This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Technical Discussions
- Network Architecture & Design
- Help with intervlan routing ACL
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Help with intervlan routing ACL
Help with intervlan routing ACL
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-07-2015 05:23 PM
Greetings! This is my first post here. My name is John and I'm trying to configure a scalable solution for our monitoring system to keep track of individual circuit health.
I've configured one Extreme Networks X440-48t switch stack as a router connecting to switches at different buildings over metro ethernet circuits.
Each building switch can see the routing switch on a /30 like so:
Routing Switch Stack X440-48t: Building Switches X440-8p's:
VLAN 311: 192.168.252.1/30 -> 192.168.252.2
VLAN 512: 192.168.252.5/30 -> 192.168.252.6
VLAN 242: 192.168.252.9/30 -> 192.168.252.10
Default VLAN: 192.168.2.236/24
|
Core switching stack
|
Internal Core Router
|
192.168.2.254
I want IP traffic coming from 192.168.2.0 network to have access to all VLAN's with those /30 addresses but I do not want each of the switches to be able to communicate with each other.
For example:
192.168.252.2/30 should not be able to communicate with 192.168.252.6/30 or 192.168.252.10/30.
What would be the most efficient and manageable way to do achieve this goal using EXOS ACL's while also planning for the fact that there could be endless VLAN interfaces configured this way in the future?
Thanks in advance for any assistance.
John
I've configured one Extreme Networks X440-48t switch stack as a router connecting to switches at different buildings over metro ethernet circuits.
Each building switch can see the routing switch on a /30 like so:
Routing Switch Stack X440-48t: Building Switches X440-8p's:
VLAN 311: 192.168.252.1/30 -> 192.168.252.2
VLAN 512: 192.168.252.5/30 -> 192.168.252.6
VLAN 242: 192.168.252.9/30 -> 192.168.252.10
Default VLAN: 192.168.2.236/24
|
Core switching stack
|
Internal Core Router
|
192.168.2.254
I want IP traffic coming from 192.168.2.0 network to have access to all VLAN's with those /30 addresses but I do not want each of the switches to be able to communicate with each other.
For example:
192.168.252.2/30 should not be able to communicate with 192.168.252.6/30 or 192.168.252.10/30.
What would be the most efficient and manageable way to do achieve this goal using EXOS ACL's while also planning for the fact that there could be endless VLAN interfaces configured this way in the future?
Thanks in advance for any assistance.
John
10 REPLIES 10
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-02-2015 02:47 PM
Thank you for the update. I'll need to test this on my end.
The 24t needs its firmware updated so I'll have to schedule an outage
The switch that I ran the initial test on does not have ipforwarding enabled and that could explain why it didn't work.
I'll update the firmware this week and confirm.
The 24t needs its firmware updated so I'll have to schedule an outage
The switch that I ran the initial test on does not have ipforwarding enabled and that could explain why it didn't work.
I'll update the firmware this week and confirm.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-02-2015 08:57 AM
Hi John,
I tested multiple scenarios with port isolation.
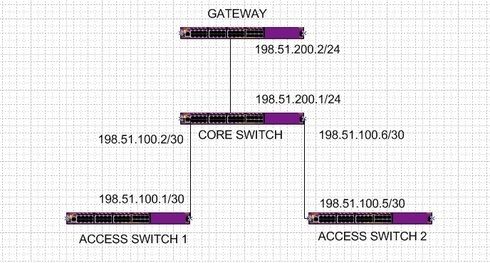
It really does not matter if the port is tagged or untagged. If I make the ports of the core switches connecting to access switches as isolated ports, the access switches do not communicate with each other. But they are able to reach the gateway.
In your network too, it would be ideal to only configure the port isolation in the 24p switch which will do the ipforwarding. Hope this helps!
Please share more details about the issue that you are facing as requested above.
I tested multiple scenarios with port isolation.
It really does not matter if the port is tagged or untagged. If I make the ports of the core switches connecting to access switches as isolated ports, the access switches do not communicate with each other. But they are able to reach the gateway.
In your network too, it would be ideal to only configure the port isolation in the 24p switch which will do the ipforwarding. Hope this helps!
Please share more details about the issue that you are facing as requested above.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-29-2015 02:50 PM
If I get this right, after enabling the port isolation on ports 1-11, it stopped communicating with the port 12 as well. Is that correct?
How about between the ports 1 to 11, are they working as expected?
It would be good to explain the exact traffic that you have tested between the ports 11 and 12. In which VLAN did the traffic flow?
Does the show fdb output display the source and destination mac-address?
Please share these outputs as well.
1. show port 11-12 information detail
2. show fdb port 11-12
I will also test this in parallel and let you know.
How about between the ports 1 to 11, are they working as expected?
It would be good to explain the exact traffic that you have tested between the ports 11 and 12. In which VLAN did the traffic flow?
Does the show fdb output display the source and destination mac-address?
Please share these outputs as well.
1. show port 11-12 information detail
2. show fdb port 11-12
I will also test this in parallel and let you know.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-29-2015 02:42 PM
Thats what I would have thought too. However, I have an 8p running 15.3x at a building and to test, I enabled port isolation on all but the uplink port (12). configure ports 1-11 isolation on
Based off of the description in the docs only *isolated* ports should not be able to forward to each other. port 12 is not isolated it is the trunk uplink back to the colo.
Port 11 has 3 tagged VLAN's none untagged, and port 12 has 1 untagged VLAN and 3 tagged VLAN's.
When I enabled port isolation packet forwarding stopped between 11 & 12.
Am I missing a step in the configuration?
Based off of the description in the docs only *isolated* ports should not be able to forward to each other. port 12 is not isolated it is the trunk uplink back to the colo.
Port 11 has 3 tagged VLAN's none untagged, and port 12 has 1 untagged VLAN and 3 tagged VLAN's.
When I enabled port isolation packet forwarding stopped between 11 & 12.
Am I missing a step in the configuration?