This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: NetSight NAC - rule not working
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NetSight NAC - rule not working
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-14-2019 06:24 PM
We had NAC installed and fully configured for us. We tested on a few machines and everything was fine- in every test scenario the device being tested matched on the expected rule. Vendor is gone and now I'm rolling it out to all of my switches. Most of my computers are registering just fine, however I have a few that are not matching on rules that I expect them to.
When we created the rules, I wanted to ensure no device got blocked so we created a temporary/failsafe "Wired catchall" rule near the bottom of our rules. This rule is configured to accept anything that wasn't caught in the rules above should we experience any 802.1x authentication issues. Which is why I'm here today, I have computers that are failing authentication and are only being allowed by this catchall rule. The goal is to get all devices to match on a rule and delete the catchall, after all the catchall essentially negates the reason for buying NAC. Let me explain our environment/rules.
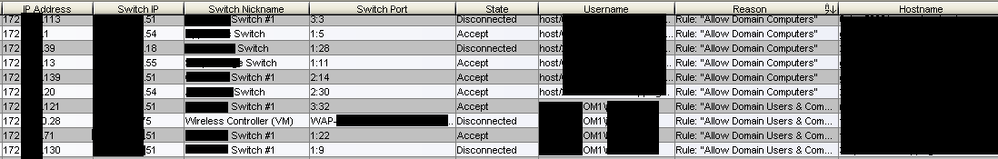
I like to think our NAC is a pretty typical setup. All computers will match on "Allow Domain Computers" and will show up in NAC as "host/%hostname%". When the user logs in it will match on "Allow Domain Users & Computers" and show up in NAC as "DOMAIN\username". See attachment "NAC-Rules.png".
Below is a screenshot of expected behavior:
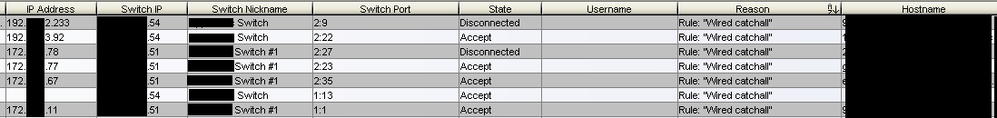
Now I have computers that fail to match on my desired rules and make it all the way down to my "Wired Catchall" rule. One computer I've been experimenting with will not ever match on my aforementioned domain rules and instead goes all the way down to the wired catch all rule.
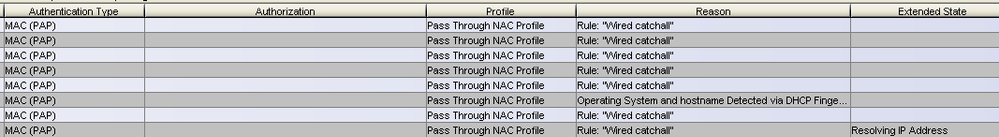
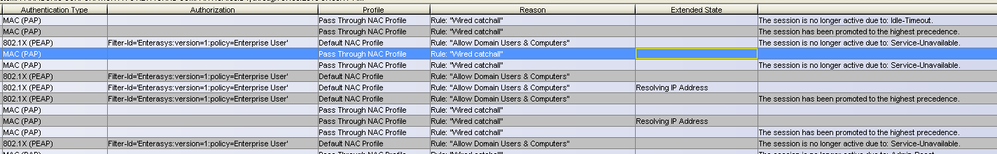
Then I have a computer that is consistently bouncing between different rules- the 3rd screenshot below. Most of the activity occurred in about 11 seconds.
I've noticed all computers that show an authentication type of MAC (PAP) get dropped in the Wired Catchall, and that computers with the authentication type of 802.1x (PEAP) match successfully. While this makes sense to me, I can't figure out why a computer would default to MAC (PAP).
Working with the computer from the middle screenshot above I've checked the following:
Anyone out there willing to take a stab before I take a hammer to these computers? ?
