This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: Best way to connect access with distribution w...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Best way to connect access with distribution with limited options
Best way to connect access with distribution with limited options
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-10-2015 05:02 AM
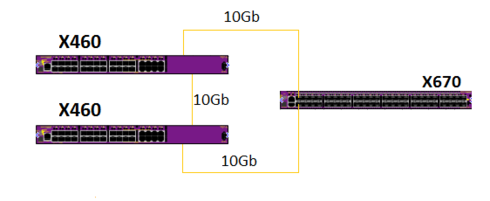
Hello, Community! Thinking what would be the most effective way to connect the devices shown in the below topology (two X460s in the access layer connecting to one X670 in the distribution).
1. One approach would be to interconnect them via EAPS domain. However, if this would scale of up to 20 domains on the X670 (up to 40 access layer switches), wouldn't that make some operating / managing issues ?
2. Other option - stacking the X460s in the daisy chain (only option because of the 10Gb uplinks) is not recommended, because the loss of the link between them makes for all sorts of troubles (double masters, etc.).
3. Maybe you would recommend some other solution that would be more resilient and scallable ?
1. One approach would be to interconnect them via EAPS domain. However, if this would scale of up to 20 domains on the X670 (up to 40 access layer switches), wouldn't that make some operating / managing issues ?
2. Other option - stacking the X460s in the daisy chain (only option because of the 10Gb uplinks) is not recommended, because the loss of the link between them makes for all sorts of troubles (double masters, etc.).
3. Maybe you would recommend some other solution that would be more resilient and scallable ?
6 REPLIES 6
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-11-2015 04:17 PM
I think we will be going with the EAPS. Thanks for the opinions, guys!
Daniel,
I'm aware and couldn't agree more with you regarding the single point of failure in the core. The intended topology was fully redundant. However, due to some reasons the client chose to split the architecture. We made sure that they're fully aware of the situation and potential consequences and i'm trying to make the most with what we have.
Daniel,
I'm aware and couldn't agree more with you regarding the single point of failure in the core. The intended topology was fully redundant. However, due to some reasons the client chose to split the architecture. We made sure that they're fully aware of the situation and potential consequences and i'm trying to make the most with what we have.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-11-2015 10:06 AM
Exit,
Any and all alternatives mentioned suffer the same BIG problem. A single X670 connecting 40 X460 to the rest of the network is a HUGE single point of failure.
I would add a second X670, configure MLAG and dual home each X460 through their 10G ports.
Any and all alternatives mentioned suffer the same BIG problem. A single X670 connecting 40 X460 to the rest of the network is a HUGE single point of failure.
I would add a second X670, configure MLAG and dual home each X460 through their 10G ports.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-10-2015 05:05 PM
I prefer to have option 1, maybe with some optimization of X460 number in each domain if possible.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-10-2015 09:56 AM
About M-LAG good redundancy you can see here - https://community.extremenetworks.com/extreme/topics/summitstack_and_lag_in_m_lag
About 20 EAPS domains - Summit series switches have limitation up to 32 EAPS domains (you can look this limit in RelNotes for EXOS).
About 20 EAPS domains - Summit series switches have limitation up to 32 EAPS domains (you can look this limit in RelNotes for EXOS).