This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- RE: Policy to allow only internet access
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Policy to allow only internet access
Policy to allow only internet access
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-11-2017 03:58 PM
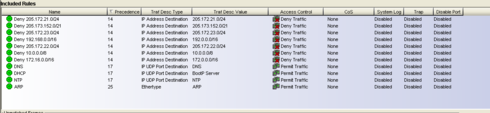
I'm trying to setup a Internet only Policy for wired ports. I've created permit role and added deny destination rules for our local networks. I've also added allow rules for dns, dhcp, etc. It looks like rule precedence is tripping me up as the denys are before the permits so everthing is blocked locally. Is there a way to make rules have different precedence or a diffrent way to do this.
6 REPLIES 6
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-11-2017 04:43 PM
So the Securestacks do not allow re-ordering of the policy. So there is no top->down execution of rules. There is a precedence. So the rules that are most complex (like your top rules with /24 bit masks, should hit first, and then your simplest ones (like ARP ethertype) should be hit last.
I think another approach to it is to look at the Unregistered Rule set that is part of the default policy domain. It effectively allows minimal traffic to talk to a NAC and get an IP address and do DNS, but no IP traffic (because the default policy is to Deny traffic). It may be a good model to work from.
I think another approach to it is to look at the Unregistered Rule set that is part of the default policy domain. It effectively allows minimal traffic to talk to a NAC and get an IP address and do DNS, but no IP traffic (because the default policy is to Deny traffic). It may be a good model to work from.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-11-2017 04:34 PM
You could always start with a deny all rule and permit only what you need.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-11-2017 04:34 PM
I guess I could do a deny all and then permit all public IP networks. That gets to be a crazy long list of permit rules as I would need to allow the following. Anyone know what the max number of rules are on the b-series?
1.0.0.0/8
2.0.0.0/7
4.0.0.0/6
8.0.0.0/7
11.0.0.0/8
12.0.0.0/6
16.0.0.0/4
32.0.0.0/3
64.0.0.0/2
139.0.0.0/8
140.0.0.0/6
144.0.0.0/4
160.0.0.0/5
168.0.0.0/6
172.0.0.0/12
172.32.0.0/11
172.64.0.0/10
172.128.0.0/9
173.0.0.0/8
174.0.0.0/7
176.0.0.0/4
192.0.0.0/9
192.128.0.0/11
192.160.0.0/13
192.169.0.0/16
192.170.0.0/15
192.172.0.0/14
192.176.0.0/12
192.192.0.0/10
193.0.0.0/8
194.0.0.0/7
196.0.0.0/6
200.0.0.0/6
204.0.0.0/8
205.0.0.0/9
205.128.0.0/11
205.160.0.0/13
205.168.0.0/14
205.172.0.0/20
205.172.16.0/22
205.172.24.0/21
205.172.32.0/19
205.172.64.0/18
205.172.128.0/17
205.173.0.0/17
205.173.128.0/20
205.173.144.0/21
205.173.160.0/19
205.173.192.0/18
205.174.0.0/15
205.176.0.0/12
205.192.0.0/10
206.0.0.0/7
208.0.0.0/4
1.0.0.0/8
2.0.0.0/7
4.0.0.0/6
8.0.0.0/7
11.0.0.0/8
12.0.0.0/6
16.0.0.0/4
32.0.0.0/3
64.0.0.0/2
139.0.0.0/8
140.0.0.0/6
144.0.0.0/4
160.0.0.0/5
168.0.0.0/6
172.0.0.0/12
172.32.0.0/11
172.64.0.0/10
172.128.0.0/9
173.0.0.0/8
174.0.0.0/7
176.0.0.0/4
192.0.0.0/9
192.128.0.0/11
192.160.0.0/13
192.169.0.0/16
192.170.0.0/15
192.172.0.0/14
192.176.0.0/12
192.192.0.0/10
193.0.0.0/8
194.0.0.0/7
196.0.0.0/6
200.0.0.0/6
204.0.0.0/8
205.0.0.0/9
205.128.0.0/11
205.160.0.0/13
205.168.0.0/14
205.172.0.0/20
205.172.16.0/22
205.172.24.0/21
205.172.32.0/19
205.172.64.0/18
205.172.128.0/17
205.173.0.0/17
205.173.128.0/20
205.173.144.0/21
205.173.160.0/19
205.173.192.0/18
205.174.0.0/15
205.176.0.0/12
205.192.0.0/10
206.0.0.0/7
208.0.0.0/4
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-11-2017 04:34 PM
Ya I was trying to think of a good way to do it in the opposite direction but couldn't figure out how that would look.