This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Extreme Access Control (EAC) freeradius default ci...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Extreme Access Control (EAC) freeradius default cipher list
Extreme Access Control (EAC) freeradius default cipher list
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-16-2017 07:17 PM
The default ciphers in freeradius on the EAC engine config for eap is:
cipher_list = "ADH-AES128-GCM-SHA256:ADH-AES128-SHA:ADH-AES128-SHA256:
ADH-AES256-GCM-SHA384:ADH-AES256-SHA:ADH-AES256-SHA256:ADH-CAMELLIA128-SHA:
ADH-CAMELLIA256-SHA:AECDH-AES128-SHA:AECDH-AES256-SHA:AES128-GCM-SHA256:
AES128-SHA:AES128-SHA256:AES256-GCM-SHA384:AES256-SHA:AES256-SHA256:
CAMELLIA128-SHA:CAMELLIA256-SHA:DHE-DSS-AES128-GCM-SHA256:
DHE-DSS-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-DSS-AES256-GCM-SHA384:
DHE-DSS-AES256-SHA:DHE-DSS-AES256-SHA256:DHE-DSS-CAMELLIA128-SHA:
DHE-DSS-CAMELLIA256-SHA:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA:
DHE-RSA-AES128-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA:
DHE-RSA-AES256-SHA256:DHE-RSA-CAMELLIA128-SHA:DHE-RSA-CAMELLIA256-SHA:
ECDH-ECDSA-AES128-GCM-SHA256:ECDH-ECDSA-AES128-SHA:
ECDH-ECDSA-AES128-SHA256:ECDH-ECDSA-AES256-GCM-SHA384:
ECDH-ECDSA-AES256-SHA:ECDH-ECDSA-AES256-SHA384:ECDH-RSA-AES128-GCM-SHA256:
ECDH-RSA-AES128-SHA:ECDH-RSA-AES128-SHA256:ECDH-RSA-AES256-GCM-SHA384:
ECDH-RSA-AES256-SHA:ECDH-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:
ECDHE-ECDSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA256:
ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA:
ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES128-GCM-SHA256:
ECDHE-RSA-AES128-SHA:ECDHE-RSA-AES128-SHA256:
ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES256-SHA384:
PSK-AES128-CBC-SHA:PSK-AES256-CBC-SHA:SRP-AES-128-CBC-SHA:
SRP-AES-256-CBC-SHA:SRP-DSS-AES-128-CBC-SHA:SRP-DSS-AES-256-CBC-SHA:
SRP-RSA-AES-128-CBC-SHA:SRP-RSA-AES-256-CBC-SHA"
It seems this config is generated with something like:
openssl ciphers HIGH | tr ':' '\n' | sort | grep -v RC4 | tr '\n' ':'which is controled by application properties (default values):
RADIUS_TLS_CIPHER_LIST = "HIGH"
RADIUS_TLS_REMOVE_RC4_CIPHERS = trueSo the list is sorted and the weak ciphers (128 < 256) gets in front. I don't know
how the EAC implementation uses this list, but the default openssl libs use
this list as an ordered list. So the weakest ciphers are used first.
Isn't this a security bug?
cipher_list = "ADH-AES128-GCM-SHA256:ADH-AES128-SHA:ADH-AES128-SHA256:
ADH-AES256-GCM-SHA384:ADH-AES256-SHA:ADH-AES256-SHA256:ADH-CAMELLIA128-SHA:
ADH-CAMELLIA256-SHA:AECDH-AES128-SHA:AECDH-AES256-SHA:AES128-GCM-SHA256:
AES128-SHA:AES128-SHA256:AES256-GCM-SHA384:AES256-SHA:AES256-SHA256:
CAMELLIA128-SHA:CAMELLIA256-SHA:DHE-DSS-AES128-GCM-SHA256:
DHE-DSS-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-DSS-AES256-GCM-SHA384:
DHE-DSS-AES256-SHA:DHE-DSS-AES256-SHA256:DHE-DSS-CAMELLIA128-SHA:
DHE-DSS-CAMELLIA256-SHA:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA:
DHE-RSA-AES128-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA:
DHE-RSA-AES256-SHA256:DHE-RSA-CAMELLIA128-SHA:DHE-RSA-CAMELLIA256-SHA:
ECDH-ECDSA-AES128-GCM-SHA256:ECDH-ECDSA-AES128-SHA:
ECDH-ECDSA-AES128-SHA256:ECDH-ECDSA-AES256-GCM-SHA384:
ECDH-ECDSA-AES256-SHA:ECDH-ECDSA-AES256-SHA384:ECDH-RSA-AES128-GCM-SHA256:
ECDH-RSA-AES128-SHA:ECDH-RSA-AES128-SHA256:ECDH-RSA-AES256-GCM-SHA384:
ECDH-RSA-AES256-SHA:ECDH-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:
ECDHE-ECDSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA256:
ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA:
ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES128-GCM-SHA256:
ECDHE-RSA-AES128-SHA:ECDHE-RSA-AES128-SHA256:
ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES256-SHA384:
PSK-AES128-CBC-SHA:PSK-AES256-CBC-SHA:SRP-AES-128-CBC-SHA:
SRP-AES-256-CBC-SHA:SRP-DSS-AES-128-CBC-SHA:SRP-DSS-AES-256-CBC-SHA:
SRP-RSA-AES-128-CBC-SHA:SRP-RSA-AES-256-CBC-SHA"
It seems this config is generated with something like:
openssl ciphers HIGH | tr ':' '\n' | sort | grep -v RC4 | tr '\n' ':'which is controled by application properties (default values):
RADIUS_TLS_CIPHER_LIST = "HIGH"
RADIUS_TLS_REMOVE_RC4_CIPHERS = trueSo the list is sorted and the weak ciphers (128 < 256) gets in front. I don't know
how the EAC implementation uses this list, but the default openssl libs use
this list as an ordered list. So the weakest ciphers are used first.