Edit: Switches are Summit X460-G2- all ports are configured identical.
When we created the rules, I wanted to ensure no device got blocked so we created a temporary/failsafe "Wired catchall" rule near the bottom of our rules. This rule is configured to accept anything that wasn't caught in the rules above should we experience any 802.1x authentication issues. Which is why I'm here today, I have computers that are failing authentication and are only being allowed by this catchall rule. The goal is to get all devices to match on a rule and delete the catchall, after all the catchall essentially negates the reason for buying NAC. Let me explain our environment/rules.
I like to think our NAC is a pretty typical setup. All computers will match on "Allow Domain Computers" and will show up in NAC as "host/%hostname%". When the user logs in it will match on "Allow Domain Users & Computers" and show up in NAC as "DOMAIN\username". See attachment "NAC-Rules.png".
Below is a screenshot of expected behavior:
Now I have computers that fail to match on my desired rules and make it all the way down to my "Wired Catchall" rule. One computer I've been experimenting with will not ever match on my aforementioned domain rules and instead goes all the way down to the wired catch all rule.
Then I have a computer that is consistently bouncing between different rules- the 3rd screenshot below. Most of the activity occurred in about 11 seconds.
I've noticed all computers that show an authentication type of MAC (PAP) get dropped in the Wired Catchall, and that computers with the authentication type of 802.1x (PEAP) match successfully. While this makes sense to me, I can't figure out why a computer would default to MAC (PAP).
Working with the computer from the middle screenshot above I've checked the following:
- Ran netsh lan int sh - results show "Connected. Network does not support authentication."
- Updated NIC drivers (Realtek RTL8167) - I have other similar computers that work with the driver used from imaging
- Confirmed NIC has 802.1x enabled, no cert validation, fast reconnect, and authentication mode for user or computer. These settings are being pushed via Group Policy so they're the same on every computer.
- Event Log reports the following:
- - 802.1x = Enabled
- - 802.1x = Not Enforced
- - EAP Type = Microsoft Protected EAP
- - Then "authentication succeeded" but reports it does not support authentication
Anyone out there willing to take a stab before I take a hammer to these computers? ?
Edit: Switches are Summit X460-G2- all ports are configured identical.
Solved! Go to Solution.
1 ACCEPTED SOLUTION
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-16-2019 02:23 PM
Ok. On that screen shot, looks like you are seeing MAC and .1x auth, I don't see timestamps on the screenshot so it is hard to tell the sequence. The device will do both mac and .1x while authenticating, however .1x will take precedence and have final say on the device authentication. MAC is a just a bit faster to auth, so you will see that hit the catch all rule first then .1x will authenticate.
9 REPLIES 9
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-15-2019 08:56 PM
I always wonder, when somebody says "vendor is gone" if it's me .
Does it always fail on the same computers, or is it random? If you do a ldap lookup on the computer, does NAC pull the attributes in? Under the AAA config, ldap config has a test button, from there you can search for that computer, I believe $ should pull it up. Sometimes * will do the trick too.
Does it always fail on the same computers, or is it random? If you do a ldap lookup on the computer, does NAC pull the attributes in? Under the AAA config, ldap config has a test button, from there you can search for that computer, I believe $ should pull it up. Sometimes * will do the trick too.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-15-2019 08:08 PM
Brian,
Thanks for the suggestion- DHCP is updating DNS.
I'm actually glad to see your name popup. I believe you're the one that set this up for us back on December. If so, I'm just now getting around to deploying company-wide.
Thanks for the suggestion- DHCP is updating DNS.
I'm actually glad to see your name popup. I believe you're the one that set this up for us back on December. If so, I'm just now getting around to deploying company-wide.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-15-2019 01:25 PM
I'd look and see if your DNS server has updated info on the computer in question. There are settings in DHCP server options to update DNS when it hands out an IP address. I'd start looking there.
