all
snmp-server community 0 private rw
snmp-server community 0 public ro
snmp-server user snmptrap v3 encrypted des auth md5 0 admin123
snmp-server user snmpmanager v3 encrypted des auth md5 0 admin123
!
event-system-policy default
!
profile ap410 default-ap410
ip name-server 8.8.8.8
ip name-server 8.8.4.4
ip default-gateway 192.168.1.254
autoinstall configuration
autoinstall firmware
crypto ikev1 policy ikev1-default
isakmp-proposal default encryption aes-256 group 2 hash sha
crypto ikev2 policy ikev2-default
isakmp-proposal default encryption aes-256 group 2 hash sha
crypto ipsec transform-set default esp-aes-256 esp-sha-hmac
crypto ikev1 remote-vpn
crypto ikev2 remote-vpn
crypto auto-ipsec-secure
crypto load-management
crypto remote-vpn-client
interface radio1
wlan wlan1 bss 2 primary
wlan wlan2 bss 3 primary
antenna-mode 2x2
interface radio2
wlan wlan1 bss 1 primary
wlan wlan2 bss 2 primary
antenna-mode 2x2
interface radio3
interface bluetooth1
shutdown
mode le-sensor
interface ge1
switchport mode trunk
switchport trunk allowed vlan 1-3
interface ge2
interface vlan1
ip address dhcp
ip address zeroconf secondary
ip dhcp client request options all
interface vlan2
description "Cap ST-EDU"
ip nat inside
interface vlan3
description "Cap ST-Gosc"
ip nat inside
use firewall-policy default
use client-identity-group default
logging on
ip nat inside source list BROADCAST-MULTICAST-CONTROL precedence 1 interface vlan1 overload
service pm sys-restart
router ospf
adoption-mode controller
!
rf-domain default
location Hol
contact mail@wp.pl
timezone Etc/GMT+1
country-code pl
!
ap410 AA-AA-AA-AA-AA-AA
use profile default-ap410
use rf-domain default
hostname ST-AP01
area 2C
floor Ip
use radius-server-policy default
interface radio1
shutdown
interface radio2
shutdown
interface vlan1
ip address 192.168.1.13/24
ip address zeroconf secondary
interface vlan2
ip address 10.10.10.13/24
interface vlan3
ip address 10.10.11.13/24
use dhcp-server-policy default
use captive-portal server default-onboard
use captive-portal server default-onboard2
ip dns-server-forward
!
ap410 BB-BB-BB-BB-BB-BB
use profile default-ap410
use rf-domain default
hostname ST-AP01
area Wysoki
floor Ip
use radius-server-policy default
interface radio1
shutdown
interface radio2
shutdown
interface vlan1
ip address 192.168.1.12/24
ip address zeroconf secondary
interface vlan2
ip address 10.10.10.12/24
interface vlan3
ip address 10.10.11.12/24
use dhcp-server-policy default
use captive-portal server default-onboard
use captive-portal server default-onboard2
ip dns-server-forward
!
ap410 CC-CC-CC-CC-CC-CC
use profile default-ap410
use rf-domain default
hostname ST-CON0
area Aula
floor Parter
use radius-server-policy default
interface radio1
no shutdown
interface radio2
no shutdown
interface vlan1
description "Virtual Interface for LAN by Wizard"
ip address 192.168.1.11/24
no ip dhcp client request options all
no ip nat
interface vlan2
ip address 10.10.10.11/24
interface vlan3
ip address 10.10.11.11/24
use dhcp-server-policy default
use captive-portal server default-onboard
use captive-portal server default-onboard2
virtual-controller
rf-domain-manager capable
ip dns-server-forward
no adoption-mode
!