Isn't this a security bug?
6 REPLIES 6
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-21-2017 07:52 PM
Hi Patrick,
freeRADIUS seems to fully rely on openSSL to negotiate suitable cipher.
It is set in eap.conf and default string seems to go like this
ALL:!EXPORT:!LOW:!aNULL:!eNULL:!SSLv2It may obviously differ based on intended server settings.
See more details in openSSL ciphers documentation
Anyway, it i the client who sets rules and cipher order seen on server side is quite irrelevant.
See page from openSSL s_server manual
Let me know if you have any more questions.
Regards,
Ondrej
freeRADIUS seems to fully rely on openSSL to negotiate suitable cipher.
It is set in eap.conf and default string seems to go like this
ALL:!EXPORT:!LOW:!aNULL:!eNULL:!SSLv2It may obviously differ based on intended server settings.
See more details in openSSL ciphers documentation
Anyway, it i the client who sets rules and cipher order seen on server side is quite irrelevant.
See page from openSSL s_server manual
-cipher cipherlistThere might be an exception related to server preferences, but this must be set within s_server SSL_CTX configuration
this allows the cipher list used by the server to be modified. When the client sends a list of supported ciphers the first client cipher also included in the server list is used. Because the client specifies the preference order, the order of the server cipherlist irrelevant. See the ciphers command for more information.
SSL_OP_CIPHER_SERVER_PREFERENCEYou might give it a try with simple test - capturing authentication between client and server or try to find ssl.h and double check it is not used.
When choosing a cipher, use the server's preferences instead of the client preferences. When not set, the SSL server will always follow the clients preferences. When set, the SSLv3/TLSv1 server will choose following its own preferences. Because of the different protocol, for SSLv2 the server will send its list of preferences to the client and the client chooses.
Let me know if you have any more questions.
Regards,
Ondrej
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-21-2017 07:52 PM
Hi Patrick,
yes, in tls.c is written that CTX prefers server list.
Here is what openssl wiki says
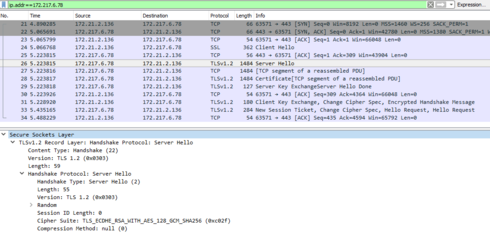
Could you share packet capture filtered with EAC IP to compare it?
If you do not like ciphers used by server, you might change the cipher list limiting weak ones. However, take in consideration wider support by older supplicants.
Regards,
Ondrej
yes, in tls.c is written that CTX prefers server list.
Here is what openssl wiki says
So it is implementation dependent. In openssl there are two modes:If EAC uses server preferences you may only benefit from it. Today TLS severs usually relay on Eliptic Curves - GCM based ciphers and upon response to client server may use only specific cipher. See below
- default is to choose the first compatible cipher suite from client hello.
- SSL_OP_CIPHER_SERVER_PREFERENCE to SSL_CTX_set_option to choose from server cipher list order
Could you share packet capture filtered with EAC IP to compare it?
If you do not like ciphers used by server, you might change the cipher list limiting weak ones. However, take in consideration wider support by older supplicants.
Regards,
Ondrej
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-21-2017 07:52 PM
Hi Ondrej,
if you look at the source code of freeradius (stable, not EOL):
if (conf->cipher_server_preference) {
/*
* SSL_OP_CIPHER_SERVER_PREFERENCE to follow best practice
* of nowday's TLS: do not allow poorly-selected ciphers from
* * client to take preference
*/
ctx_options |= SSL_OP_CIPHER_SERVER_PREFERENCE;
}Regards,
Patrick
if you look at the source code of freeradius (stable, not EOL):
if (conf->cipher_server_preference) {
/*
* SSL_OP_CIPHER_SERVER_PREFERENCE to follow best practice
* of nowday's TLS: do not allow poorly-selected ciphers from
* * client to take preference
*/
ctx_options |= SSL_OP_CIPHER_SERVER_PREFERENCE;
}Regards,
Patrick
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-21-2017 07:52 PM
Hi Ondrej,
during the TLS handshake the server sends his cipher list to the client and the client
this his to the server.
https://en.wikipedia.org/wiki/Transport_Layer_Security#TLS_handshake
The should agree on the stongest cipher. But if the client choses
the cipher (that itself would be a security risk), you have to check every implementation
of every client. If any of them uses this as a ordered list, your implementation is a
security bug.
You relying on:
cryptographic expert but I still think this is a security bug in EMC/EAC.
Regards
Patrick
during the TLS handshake the server sends his cipher list to the client and the client
this his to the server.
https://en.wikipedia.org/wiki/Transport_Layer_Security#TLS_handshake
The should agree on the stongest cipher. But if the client choses
the cipher (that itself would be a security risk), you have to check every implementation
of every client. If any of them uses this as a ordered list, your implementation is a
security bug.
You relying on:
- implementation of freeradius
- implementation of openssl
- implementation of every client
cryptographic expert but I still think this is a security bug in EMC/EAC.
Regards
Patrick