This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud A3
- Re: How to configure radius authentication for EXO...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to configure radius authentication for EXOS switch management
How to configure radius authentication for EXOS switch management
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-05-2022 03:28 PM
Hello,
I'm trying to configure A3 as our radius-mgmt server for switch authentication. I found an older article that mentions only Cicso Management Authentications are supported? The EXOS switch is a 440G2 running 31.3.1.3-patch1-10, with radius mgmt-access enabled and correct shared-secret. I enabled 'CLI Access' under the device settings as well. The RADIUS log show 'Auth Rejected' and I'm not sure what step/filter I might be missing.
Any guidance or step-by-step guides you can provide would be great.
Thanks,
Matt
I'm trying to configure A3 as our radius-mgmt server for switch authentication. I found an older article that mentions only Cicso Management Authentications are supported? The EXOS switch is a 440G2 running 31.3.1.3-patch1-10, with radius mgmt-access enabled and correct shared-secret. I enabled 'CLI Access' under the device settings as well. The RADIUS log show 'Auth Rejected' and I'm not sure what step/filter I might be missing.
Any guidance or step-by-step guides you can provide would be great.
Thanks,
Matt
11 REPLIES 11
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-27-2022 02:46 AM
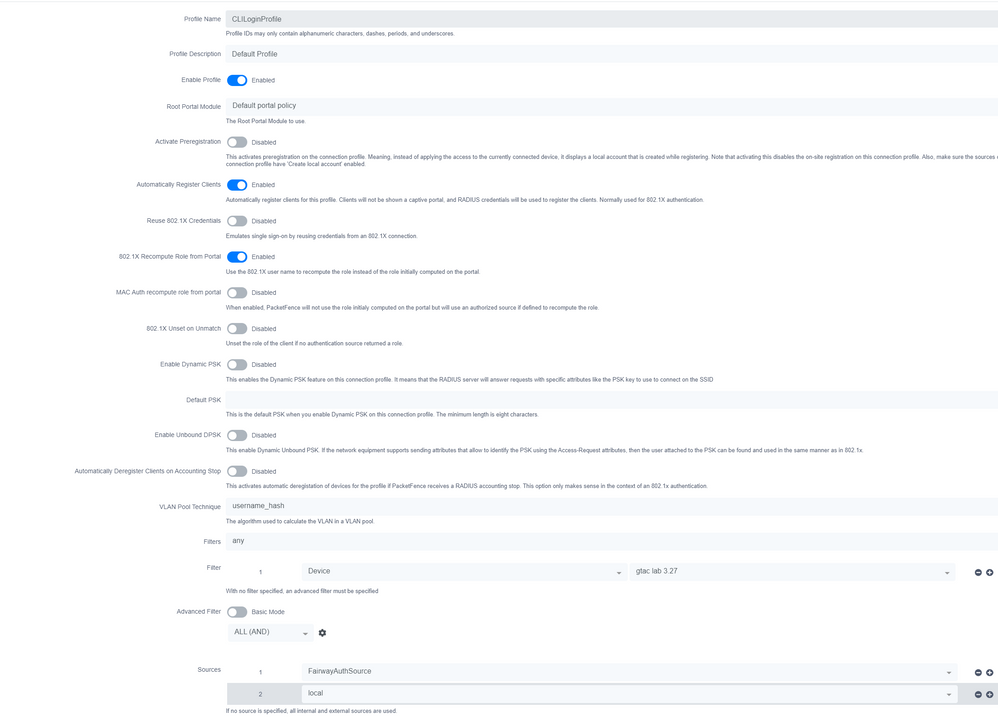
Connection Profile
 Authentication source
Authentication source
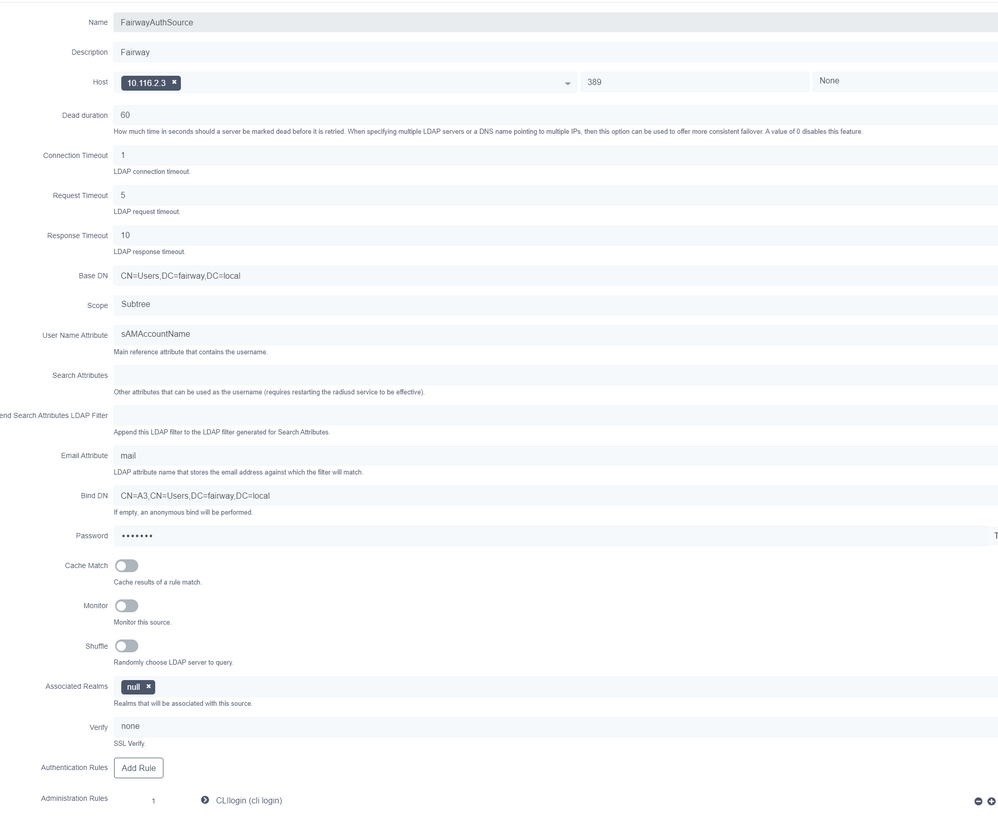 Auth source rule
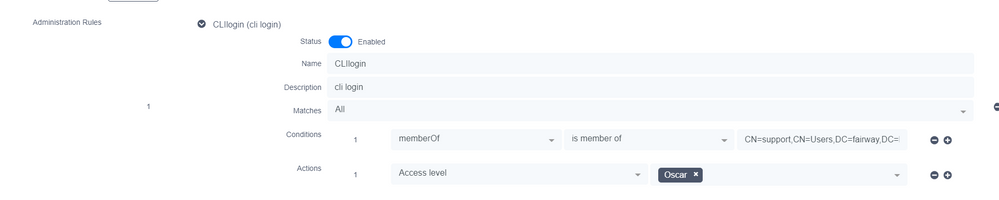
Auth source rule
 Authentication source
Authentication source Auth source rule
Auth source rule
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-26-2022 02:26 PM
I was testing some other features with A3 so I just got back to this. Can you send me a screenshot of your setup?
Here's the RADIUS log entry for the test account I setup...
