- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: Cisco Trunk Interface with Extreme NAC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Trunk Interface with Extreme NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-12-2020 07:33 AM
Dear All
I’m trying to enable Extreme NAC for Cisco switches. It works fine for Clients on Access Ports. For Accesspoints (local breakout), I’m trying to get a trunk interface with management vlan untagged and data VLANs tagged.
For XOS Switches, I would create a Role with the needed VLAN Egress config
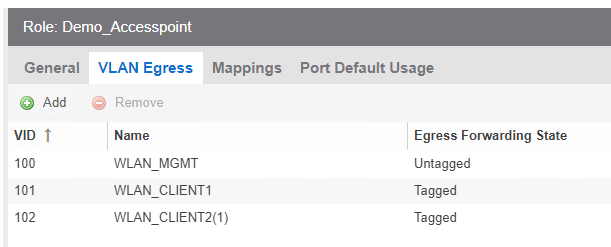
But I cant enforce this role configuration to Cisco switches
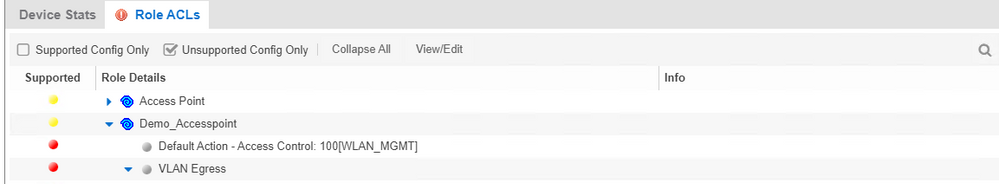
How can I achieve that for Cisco switches with Extreme NAC?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-15-2020 11:53 AM
Hi Miguel
Yes sure, I can share my cisco config. In the meantime, I tested NEAT as well and it seems to be easier than using macro.
Macro
conf t
no macro auto global control device
no macro auto global control trigger
macro auto global processing
macro auto execute AP_TRUNK {
if [[ $LINKUP == YES ]]
then conf t
default interface $INTERFACE
interface $INTERFACE
Description AP_TRUNK
macro description $TRIGGER
switchport trunk allowed vlan ##VLAN-LIST##
switchport trunk native vlan ##VLAN##
switchport mode trunk
spanning-tree portfast trunk
macro auto processing
exit
fi
if [[ $LINKUP == NO ]]
then conf t
default interface $INTERFACE
interface $INTERFACE
description NAC
no switchport trunk allowed vlan
no switchport trunk native vlan
switchport mode access
macro auto processing
authentication control-direction in
authentication event server dead action authorize
authentication event server dead action authorize voice
authentication event server alive action reinitialize
authentication host-mode multi-host
authentication order mab dot1x
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation restrict
mab
snmp trap mac-notification change added
snmp trap mac-notification change removed
dot1x pae authenticator
dot1x timeout tx-period 10
no macro description $TRIGGER
exit
fi
}
int range ##INTERFACE-RANGE##
macro auto processing
Radius Attribute: Cisco-AVPair=auto-smart-port=AP_TRUNK
NEAT
cisp enable
!
template AP_TRUNK
switchport trunk encapsulation dot1q
switchport trunk native vlan 100
switchport mode trunk
Radius Attribute: Cisco-AVPair=interface-template-name=AP_TRUNK
Comparison Smart Port vs. Macro:
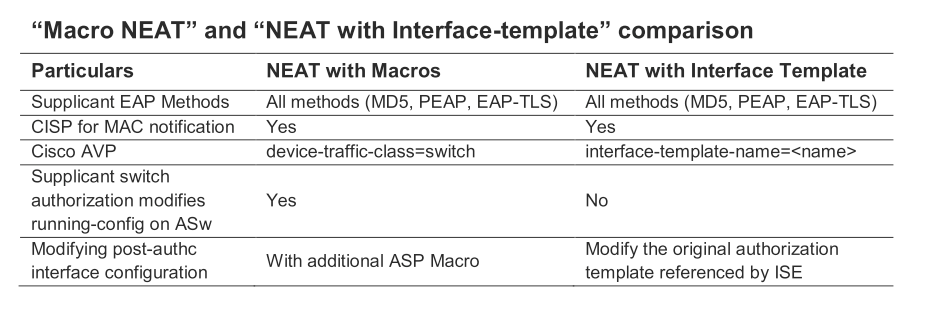
best regards
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-09-2020 12:35 PM
Hi Stephan
It looks like if you use new-style config mode, changing the authentication host-mode is supported via template

Unfortunately, not all of my switches support new-style, so this is not a way for me to go. So I won’t test it.
Up to now i got it working to send both radius attribute (template and smart-port) to the switch. But the switch does not handle both of them
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-05-2020 08:31 AM
Hi Stephan
Yes you’re right, you can’t change the authentication host-mode via port template. But with Macros it works. What I’m trying to do is to do all the needed config via port template and just the changing the authentication host-mode with a macro. But up to now I didn’t get i working to send both Cisco-AVPair attributes via NAC. I’m still on my engineering.
best regards
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-03-2020 07:08 AM
Hello Michael,
how did you solve authentication with neat and Extreme APs?
Normal for an standard port (printer, pc,...) “authentication host-mode multi-auth” is a good choice to authentication every client separatly (if more the one is present).
If you now plug an AP to the port “authentication host-mode multi-host” is a better choice to authenticate only the first device (=AP). All wireless clients are authenticated via the wireless controller.
If you use “multi-auth” with an Access Point on the port you will see every wireless client twice. From WLAN and from LAN.
I hoped there is a way to change the “authentication host-mode “ via the port template but it seems that’s not possible.
How do you handle that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-15-2020 11:53 AM
Hi Miguel
Yes sure, I can share my cisco config. In the meantime, I tested NEAT as well and it seems to be easier than using macro.
Macro
conf t
no macro auto global control device
no macro auto global control trigger
macro auto global processing
macro auto execute AP_TRUNK {
if [[ $LINKUP == YES ]]
then conf t
default interface $INTERFACE
interface $INTERFACE
Description AP_TRUNK
macro description $TRIGGER
switchport trunk allowed vlan ##VLAN-LIST##
switchport trunk native vlan ##VLAN##
switchport mode trunk
spanning-tree portfast trunk
macro auto processing
exit
fi
if [[ $LINKUP == NO ]]
then conf t
default interface $INTERFACE
interface $INTERFACE
description NAC
no switchport trunk allowed vlan
no switchport trunk native vlan
switchport mode access
macro auto processing
authentication control-direction in
authentication event server dead action authorize
authentication event server dead action authorize voice
authentication event server alive action reinitialize
authentication host-mode multi-host
authentication order mab dot1x
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation restrict
mab
snmp trap mac-notification change added
snmp trap mac-notification change removed
dot1x pae authenticator
dot1x timeout tx-period 10
no macro description $TRIGGER
exit
fi
}
int range ##INTERFACE-RANGE##
macro auto processing
Radius Attribute: Cisco-AVPair=auto-smart-port=AP_TRUNK
NEAT
cisp enable
!
template AP_TRUNK
switchport trunk encapsulation dot1q
switchport trunk native vlan 100
switchport mode trunk
Radius Attribute: Cisco-AVPair=interface-template-name=AP_TRUNK
Comparison Smart Port vs. Macro:

best regards
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-15-2020 07:05 AM
Michael,
Could you share the solution?
I’m interested in the config lines for Cisco and the definition of the radius attributes.
Thanks
Mig
