This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Can't select user groups in authentication mapping
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can't select user groups in authentication mapping
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-08-2019 09:47 AM
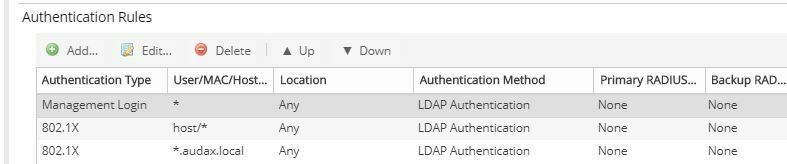
In the EAC you can configure the authentication rules in the AAA section. in one of those rules (Management Login) I want to configure an user group .
According to the help file ,should this be possible.
User/MAC/Host
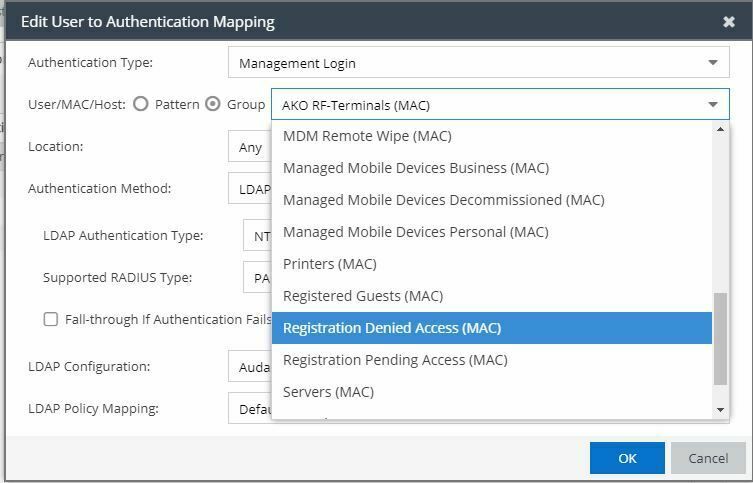
Select the Pattern radio button and enter the username, MAC address, or hostname that the end-system must match for this mapping. Or, select the Group radio button and select a user group or end-system group from the drop-down list. If you enter a MAC address, you can use a colon (:) or a dash (-) as an address delimiter, but not a period (.).
The only groups I can select are End-System Groups.
How can I select an user groups ?
According to the help file ,should this be possible.
User/MAC/Host
Select the Pattern radio button and enter the username, MAC address, or hostname that the end-system must match for this mapping. Or, select the Group radio button and select a user group or end-system group from the drop-down list. If you enter a MAC address, you can use a colon (:) or a dash (-) as an address delimiter, but not a period (.).
The only groups I can select are End-System Groups.
How can I select an user groups ?
Johan Hendrik
System Architect
Audax
Solved! Go to Solution.
1 ACCEPTED SOLUTION
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-21-2019 12:31 PM
The switch might be allowing you in just because the Access was "Accept". Can you change the "Denied Access NAC profile" and set it to "Reject authentication requests".
It will be the option at the top of the profile.
Thanks
-Ryan
It will be the option at the top of the profile.
Thanks
-Ryan
7 REPLIES 7
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-15-2019 09:37 AM
I've made roles and tested a connection to a swtich and a connection to an EWC controller.
Both systems have the same EAC controlers.
When connecting to the EWC with wrong credentials , the connection is refused.
When I do the test to a switch I can loging and have user rights.
Did I forgot something?
Both systems have the same EAC controlers.
When connecting to the EWC with wrong credentials , the connection is refused.
When I do the test to a switch I can loging and have user rights.
Did I forgot something?
Johan Hendrik
System Architect
Audax
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-10-2019 05:51 PM
Hello Johan,
LDAP usergroups can only be used in the AAA with authentication type "Registration (Auth&Admin)".
Are you looking to send management authentications to a different authentication server based on LDAP group membership, or prevent access based on group membership?
If you're looking to prevent access based on LDAP membership the way you would do that is create a rule in the rules engine with LDAP usergroup that had an accept with appropriate management access AVPs, and below this rule create another rule for all management requests to would deny.
That way unless you're part of the LDAP group configured in the first rule you'll fall into a deny role.
Let me know if this is what you're looking for.
Thanks
-Ryan
LDAP usergroups can only be used in the AAA with authentication type "Registration (Auth&Admin)".
Are you looking to send management authentications to a different authentication server based on LDAP group membership, or prevent access based on group membership?
If you're looking to prevent access based on LDAP membership the way you would do that is create a rule in the rules engine with LDAP usergroup that had an accept with appropriate management access AVPs, and below this rule create another rule for all management requests to would deny.
That way unless you're part of the LDAP group configured in the first rule you'll fall into a deny role.
Let me know if this is what you're looking for.
Thanks
-Ryan
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-09-2019 08:05 AM
Extra information: I cann't select LDAP user groups that are created.
Johan Hendrik
System Architect
Audax