!
end
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-26-2020 06:22 PM
Hi Radoslaw,
You shouldn’t have to point the captive portal server host to the IP address of the controller, this is required for the captive portal “centralized mode” where the captive portal runs on a central controller. In case of “internal(self)” the captive portal runs on the AP, and the AP will use the IP interface of the VLAN which is defined in the SSID settings for capture and redirection. If the VLAN IP interface is not defined on the AP and there is no virtual server host FQDN configured, the captive portal will use the IP address of 1.1.1.1 to perform redirection. As IP 1.1.1.1 has now got resolvable to CloudFare, it’s best practice to update the captive portal Server hostname to make sure that process is working correctly.
Looks like you have an IP conflict due to your configuration; both APs have the same IP addresses for VLAN2 and VLAN3. This would also create problems with the captive portal capture and redirection on interface VLAN2 and VLAN3. I would say you fix the IPs, set the virtual server host settings in the captive portal back to the FQDN you had earlier instead of pointing it to the VLAN1 IP of the controller AP, and it should work.
ap410 AA-AA-AA-AA-AA-AA
use profile default-ap410
use rf-domain default
hostname ST-AP01
area Wysoki
floor Ip
interface radio1
no shutdown
interface radio2
no shutdown
interface vlan1
ip address 192.168.1.12/24
ip address zeroconf secondary
interface vlan2
ip address 10.10.10.12/24
no ip nat
interface vlan3
ip address 10.10.11.12/24
ip dns-server-forward
!
ap410 BB-BB-BB-BB-BB-BB
use profile default-ap410
use rf-domain default
hostname ST-AP01
area Wysoki
floor Ip
interface radio1
no shutdown
interface radio2
no shutdown
interface vlan1
ip address 192.168.1.12/24
ip address zeroconf secondary
interface vlan2
ip address 10.10.10.12/24
no ip nat
interface vlan3
ip address 10.10.11.12/24
ip dns-server-forward
Regards,
Ovais
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-24-2020 09:15 PM
Hello Ovais Qayyum
default-ap410 on the virtual controller AP.
use radius-server-policy default
use dhcp-server-policy default
use captive-portal server default-onboard
use captive-portal server default-onboard2
Ok I moved this to profile:
connection-mode https - > I backed to http
radius-group ST-Gosc → I removed this radius-group and left only default.
At now situation look like that
- when I connect to radio on main AP working as constroler the Captive portal is availabe and i can log by radius and to wifi
- When I connect to radio on any other AP the web page Captive portal is not availiable
Actual configutration
sh running-config
!
! Configuration of AP410 version 7.3.0.0-038R
!
!
version 2.7
!
!
client-identity-group default
load default-fingerprints
!
ip access-list BROADCAST-MULTICAST-CONTROL
permit tcp any any rule-precedence 10 rule-description "permit all TCP traffic"
permit udp any eq 67 any eq dhcpc rule-precedence 11 rule-description "permit DHCP replies"
deny udp any range 137 138 any range 137 138 rule-precedence 20 rule-description "deny windows netbios"
deny ip any 224.0.0.0/4 rule-precedence 21 rule-description "deny IP multicast"
deny ip any host 255.255.255.255 rule-precedence 22 rule-description "deny IP local broadcast"
permit ip any any rule-precedence 100 rule-description "permit all IP traffic"
!
mac access-list PERMIT-ARP-AND-IPv4
permit any any type ip rule-precedence 10 rule-description "permit all IPv4 traffic"
permit any any type arp rule-precedence 20 rule-description "permit all ARP traffic"
!
ip snmp-access-list default
permit any
!
firewall-policy default
no ip dos tcp-sequence-past-window
no stateful-packet-inspection-l2
ip tcp adjust-mss 1400
!