Here's the RADIUS log entry for the test account I setup...
User-Name = "testuser" User-Password = "******" NAS-IP-Address = 10.10.200.1 NAS-Port = 0 Service-Type = Login-User Called-Station-Id = "00:04:96:9e:57:50" Calling-Station-Id = "10.24.156.103" NAS-Identifier = "lab_es01" Proxy-State = 0x3834 NAS-Port-Type = Virtual Event-Timestamp = "Jan 26 2022 14:25:16 EST" Message-Authenticator = 0xa44631837f24d451e2bc18af610cf90e Stripped-User-Name = "testuser" Realm = "null" FreeRADIUS-Client-IP-Address = 10.24.10.156 PacketFence-KeyBalanced = "8d43c43cef1ed029bd9bb5b119c2518d" PacketFence-Radius-Ip = "10.24.10.155" PacketFence-Src-Ip = "10.10.200.1" SQL-User-Name = "testuser"
Reply-Message = "Mac is empty" Proxy-State = 0x3834
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-21-2022 02:26 AM
Hi,
in the connection profile I have 1 profile that filters simply on device IP for test but in a real network you should match on the right connection type or maybe port.
In the sources of the profile add local.
Create a local user and set the actions to the correct access-level. Make sure the time/date are good. There were issue's where the user could only login the next day as the start time was set wrong.
in the connection profile I have 1 profile that filters simply on device IP for test but in a real network you should match on the right connection type or maybe port.
In the sources of the profile add local.
Create a local user and set the actions to the correct access-level. Make sure the time/date are good. There were issue's where the user could only login the next day as the start time was set wrong.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-20-2022 02:28 PM
Thanks Oscar!
Can you send me your local user auth setup? I'd like to test that as well, maybe using A3 local user auth is the better option here.
Can you send me your local user auth setup? I'd like to test that as well, maybe using A3 local user auth is the better option here.
