- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- How avoid that uplink interface of cisco switch wi...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How avoid that uplink interface of cisco switch with x450-G2 switch fill up the end-system table of my Extreme Control engine with mall mac that ear on the access vlan
How avoid that uplink interface of cisco switch with x450-G2 switch fill up the end-system table of my Extreme Control engine with mall mac that ear on the access vlan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-28-2022 04:12 AM
I've got in my lab an x450-g2 switch and connected to one port of this in trunk mode, there is a cisco switch (on cisco the uplink port is gigabitethernet0/1).
When I connect the cisco to the x450-g2 switch, the end-system table of the control engine, after a while is filled up of entries related to the cisco uplink port as in the screenshot below:
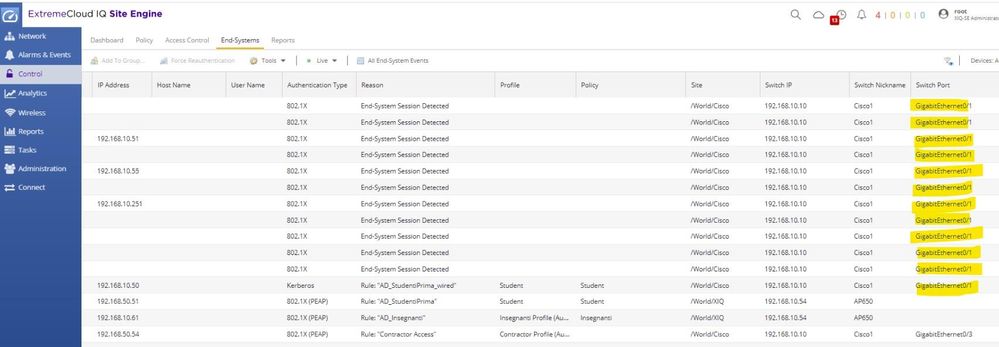
The autentication on cisco is not enable on GigaEthernet0/1 as shown below (is enabled mac an dot1x on all other ports and works when i connect and end-system to the access ports).
How can avoid that uplink port fill up the end-system table of the control engine with all mac address that "ear" on the access vlan?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-26-2022 03:57 PM
I've follow for the cisco configuration the Extreme's document "ExtremeCloud IQ - Site Engine and ExtremeControl – Cisco Switch Integration Guide".
and this guide suggest to use the following setting:
aaa accounting update periodic 5
After contact a local Extreme's SE , he suggests me to remove this line of configuration and now the uplink port messages are no more presents and only the access interfaces authenticate my hosts.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-15-2022 09:21 PM
Hello
Typically "Session Detected" means that we've received a RADIUS accounting packet for that end system.
If you take a tcpdump on control and look for port 1812/1813 can you find any packets for that end system that have the uplink port defined in the RADIUS AVPs?
tcpdump -i eth0 -s 0 -w nactrace.pcap port 1812 or port 1813
Leave it running and have an end system get a few of those "Session Detected" messages.
Once completed search the trace for any RADIUS packets for the affected client.
You can use search filters for calling-station-id which will capture MAB/802.1x authentication, or by username for 802.1x. Once you find packets check the RADIUS AVPs to make sure the uplink isn't there.
Also, I notice that there is a "Kerberos" event. Are you doing any mirroring to get Kerberos traffic to the NAC? NAC can snoop Kerberos packets to get the username, but since you're doing 802.1x NAC can get the username without Kerberos snooping.
You can right click the NAC --> Engine Settings --> Username Resolution --> Disable "Kerberos Username Resolution"
Thanks
-Ryan
