This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Technical Discussions
- Network Architecture & Design
- RE: Identical VLAN gateway config on multiple L3 s...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Identical VLAN gateway config on multiple L3 switches
Identical VLAN gateway config on multiple L3 switches
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-01-2015 05:14 PM
I'm trying to fix a mess that I partly inherited and then exacerbated through ignorance.
We have three X450e-48p switches on a single, flat, /24 network, one per building. One of the switches has a small port-based VLAN but essentially everything else is on the Default VLAN so we may as well have been using L2 switches all this time. Anyway, I need to get this thing under control, so:
The default gateway for basically everything in this 10.10.10.1/24 network is the firewall's ip address. The three switches have ip addresses of 10.10.10.150, 10.10.10.151, 10.10.10.152 which are used to manage them.
Can I create an identical VLAN on each switch such that the default gateway for that VLAN is the same IP address no matter which switch the host is plugged into?
Like, on all three switches can I blow away the VLAN configuration and do this:
create vlan voice_vlan
configure vlan voice_vlan tag 11
configure vlan voice_vlan ipaddress 10.10.11.1/24
configure vlan voice_vlan add ports 1-48 tagged
enable ipforwarding voice_vlan
configure vlan default ipaddress 10.10.10.1/24
configure vlan default add ports 1-48 untagged
enable ipforwarding default
I assume this would create a problem with management access so, given we don't have any dedicated management network to speak of, how would I then manage the switches?
We have three X450e-48p switches on a single, flat, /24 network, one per building. One of the switches has a small port-based VLAN but essentially everything else is on the Default VLAN so we may as well have been using L2 switches all this time. Anyway, I need to get this thing under control, so:
The default gateway for basically everything in this 10.10.10.1/24 network is the firewall's ip address. The three switches have ip addresses of 10.10.10.150, 10.10.10.151, 10.10.10.152 which are used to manage them.
Can I create an identical VLAN on each switch such that the default gateway for that VLAN is the same IP address no matter which switch the host is plugged into?
Like, on all three switches can I blow away the VLAN configuration and do this:
create vlan voice_vlan
configure vlan voice_vlan tag 11
configure vlan voice_vlan ipaddress 10.10.11.1/24
configure vlan voice_vlan add ports 1-48 tagged
enable ipforwarding voice_vlan
configure vlan default ipaddress 10.10.10.1/24
configure vlan default add ports 1-48 untagged
enable ipforwarding default
I assume this would create a problem with management access so, given we don't have any dedicated management network to speak of, how would I then manage the switches?
12 REPLIES 12
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-02-2015 06:26 PM
You pretty much nailed it in that last post. The Default Gateway will need to be different on swB and swC than it is on swA - because swA is acting more like your network core.
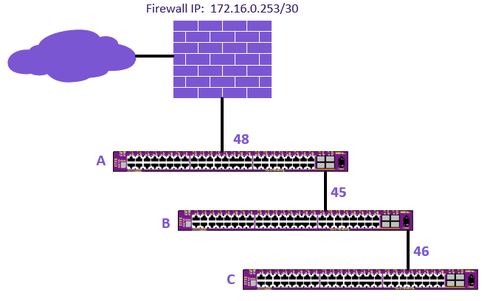
I set it up in the lab to do a quick test. With the configs below, all switches can ping out to the internet. I used a 4th switch for the "firewall" and added a local loopback VLAN to serve as the "internet."
I also decided to create a "users" VLAN instead of using Default. Personally, I'd build it out as Jen0342 mentioned with VLANs for each building - it would require a bit more work, but in the end would help isolate problems and give a cleaner infrastructure (albeit slightly more complicated). In the design below, ipforwarding is enabled on the users and voice VLANs on each switch to keep traffic as local to each switch as possible.
Switch A Config
Switch B Config
Switch C Config
Let me know what you think!
-Drew
I set it up in the lab to do a quick test. With the configs below, all switches can ping out to the internet. I used a 4th switch for the "firewall" and added a local loopback VLAN to serve as the "internet."
I also decided to create a "users" VLAN instead of using Default. Personally, I'd build it out as Jen0342 mentioned with VLANs for each building - it would require a bit more work, but in the end would help isolate problems and give a cleaner infrastructure (albeit slightly more complicated). In the design below, ipforwarding is enabled on the users and voice VLANs on each switch to keep traffic as local to each switch as possible.