!
mint-policy global-default
!
wlan-qos-policy default
qos trust dscp
qos trust wmm
!
radio-qos-policy default
!
aaa-policy default-onboard
authentication server 1 onboard self
!
captive-portal default-onboard
server host guest-access.net
webpage internal org-name Startowa
use aaa-policy default-onboard
webpage internal registration field city type text enable label "City" placeholder "Enter City"
webpage internal registration field street type text enable label "Address" placeholder "123 Any Street"
webpage internal registration field name type text enable label "Full Name" placeholder "Enter First Name, Last Name"
webpage internal registration field zip type number enable label "Zip" placeholder "Zip"
webpage internal registration field via-sms type checkbox enable title "SMS Preferred"
webpage internal registration field mobile type number enable label "Mobile" placeholder "Mobile Number with Country code"
webpage internal registration field age-range type dropdown-menu enable label "Age Range" title "Age Range"
webpage internal registration field email type e-address enable mandatory label "Email" placeholder "you@domain.com"
webpage internal registration field via-email type checkbox enable title "Email Preferred"
!
captive-portal default-onboard2
server host guest-access.net
webpage internal org-name Startowa
webpage internal login header Witamy w sieci Startowa Gosc
use aaa-policy default-onboard
webpage internal registration field city type text enable label "City" placeholder "Enter City"
webpage internal registration field street type text enable label "Address" placeholder "123 Any Street"
webpage internal registration field name type text enable label "Full Name" placeholder "Enter First Name, Last Name"
webpage internal registration field zip type number enable label "Zip" placeholder "Zip"
webpage internal registration field via-sms type checkbox enable title "SMS Preferred"
webpage internal registration field mobile type number enable label "Mobile" placeholder "Mobile Number with Country code"
webpage internal registration field age-range type dropdown-menu enable label "Age Range" title "Age Range"
webpage internal registration field email type e-address enable mandatory label "Email" placeholder "you@domain.com"
webpage internal registration field via-email type checkbox enable title "Email Preferred"
!
wlan ST-Test
ssid ST-Test
vlan 3
bridging-mode local
encryption-type none
authentication-type none
no multi-band-operation
no protected-mgmt-frames
!
wlan wlan1
ssid ST-EDU
vlan 2
bridging-mode local
encryption-type none
authentication-type none
no multi-band-operation
no protected-mgmt-frames
use captive-portal default-onboard
captive-portal-enforcement
!
wlan wlan2
ssid ST-Gosc
vlan 3
bridging-mode local
encryption-type none
authentication-type none
no multi-band-operation
no protected-mgmt-frames
use captive-portal default-onboard2
captive-portal-enforcement
!
smart-rf-policy default
no select-shutdown
no smart-sensor
smart-sensor auto-trigger
smart-sensor band smart-band-5GHz
!
radius-group default
!
radius-user-pool-policy default
user Gosc password 0 654321 group default
user r.duszczyk password 0 123456 default
!
radius-server-policy default
use radius-user-pool-policy default
!
dhcp-server-policy default
dhcp-pool DHCP-EDU-Vlan2
network 10.10.10.0/24
address range 10.10.10.20 10.10.10.200
default-router 10.10.10.11
dns-server 10.10.10.11
dhcp-pool DCHP-Gosc-Vlan3
network 10.10.11.0/24
address range 10.10.11.20 10.10.11.200
lease 0 1
default-router 10.10.11.11
dns-server 10.10.11.11
!
!
management-policy default
telnet
no http server
https server
rest-server
ssh
user admin password 1 bffa8-----------------------------------7199 role superuser access all
snmp-server community 0 private rw
snmp-server community 0 public ro
snmp-server user snmptrap v3 encrypted des auth md5 0 admin123
snmp-server user snmpmanager v3 encrypted des auth md5 0 admin123
!
event-system-policy default
!
