- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: Floating Default Route vs Flow Redirect
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Floating Default Route vs Flow Redirect
Floating Default Route vs Flow Redirect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-23-2017 08:31 AM
Hi,
Currently working on integrating a legacy Cisco network with Extreme, where the default route for the interim is to send all traffic into the legacy Cisco network.
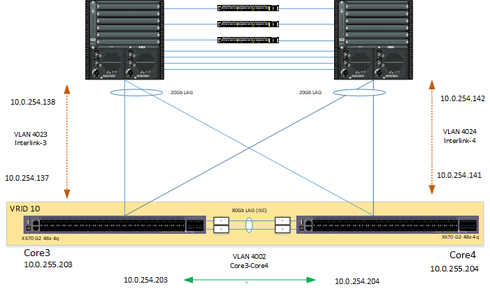
This is to be configured via static routing, due to problems in the legacy network enabling a common routing protocol. Below is an example of what the network interconnections will look like:
The two Extreme Switches are using MLAG, common VRRP between them for each of the VLANs with Fabric routing mode enabled, and OSPF also enable across the two.
So in the scenario I would like both cores to route all traffic to the first Cisco core, should that fail all traffic to be routed to the other core.
Have been looking at both these articles:
https://extremeportal.force.com/ExtrArticleDetail?an=000083175
https://extremeportal.force.com/ExtrArticleDetail?an=000083436
The new network is all on 10.x.x.x/8, everything else is to go to the legacy network.
Was exploring implementing something like the following:
create flow-redirect core3-redirect
configure flow-redirect core3-redirect add nexthop 10.0.254.204 priority 100
configure flow-redirect core3-redirect add nexthop 10.0.254.138 priority 200
edit policy ACL_redirect
Entry redirect {
If match all {
source-address 10.0.0.0/8;
} then {
permit;
redirect-name core3-redirect;
}
}
configure access-list ACL_redirect ports x ingress
---------------
create flow-redirect core4-redirect
configure flow-redirect core4-redirect add nexthop 10.0.254.142 priority 100
configure flow-redirect core4-redirect add nexthop 10.0.254.203 priority 200
edit policy ACL_redirect
Entry redirect {
If match all {
source-address 10.0.0.0/8;
} then {
permit;
redirect-name core4-redirect;
}
}
configure access-list ACL_redirect ports x ingress
--------------
Not sure if this is the best way to do it, perhaps using the following instead?:
configure iproute priority static [11-65534]
Also, should I use flow-redirect I would probably have to apply the ACL to all ports bar the ISC link and interlinks to legacy network?
Will have to give the same consideration on the legacy side to stop any asymmetric routing, so if you also have any ideas around that?
Many thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-23-2017 09:00 AM
Your above redirect is missing the health-check by ping/arp.
You are doing what Cisco is doing on their PBR with IP SLA monitoring the next-hop.
You can search the EXOS user-guide on ""Policy-based redirection redundancy"
The above will be doing the things right. But it will be complex, messy and complicated.
mVRRY or mHSRP will solve the common problem of load-sharing on FHRP (First-Hop Redundancy Protocol) in the first place for outgoing traffic.
Good Luck.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-23-2017 09:00 AM
Thanks for replying, I hadn't considered this but one of the reasons for using default routes is the legacy Cisco network is old, end of life and deemed very unstable, so a minimum and simple as possible configuration work is to be considered for the integration.
So although this might be a good idea, I can't use it in this example.
My Cisco knowledge being a little out dated now, they are currently using HSRP and a presume utilising this method could take some extensive'ish configuration work?
Any other ways of doing it?
Just need to way up all my options and consider which is best really.
Many thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-23-2017 08:49 AM
VRRP is a well known standard and can coexists between different vendors. The only thing to note the multicast hello which is tied to VRRP ID. So make sure no conflict there.