Here is a good article to start looking at. https://gtacknowledge.extremenetworks.com/articles/Solution/NAC-LDAP-Host-Rule-Not-Working-End-Syste...
There are others in GTAC, look for reverse dns lookup in the NAC category.
Hope this helps.
Here is a good article to start looking at. https://gtacknowledge.extremenetworks.com/articles/Solution/NAC-LDAP-Host-Rule-Not-Working-End-Syste...
There are others in GTAC, look for reverse dns lookup in the NAC category.
Hope this helps.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-14-2019 06:58 PM
Rodney,
Here is an expected behavior:
- I'm running 8.1.5.22
- No location groups
Here is an expected behavior:
- PASSED: The Authentication Type of: 802.1X (PEAP) passes the any criteria evaluation.
- PASSED: The Device Type of: MAC Address: XX:XX:XX:7B:03:57, IP Address: 172.xxx.xxx.83, Host Name: %hostname%.%domain% passes the any criteria evaluation.
- PASSED: The User: host/%hostname%.%domain% has LDAP attributes that match the ones defined in LDAP User Group: Domain Computers.
- PASSED: The User: host/%hostname%.%domain% exists in the LDAP database.
- PASSED: The Location of: Switch IP: xxx.xxx.xxx.51, Port Name: 2:26, SSID: null passes the any criteria evaluation.
- PASSED: The Time of: Wednesday, August 14, 2019 1:57:00 PM EDT passes the any criteria evaluation.
- PASSED: The Operating System Name of: Windows 7 SP1 passes the any criteria evaluation.
- PASSED: The Authentication Type of: MAC (PAP) passes the any criteria evaluation.
- PASSED: The Device Type of: MAC Address: XXX:XXX:XXX:7B:04:75, IP Address: 172.xxx.xxx.129, Host Name: %hostname%.%domain% passes the any criteria evaluation.
- FAILED: The User: null does not have LDAP attributes that match the ones defined in LDAP User Group: Domain Computers.
- PASSED: The Authentication Type of: MAC (PAP) passes the any criteria evaluation.
- FAILED: The Host: %hostname%.%domain% does not exist in the LDAP database.
- PASSED: The Authentication Type of: MAC (PAP) passes the any criteria evaluation.
- PASSED: The Device Type of: MAC Address: XX:XX:XX:7B:04:75, IP Address: 172.xxx.xxx.129, Host Name: %hostname%.%domain% passes the any criteria evaluation.
- PASSED: The User Name of: null passes the any criteria evaluation.
- PASSED: The Location of: Switch IP: xxx.xxx.xxx.51, Port Name: 1:42, SSID: null passes the any criteria evaluation.
- PASSED: The Time of: Wednesday, August 14, 2019 9:33:52 AM EDT passes the any criteria evaluation.
- PASSED: The Operating System Name of: Windows 7 SP1 passes the any criteria evaluation.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-14-2019 06:33 PM
A few questions:
1) What version of NAC/XMC is this?
2) The computers that are failing - are location groups involved in the rule you expect them to hit?
We have a configuration/evaluation tool which will tell you WHY we think the authorization is failing.
In the WEB ui, right click on the end system in question in the End System table, choose "Configuration Evaluation Tool" and then run it. On the Authorization tab of the results, you will see why we think it is failing. You can expand the rule section you THINK it should be hitting, and the reason(s) will be outlined as to why it fell through to the next rule.
That should give us an idea of what's going on and why.
1) What version of NAC/XMC is this?
2) The computers that are failing - are location groups involved in the rule you expect them to hit?
We have a configuration/evaluation tool which will tell you WHY we think the authorization is failing.
In the WEB ui, right click on the end system in question in the End System table, choose "Configuration Evaluation Tool" and then run it. On the Authorization tab of the results, you will see why we think it is failing. You can expand the rule section you THINK it should be hitting, and the reason(s) will be outlined as to why it fell through to the next rule.
That should give us an idea of what's going on and why.