profile ap410 default-ap410
ip name-server 8.8.8.8
ip name-server 8.8.4.4
ip default-gateway 192.168.1.254
autoinstall configuration
autoinstall firmware
use radius-server-policy default
crypto ikev1 policy ikev1-default
isakmp-proposal default encryption aes-256 group 2 hash sha
crypto ikev2 policy ikev2-default
isakmp-proposal default encryption aes-256 group 2 hash sha
crypto ipsec transform-set default esp-aes-256 esp-sha-hmac
crypto ikev1 remote-vpn
crypto ikev2 remote-vpn
crypto auto-ipsec-secure
crypto load-management
crypto remote-vpn-client
interface radio1
wlan wlan1 bss 2 primary
wlan wlan2 bss 3 primary
antenna-mode 2x2
interface radio2
wlan wlan1 bss 1 primary
wlan wlan2 bss 2 primary
antenna-mode 2x2
interface radio3
interface bluetooth1
shutdown
mode le-sensor
interface ge1
switchport mode trunk
switchport trunk allowed vlan 1-3
interface ge2
interface vlan1
ip address dhcp
ip address zeroconf secondary
ip dhcp client request options all
interface vlan2
description "Cap ST-EDU"
ip nat inside
interface vlan3
description "Cap ST-Gosc"
ip nat inside
use dhcp-server-policy default
use firewall-policy default
use captive-portal server default-onboard
use captive-portal server default-onboard2
use client-identity-group default
logging on
ip nat inside source list BROADCAST-MULTICAST-CONTROL precedence 1 interface vlan1 overload
service pm sys-restart
router ospf
adoption-mode controller
!
rf-domain default
location Hol
contact raddus@wp.pl
timezone Etc/GMT+1
country-code pl
!
ap410 AA-AA-AA-AA-AA-AA
use profile default-ap410
use rf-domain default
hostname ST-AP01
area Wysoki
floor Ip
interface radio1
no shutdown
interface radio2
no shutdown
interface vlan1
ip address 192.168.1.12/24
ip address zeroconf secondary
interface vlan2
ip address 10.10.10.12/24
no ip nat
interface vlan3
ip address 10.10.11.12/24
ip dns-server-forward
!
ap410 BB-BB-BB-BB-BB-BB
use profile default-ap410
use rf-domain default
hostname ST-AP01
area Wysoki
floor Ip
interface radio1
no shutdown
interface radio2
no shutdown
interface vlan1
ip address 192.168.1.12/24
ip address zeroconf secondary
interface vlan2
ip address 10.10.10.12/24
no ip nat
interface vlan3
ip address 10.10.11.12/24
ip dns-server-forward
!
ap410 CC-CC-CC-CC-CC-CC
use profile default-ap410
use rf-domain default
hostname ST-CON0
area Aula
floor Parter
interface radio1
no shutdown
interface radio2
no shutdown
interface vlan1
description "Virtual Interface for LAN by Wizard"
ip address 192.168.1.11/24
no ip dhcp client request options all
no ip nat
interface vlan2
ip address 10.10.10.11/24
interface vlan3
ip address 10.10.11.11/24
virtual-controller
rf-domain-manager capable
ip dns-server-forward
no adoption-mode
!
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-24-2020 03:10 AM
Hi Radoslaw,
Do you even see the splash page when you connect to the other two APs? or you see the page but authentication fails?
I would recommend you to use the profile based configuration on the virtual controller AP to make things easier for you to configure and troubleshoot. I see that you have the following 4 parameters configured as overrides on every AP; remove these overrides and move them to the profile ap410 default-ap410 on the virtual controller AP.
use radius-server-policy default
use dhcp-server-policy default
use captive-portal server default-onboard
use captive-portal server default-onboard2
You also need to make the following configuration changes:
connection-mode https → do you have a captive portal certificate loaded on the AP trust point? if not, use the default HTTP connection mode to avoid HTTPS cert error every time you connect.
radius-group ST-Gosc
guest
policy vlan 3 → you can remove the VLAN definition
policy ssid ST-Gosc → add your ssid ST-EDU here in the list as well
rate-limit from-air 100000
rate-limit to-air 100000
!
radius-user-pool-policy default
user Gosc password 0 654321 group default
user r.duszczyk password 0 123456 group default → both of these users are created under the default user group whereas your SSIDs are defined under ST-Gosc group.
Let me know how it goes.
Regards,
Ovais
