- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: Delete Expired Certificates In NAC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Delete Expired Certificates In NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-22-2019 04:50 PM
Hi,
Working on an issue where NAC is complaining of old expired certificates, so would like to clean these up.
One of the alarms are something along the lines of:
Device: 192.168.60.11
Severity: Critical
Message: AAA Configuration Truststore: Invalid Certificate Found Certificate expired on 2018-11-25 10:53 GMT Alias: 0 Serial Number: 3b 48 6d f7 b6 8d f4 b5 42 f3 90 72 af 49 20 3b CN=xxx-CERTROOTCA01-CA DC=xxx DC=xxx DC=uk CN=xxx-CERTROOTCA01-CA DC=xxx DC=gxxx DC=uk Valid From: 2013-11-25 10:43 GMT Valid Until: 2018-11-25 10:53 GMT RSA (2048 bits) SHA1withRSA
What has been happening is overtime as and when the RADIUS cert has expired, new ones have been updated and the old ones have remained in NAC.
I think the location of the certificate store is at /opt/nac/radius/raddb/certs
When I do an ‘ls’ I see something along the lines of:
drwxr-xr-x 3 root root 4.0K May 3 2019 ./
drwxr-xr-x 8 root root 4.0K Mar 17 2019 ../
-rw-r----- 1 root root 245 Nov 30 2017 dh
-rw-r--r-- 1 root root 14K May 3 2019 external_ca.pem
-rw-r--r-- 1 root root 6.4K Jul 19 2018 external_server.keystore
-rw-r--r-- 1 root root 2.2K Nov 30 2017 external_server.keystore.bak
-rw-r--r-- 1 root root 2.2K Dec 6 2017 external_server.keystore.bak.1
-rw-r--r-- 1 root root 6.4K Jul 19 2018 external_server.keystore.bak.10
-rw-r--r-- 1 root root 6.3K Dec 14 2017 external_server.keystore.bak.2
-rw-r--r-- 1 root root 6.3K Jan 22 2018 external_server.keystore.bak.3
-rw-r--r-- 1 root root 6.3K Feb 20 2018 external_server.keystore.bak.4
-rw-r--r-- 1 root root 6.3K Mar 22 2018 external_server.keystore.bak.5
-rw-r--r-- 1 root root 6.3K Apr 20 2018 external_server.keystore.bak.6
-rw-r--r-- 1 root root 6.3K Jun 1 2018 external_server.keystore.bak.7
-rw-r--r-- 1 root root 6.4K Jun 4 2018 external_server.keystore.bak.8
-rw-r--r-- 1 root root 6.4K Jul 16 2018 external_server.keystore.bak.9
-rw-r--r-- 1 root root 8.7K Jul 19 2018 external_server.pem
-rw-r--r-- 1 root root 14K May 3 2019 external_trust.pem
-rwxr-xr-- 1 root root 2.5K Mar 17 2019 generate_client_cert*
-rwxr-xr-- 1 root root 3.1K Mar 17 2019 generate_server_cert*
-rw-r----- 1 root root 112 Nov 30 2017 index.txt
-rw-r--r-- 1 root root 20 Sep 30 2018 index.txt.attr
-rw-r----- 1 root root 21 Nov 30 2017 index.txt.attr.orig
-rw-r----- 1 root root 0 Nov 30 2017 index.txt.old
-rw-r--r-- 1 root root 4.2K Oct 3 2017 Makefile
-rw-r----- 1 root root 5.0K Mar 17 2019 random
-rw-r--r-- 1 root root 7.7K Oct 3 2017 README
drwxr-xr-x 2 root root 4.0K Nov 30 2017 selfsigned/
-rw-r----- 1 root root 1.6K Nov 30 2017 selfsigned_ca.pem
-rw-r----- 1 root root 3.5K Nov 30 2017 selfsigned_server.pem
-rw-r----- 1 root root 3 Nov 30 2017 serial
-rw-r----- 1 root root 3 Nov 30 2017 serial.old
-rw-r--r-- 1 root root 578 Oct 3 2017 xpextensions
There are several alarms about several certificates that have expired, and have to be careful I don’t remove the current valid certificate that is valid from 2018-07-18 to 2020-07-17.
My assumption here is that the current ‘external_server_keystore’ is perhaps what holds this, and the others maybe old?
I can’t see a way to do it through the GUI, so assume this will have to be done via the shell?
In addition below is a view of the AAA Trusted Certificate:
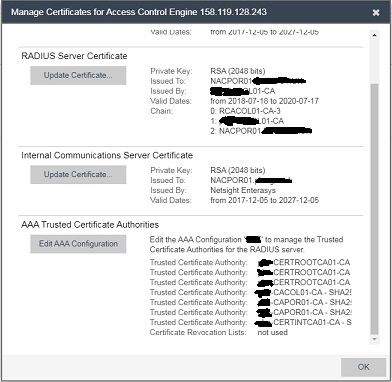
Although I can delete these individual certs from the GUI, I would like to look at the cert to see its details and valid dates before removing to check if its necessary or not.
