- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: XIQ-SE Authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
XIQ-SE Authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-08-2024 11:04 AM
Hi!
I'm trying to configure a MS NPS server to act as RADIUS server authenticator for XIQ-SE login.
I've managed to do it, but whenever there's a user who has never logged in before (or that it hasn't been manually created and added to an Authorization Group) it just keeps asking for credentials and never logs in.
I know there must be some "Automatic Membership Criteria" defined, but I cannot find any examples on how to do it, specifically when using RADIUS.
I've captured the RADIUS packets and saw that I got authorized. I also saw on XIQ-SE Event log a "No Group for User" event - "Unable to find dynamic group for user XPTO using RADIUS configuration".
On the reply RADIUS packets I see that there are no VSA's sent back and that's normal because I haven't configured them as I don't know if they are required... Is this the way to go? Any documentation on what VSA to use?
Any help on achieving this?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-09-2024 12:54 AM
Hi Tiago,
I did this using ExtremeControl, but it should work also for any third party radius server.
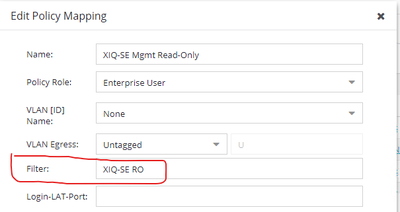
I configured a Filter-Id in the automatic Membership criteria, for example:
My ExtremeControl rule then has this filter configured:
I have some other rules that return another Filter-Id that is used for other groups.
Hope that helps a bit.
Best regards
Stefan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-09-2024 12:54 AM
Hi Tiago,
I did this using ExtremeControl, but it should work also for any third party radius server.
I configured a Filter-Id in the automatic Membership criteria, for example:
My ExtremeControl rule then has this filter configured:
I have some other rules that return another Filter-Id that is used for other groups.
Hope that helps a bit.
Best regards
Stefan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-09-2024 01:25 AM
I also thought something link this could be a solution. I can even use other random VSAs... I'll try to go that way and test it.
Still if there is a manufacturer recomended way to do this would be great!
Thanks Stefan!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-09-2024 01:57 AM
I've already tested using the Filter-ID and it worked perfectly!
I still don't know if this is the recomended way to do it, but it sure works as expected.
Maybe this can be a good add to the official documentation that tends to take you in a direction that will not work if you choose RADIUS as the protocol to use. If you decide to use LDAP it makes sense to use the OU=CN notation, but if you choose RADIUS that's not the way to go because the RADIUS server will not send those attributes automatically...
Thanks again Stefan!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-09-2024 02:00 AM
Great to hear!
It's the recommended way, I once was in contact with GTAC regarding this topic.