This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Technical Discussions
- Network Architecture & Design
- RE: I need one device to have a specific ip defaul...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
I need one device to have a specific ip default route to another firewall
I need one device to have a specific ip default route to another firewall
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-14-2015 02:32 PM
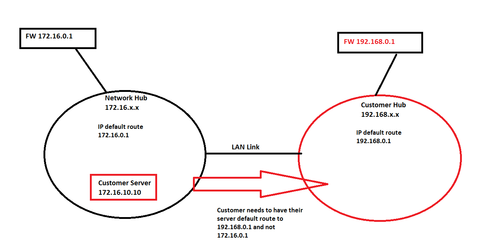
Hi I have a remote site that connects through our hub via LAN and they have their own independent Firewall connection for internet. They communicate to a few devices on our network and everything else is blocked via access-list but they need to have a server on our LAN. Now I need to move their server and host it on our network 172.16.x.x but they need it to use their Firewall for internet access. The only thing I can think of is create an access-list on our Firewall uplink to allow everything but their server and add the server to the access-list that connects to their LAN with addition to add another IP default route inside my hub. That’s the only thing I can think of at the moment, does anyone have a better solution?
19 REPLIES 19
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-14-2015 03:09 PM
The customers LAN is a flat network vs mine but they only need to communicate with a few devices on one VLan which I can give them a range of /29. But like I mentioned to the other user is that I'm a bit confused on where the PBR policy takes place in order to redirect it back to their LAN?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-14-2015 03:09 PM
If you're 172.16.X.X is a flat /16 and that's the only network the customer server needs access to, then I would think a simple PBR ACL on the network hub switch would suffice... According to the subnet masks you have in your diagram everything else would be L2 switched... If there are additional subnets at your hub site that the customer server needs access to, then more specifics would need to be added to the policy.
So something to the effect of:
entry PBR {
if {
source-address 172.16.10.10/32;
destination-address 0.0.0.0/0;
} then {
redirect X.X.X.X (the appropriate next hop for the remote site)
}
}
So something to the effect of:
entry PBR {
if {
source-address 172.16.10.10/32;
destination-address 0.0.0.0/0;
} then {
redirect X.X.X.X (the appropriate next hop for the remote site)
}
}
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-14-2015 03:04 PM
Understood but where would this access-list entry reside on? On the uplink to our Firewall (That doesn't have a access-list) or on the access-list that is between my site and the customers? Because I would like the policy to redirect to there network and not my firewall.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-14-2015 03:04 PM
The server 172.16.10.10 will have to have a default route of 172.16.10.1 . On 172.16.10.1 create a policy based route, if it has that capability, to forward any traffic sourced from 172.16.10.10 to go to the IP address of the Customer Hub on the interface you have drawn and labeled LAN link.
It all depends on if your firewall supports policy based routing.
It all depends on if your firewall supports policy based routing.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-14-2015 02:33 PM