Any advise much appreciated in advance.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2019 01:36 PM
Hey Martin,
In XMC → Control → Access Control → Engines → Right click a NAC appliance and click “Web View”.
In the browser that pops up click on Diagnostics → Certificate Diagnostics
I believe it will break out the Trusted Root certificates to provide more information about each one.
If you SSH into the NAC box and go into /opt/nac/radius/raddb/certs you can also view them through the openssl application.
openssl x509 -in <certificate> -text
That should display the contents of the certificate. I think that you want to view the “external trust.pem”. To view this file make sure that you escape the space.
openssl x509 -in external\ trust.pem -text
Thanks
-Ryan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-17-2019 08:38 AM
Workaround found.
The repository contained duplicate CA certs that could not be deleted one at a time, but could via the legacy NAC manager.
Currently looking into a bug fix for XMC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-27-2019 11:37 PM
Opened a GTAC case on that last issue, possible bug.
There seems to be a part workaround in that I have to delete two of the certificates together in order to remove it, but again will post back when I’ve got more detail.
Many thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2019 02:39 PM
Hi Ryan,
Thanks for posting back…. slightly annoyed with myself, as should have thought of the webview 🙂
Really appreciate the advise as was stuck.
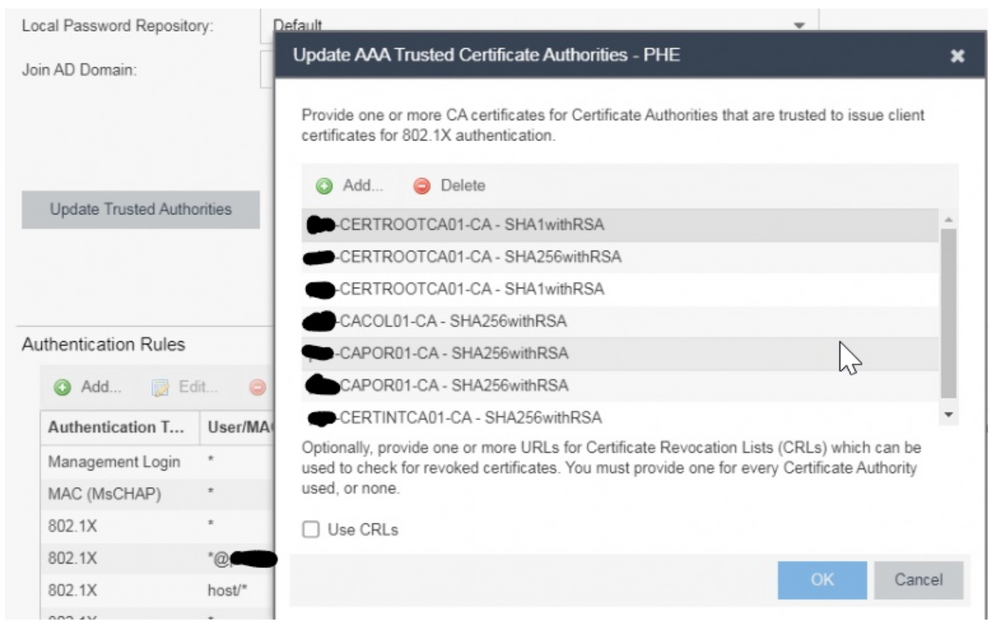
Do have an issue though, in deleting the certificate. See images below:
This shows a list of all the certs:
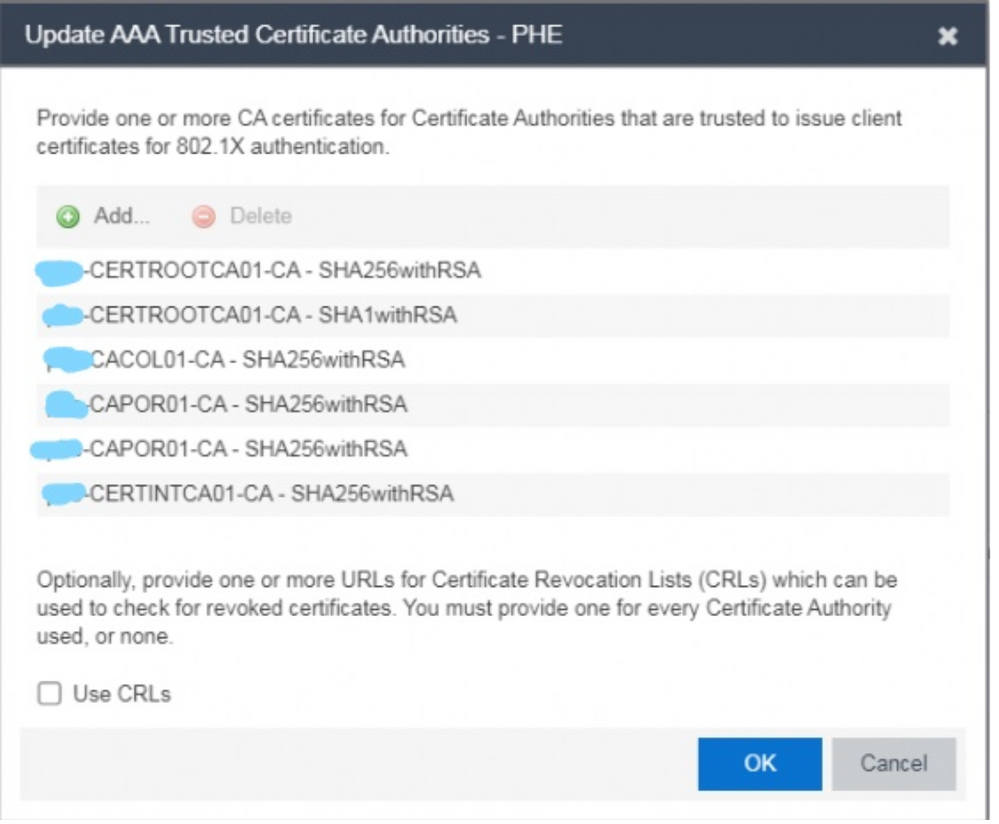
This shows I’ve just deleted the top cert:
When I click ‘OK’, it seems to have added it in again and continuing with ‘Yes’ doesn’t remove the cert:
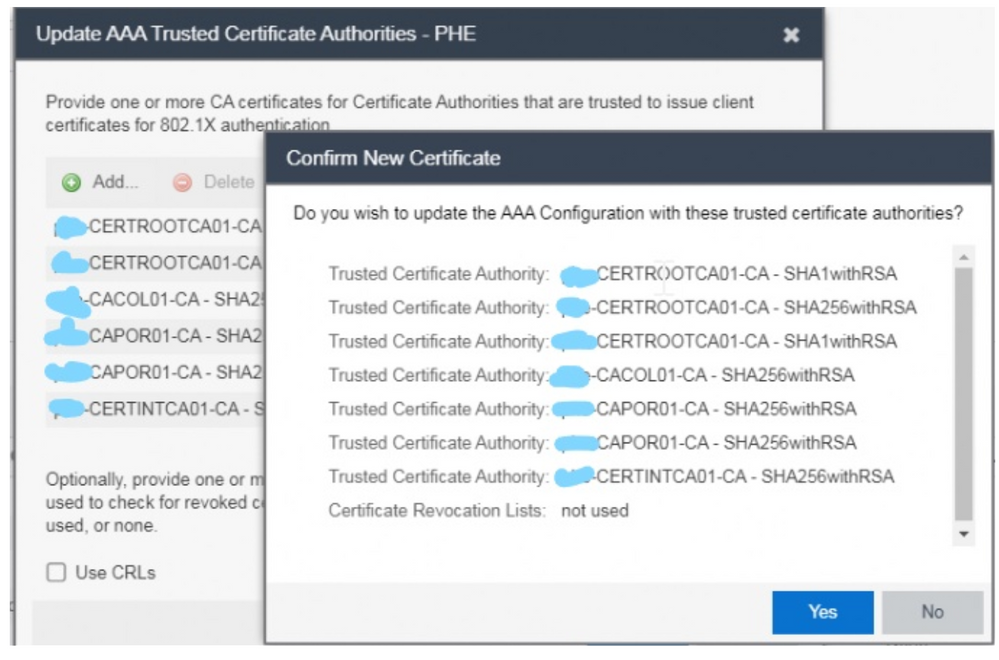
Maybe I’m doing something wrong, but be good to get your opinion.
Many thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-25-2019 01:36 PM
Hey Martin,
In XMC → Control → Access Control → Engines → Right click a NAC appliance and click “Web View”.
In the browser that pops up click on Diagnostics → Certificate Diagnostics
I believe it will break out the Trusted Root certificates to provide more information about each one.
If you SSH into the NAC box and go into /opt/nac/radius/raddb/certs you can also view them through the openssl application.
openssl x509 -in <certificate> -text
That should display the contents of the certificate. I think that you want to view the “external trust.pem”. To view this file make sure that you escape the space.
openssl x509 -in external\ trust.pem -text
Thanks
-Ryan
