- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: Cisco Trunk Interface with Extreme NAC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Trunk Interface with Extreme NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-12-2020 07:33 AM
Dear All
I’m trying to enable Extreme NAC for Cisco switches. It works fine for Clients on Access Ports. For Accesspoints (local breakout), I’m trying to get a trunk interface with management vlan untagged and data VLANs tagged.
For XOS Switches, I would create a Role with the needed VLAN Egress config
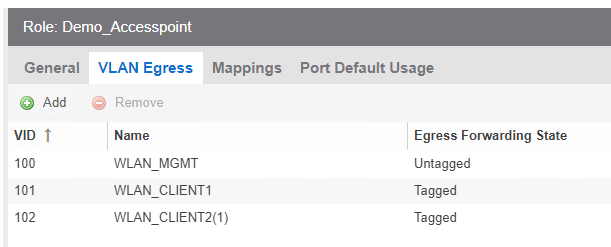
But I cant enforce this role configuration to Cisco switches
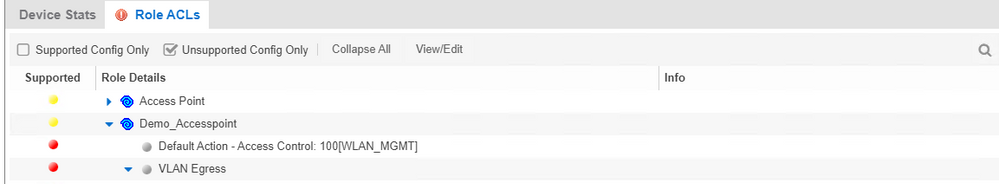
How can I achieve that for Cisco switches with Extreme NAC?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-15-2020 11:53 AM
Hi Miguel
Yes sure, I can share my cisco config. In the meantime, I tested NEAT as well and it seems to be easier than using macro.
Macro
conf t
no macro auto global control device
no macro auto global control trigger
macro auto global processing
macro auto execute AP_TRUNK {
if [[ $LINKUP == YES ]]
then conf t
default interface $INTERFACE
interface $INTERFACE
Description AP_TRUNK
macro description $TRIGGER
switchport trunk allowed vlan ##VLAN-LIST##
switchport trunk native vlan ##VLAN##
switchport mode trunk
spanning-tree portfast trunk
macro auto processing
exit
fi
if [[ $LINKUP == NO ]]
then conf t
default interface $INTERFACE
interface $INTERFACE
description NAC
no switchport trunk allowed vlan
no switchport trunk native vlan
switchport mode access
macro auto processing
authentication control-direction in
authentication event server dead action authorize
authentication event server dead action authorize voice
authentication event server alive action reinitialize
authentication host-mode multi-host
authentication order mab dot1x
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation restrict
mab
snmp trap mac-notification change added
snmp trap mac-notification change removed
dot1x pae authenticator
dot1x timeout tx-period 10
no macro description $TRIGGER
exit
fi
}
int range ##INTERFACE-RANGE##
macro auto processing
Radius Attribute: Cisco-AVPair=auto-smart-port=AP_TRUNK
NEAT
cisp enable
!
template AP_TRUNK
switchport trunk encapsulation dot1q
switchport trunk native vlan 100
switchport mode trunk
Radius Attribute: Cisco-AVPair=interface-template-name=AP_TRUNK
Comparison Smart Port vs. Macro:
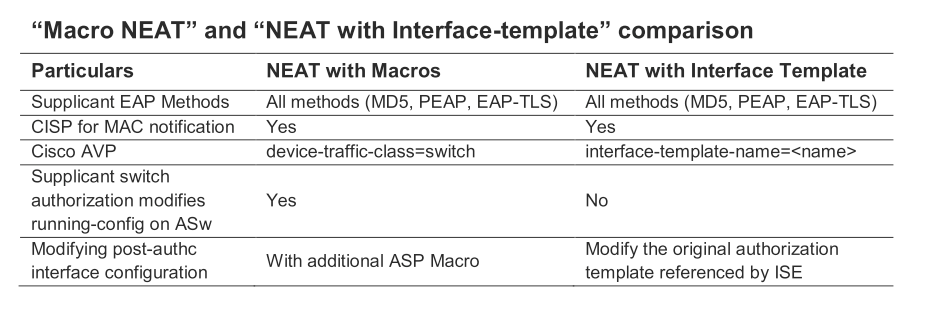
best regards
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-15-2020 06:21 AM
Yes exactly, I use the radius attribute “uto-smart-port=event-trigger” if the mac address is in my Accesspoint End System group.
best regards
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-15-2020 04:48 AM
Hello Michael,
nice to hear that you have found a solution.
Do you tigger the macro with the radius attribute “auto-smart-port=event-trigger from NAC, if a appropriate device is authenticated on the access port?
Or how do you enable a macro on the specific port?
Best regards
Stephan Harrer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-15-2020 04:15 AM
I solved it with macros because NEATis not available on all switches.
Many thanks for your help.
best regards
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-13-2020 01:47 PM
Hello Stefan,
I did a quick web search, too. Here is another description regarding NEAT and templates:
There are some hints in the net about disadvantages concerning the port configuration with NEAT.
for example here: https://community.cisco.com/t5/network-access-control/flexconnect-ap-ise-and-neat/td-p/3302383
It seems that Cisco still has problems to implement a function like "AP Aware" from Extreme.
Best regards
Stephan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-13-2020 01:35 PM
Hello Stefan,
I have searched my knowledge base again.
Maybe a interface template is a good workaround.
https://community.cisco.com/t5/security-documents/neat-with-interface-template/ta-p/3642967
Regards
Stephan
