This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- Help to determine the most suitable STP type for m...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Help to determine the most suitable STP type for my configuration
Help to determine the most suitable STP type for my configuration
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-19-2016 06:36 AM
Hello, everybody!
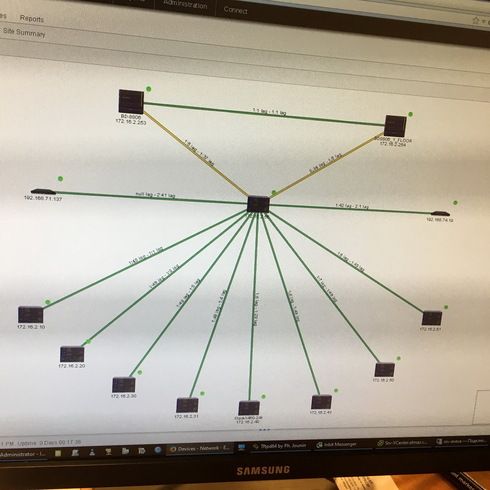
I have a network, where only Extremes exist.
Access layer are 8 stacks spread through floors.
Distribution layer is a stack of 2 X670.
Core layer are two BD8806 connected with MLAG. There is also VRRP configured.
There is one etherchannel between core for MLAG, and one etherchannel to X670 stack.
Floor stacks are connected to X670 with one etherchannel link.
I have 30 vlans total.
The schema is provided below.
Could you please help me to find the most suitable STP type/configuration?
At the moment I have configured EMISTP encapsulation with dot1w mode, but I don't like it.
Many thanks in advance,
Ilya
P.S. With this scheme I have strange alternating ping replies from 1 to 50 ms. Is there any connection with STPDs or VRRP in the core?
P.P.S Could you give me a link to any article where the simplest STP configuration on extremes described? I am interested in the method of configuring STP for all vlans with minimum efforts like in CISCO.
I have a network, where only Extremes exist.
Access layer are 8 stacks spread through floors.
Distribution layer is a stack of 2 X670.
Core layer are two BD8806 connected with MLAG. There is also VRRP configured.
There is one etherchannel between core for MLAG, and one etherchannel to X670 stack.
Floor stacks are connected to X670 with one etherchannel link.
I have 30 vlans total.
The schema is provided below.
Could you please help me to find the most suitable STP type/configuration?
At the moment I have configured EMISTP encapsulation with dot1w mode, but I don't like it.
Many thanks in advance,
Ilya
P.S. With this scheme I have strange alternating ping replies from 1 to 50 ms. Is there any connection with STPDs or VRRP in the core?
P.P.S Could you give me a link to any article where the simplest STP configuration on extremes described? I am interested in the method of configuring STP for all vlans with minimum efforts like in CISCO.
18 REPLIES 18
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-20-2016 04:23 PM
One other thing you can do that is also a great alarm generator and protection on edge access ports. Enable rate shaping. you have three options... broadcast, mcast, and unknown mac address packets per second. This is fully configurable .. We only do broadcast and set it to 200 pps. If someone plugs a dumb switch in a loops it on their side this simple configuration will limit the amount of broadcast packets coming from them and send you monitoring system and nice trap. Good luck
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-20-2016 05:30 AM
David, I wish you the luck!)
Thank you!
Thank you!
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-19-2016 07:03 PM
I have not tested it but I don't think you can name a VLAN elrp, I think it is "protected" which could be why we use "noloop"
You can turn elrp on for the distribution layer, I think were where all just advising against letting it disable ports that will take down entire switches.
We don't use stp at all, but its your network......
Orlando sounds fun but boss would have to send me. Wish me luck on that one.
Thanks,
You can turn elrp on for the distribution layer, I think were where all just advising against letting it disable ports that will take down entire switches.
We don't use stp at all, but its your network......
Orlando sounds fun but boss would have to send me. Wish me luck on that one.
Thanks,
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-19-2016 04:28 PM
Guys... Did I get it right...? To protect access ports against loops I have to add to all of them special technical VLAN as tagged. Then turn on the mysterious ELRP. Associate it with the VLAN. In case of a loop ELRP have to detect on a certain port BPDUs from current switch (from himself) and block the port, yes? Permanent or for period of time...
Would this conf be ok?
create vlan ELRP tag 4094
conf vlan ELRP add ports all tag
enable elrp-client
configure elrp-client disable-ports exclude 49,50 (these are uplinks)
configure elrp-client periodic "ELRP" ports all log disable-port duration 60
Why shouldn't I turn on the same feature at distribution layer on X670?
To be honest I scrating my head over whether is it safe to completely remove STPDs from core and distribution? Still thinking...
Many thanks to you!
P.S. Will you attend annual summit in Orlando?)
Would this conf be ok?
create vlan ELRP tag 4094
conf vlan ELRP add ports all tag
enable elrp-client
configure elrp-client disable-ports exclude 49,50 (these are uplinks)
configure elrp-client periodic "ELRP" ports all log disable-port duration 60
Why shouldn't I turn on the same feature at distribution layer on X670?
To be honest I scrating my head over whether is it safe to completely remove STPDs from core and distribution? Still thinking...
Many thanks to you!
P.S. Will you attend annual summit in Orlando?)