Switch A Config
code:
configure vlan default delete ports all create vlan "inet_gw" create vlan "users" create vlan "Voice" configure vlan inet_gw tag 100 configure vlan users tag 10 configure vlan Voice tag 11 configure vlan inet_gw add ports 48 untagged configure vlan users add ports 45 untagged configure vlan Voice add ports 45 tagged configure vlan inet_gw ipaddress 172.16.0.254/30 configure vlan users ipaddress 10.10.10.1/24 configure vlan Voice ipaddress 10.10.11.1/24 enable ipforwarding configure iproute add default 172.16.0.253
Switch B Config
code:
configure vlan default delete ports all create vlan "users" create vlan "Voice" configure vlan users tag 10 configure vlan Voice tag 11 configure vlan users add ports 45,46 untagged configure vlan Voice add ports 45,46 tagged configure vlan Voice ipaddress 10.10.11.2/24 configure vlan users ipaddress 10.10.10.2/24 enable ipforwarding configure iproute add default 10.10.10.1
Switch C Config
code:
configure vlan default delete ports all create vlan "users" create vlan "Voice" configure vlan users tag 10 configure vlan Voice tag 11 configure vlan users add ports 46 untagged configure vlan Voice add ports 46 tagged configure vlan Voice ipaddress 10.10.11.3/24 configure vlan users ipaddress 10.10.10.3/24 enable ipforwarding configure iproute add default 10.10.10.1
Let me know what you think!
-Drew
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-02-2015 01:38 PM
Drew,
I've just read through that thread and, while my first post in this thread may have been a little out there, I think my last post correctly observes the concepts you described. Am I still wrong?
I've just read through that thread and, while my first post in this thread may have been a little out there, I think my last post correctly observes the concepts you described. Am I still wrong?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-02-2015 01:24 PM
Take a look at the response I posted in this thread: https://community.extremenetworks.com/extreme/topics/iproute-if-only-using-l2
It's not the same scenario, but the concepts described may help you understand a little more about the routing that needs to happen in your setup.
It's not the same scenario, but the concepts described may help you understand a little more about the routing that needs to happen in your setup.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-02-2015 11:38 AM
I appreciate your answers and am trying to figure this out. When I first sketched this out I did in fact have multiple VLANs in each building but it just seemed to get excessively complex given the relatively small network we have here. The buildings are connected with small (100ft) fiber runs, they may as well be adjacent rooms, it's not like they're across town.
So, let's forget about switches B and C for a minute.
Can Switch A be configured thus:
configure vlan default ipaddress 10.10.10.1/24
configure vlan default add ports 2-48 untagged
enable ipforwarding default
create vlan voice_vlan
configure vlan voice_vlan tag 11
configure vlan voice_vlan ipaddress 10.10.11.1/24
configure vlan voice_vlan add ports 2-48 tagged
enable ipforwarding voice_vlan
Now we need to get out to the internet so again on switch A:
create vlan internet_gateway
configure vlan internet_gateway ipaddress 172.16.0.254 255.255.255.252
configure vlan internet_gateway add ports 1 untagged
enable ipforwarding internet_gateway
configure iproute add default 172.16.0.253 vr "VR-Default"
172.16.0.253 is now the inside of the firewall which is on switch A port 1.
So, hosts in the default VLAN can talk to VLAN 11 and vice versa. Hosts in the default VLAN can access the internet via a default route to 172.16.0.253. Then, on the firewall I need something like route inside 10.10.10.0 255.255.255.0 172.16.0.254 to get back inside and we're done?
Assuming that single switch configuration isn't nonsense (distinct possibility!) can I not then add the vlan/port/tagging configuration (without ip addresses) to switches B and C like:
create vlan voice_vlan
configure vlan voice_vlan tag 11
configure vlan voice_vlan add ports 1-48 tagged
configure vlan default add ports 1-48 untagged
So, let's forget about switches B and C for a minute.
Can Switch A be configured thus:
configure vlan default ipaddress 10.10.10.1/24
configure vlan default add ports 2-48 untagged
enable ipforwarding default
create vlan voice_vlan
configure vlan voice_vlan tag 11
configure vlan voice_vlan ipaddress 10.10.11.1/24
configure vlan voice_vlan add ports 2-48 tagged
enable ipforwarding voice_vlan
Now we need to get out to the internet so again on switch A:
create vlan internet_gateway
configure vlan internet_gateway ipaddress 172.16.0.254 255.255.255.252
configure vlan internet_gateway add ports 1 untagged
enable ipforwarding internet_gateway
configure iproute add default 172.16.0.253 vr "VR-Default"
172.16.0.253 is now the inside of the firewall which is on switch A port 1.
So, hosts in the default VLAN can talk to VLAN 11 and vice versa. Hosts in the default VLAN can access the internet via a default route to 172.16.0.253. Then, on the firewall I need something like route inside 10.10.10.0 255.255.255.0 172.16.0.254 to get back inside and we're done?
Assuming that single switch configuration isn't nonsense (distinct possibility!) can I not then add the vlan/port/tagging configuration (without ip addresses) to switches B and C like:
create vlan voice_vlan
configure vlan voice_vlan tag 11
configure vlan voice_vlan add ports 1-48 tagged
configure vlan default add ports 1-48 untagged
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-01-2015 06:03 PM
Assuming the firewall is doing the routing and configured correctly all you would need to do is add all 3 vlans into the each switch. An IP address is not needed and it should travel via L2 to the firewall. The uplink ports would have to be "trunked" by adding the uplink port to all 3 vlans as tagged. You can keep the IP address on that one vlan for MGMT access.