This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- Assigning two vlans to X440-port via 802.1X and Wi...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Assigning two vlans to X440-port via 802.1X and Windows NPS
Assigning two vlans to X440-port via 802.1X and Windows NPS
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-10-2019 07:48 AM
Hi,
I am currently configuring configuring 802.1X on all of our Switches. We have Cisco IP-phones and Desktop PCs that are connected via the phone to to the switch. The ports should be set to the voice vlan tagged and the production vlan untagged.
The problem i have is, that only the last entry on the NPS gets set on the port, and not both.
So in this case, Production gets assigned on the Port, but i actually want both options set. Does anyone have experiences with this and is there a way to solve this?
Thanks in advance!
I am currently configuring configuring 802.1X on all of our Switches. We have Cisco IP-phones and Desktop PCs that are connected via the phone to to the switch. The ports should be set to the voice vlan tagged and the production vlan untagged.
The problem i have is, that only the last entry on the NPS gets set on the port, and not both.
So in this case, Production gets assigned on the Port, but i actually want both options set. Does anyone have experiences with this and is there a way to solve this?
Thanks in advance!
5 REPLIES 5
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-10-2019 02:55 PM
From my experience most configure it to put the phone in a untagged VLAN and the PC as tagged but I don't see a problem to tag both.
You'd use whatever 802.1X auth the phone support, state of the art phones should support a lot of different methods e.g. PEAP, EAP-TLS.
In case nothing is supported you'd end up with just MAC auth..
-Ron
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-10-2019 08:49 AM
code:
create vlan nt_login
configure netlogin vlan nt_login
enable netlogin dot1x
enable netlogin ports 10 dot1x
configure radius netlogin primary server "server" client-ip "client" vr "VR-Default"
configure radius netlogin primary shared-secret ****
enable radius netlogin
I think currently only port-based-vlans is configured, i just used port10 as my testing port.
My first idea was to just authenticate the PC and then set the port to vlan VOIP and Production so PC and Phone is allowed. But by reading trough this, i think i need to authenticate the PC and the Phone and use both tagged? Or am i wrong.
edit:
I think i understand what mac-based-vlan does, but how does the authentication side on NPS work, because i want to authenticate the PC via Username or Certificate. And how do i do the phones?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-10-2019 08:47 AM
I think you should try Ron's suggestions as well.
Yet still working, VSA-based VLAN assignment is not used today I believe, depends on what version of EXOS do you use.
Kind regards,
Tomasz
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-10-2019 08:41 AM
(oh you removed your reply)
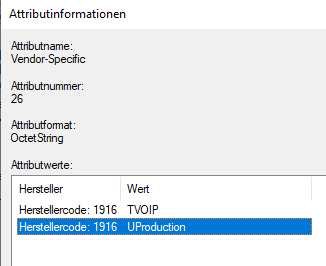
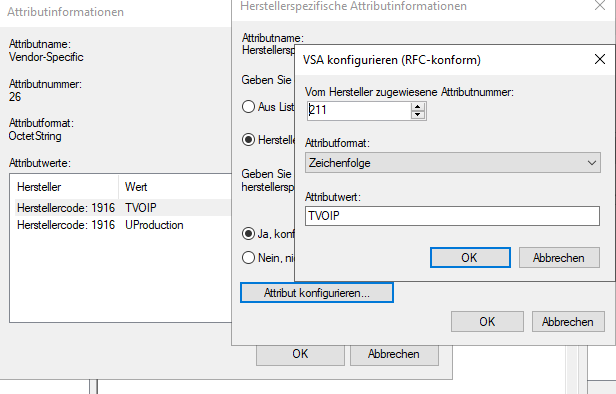
ID 26 is not a VSA, i think 26 is just something NPS specific:
I followed this guide and prepending T or U in front of the VLAN differentiates between tagged, untagged:
https://gtacknowledge.extremenetworks.com/articles/How_To/How-to-configure-802-1x-based-Netlogin-with-Radius-on-EXOS
I will try out RFC3580-based Tunnels now and see if that works.