- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: How should configuration for multiple 802.1x s...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How should configuration for multiple 802.1x sesions look like on x440?
How should configuration for multiple 802.1x sesions look like on x440?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-17-2021 08:31 AM
Hi
I need to configure switch port for AP. On AP i will broadcast wireless network based on 802.1x authentication.
probably i shud see multiple user netlogin sesions on that port. Now what i see is onlu 1 policy applied for accesspoint and meny sesions whitout any policy applied.
it look like that:
test-switch-11.15 # sh netlog session por 3
Multiple authentication session entries
---------------------------------------
Port : 3 Station address : 00:dc:b2:39:d4:12
Auth status : failed Last attempt : Fri Dec 17 13:03:41 2021
Agent type : dot1x Session applied : false
Server type : radius VLAN-Tunnel-Attr : None
Policy index : 0 Policy name : No Policy applied
Session timeout : 0 Session duration : 0:00:00
Idle timeout : 300 Idle time : 0:00:00
Auth-Override : disabled Termination time : Not Terminated
Port : 3 Station address : 00:dc:b2:39:d4:12
Auth status : success Last attempt : Fri Dec 17 12:57:51 2021
Agent type : mac Session applied : true
Server type : radius VLAN-Tunnel-Attr : None
Policy index : 33 Policy name : 0-ACCESSPOINT Auth (active)
Session timeout : 0 Session duration : 1:14:18
Idle timeout : 300 Idle time : 0:00:00
Auth-Override : disabled Termination time : Not Terminated
Port : 3 Station address : 4c:eb:42:e8:af:e9
Auth status : failed Last attempt : Fri Dec 17 12:27:50 2021
Agent type : dot1x Session applied : false
Server type : radius VLAN-Tunnel-Attr : None
Policy index : 0 Policy name : No Policy applied
Session timeout : 0 Session duration : 0:00:00
Idle timeout : 300 Idle time : 0:00:00
Auth-Override : disabled Termination time : Not Terminated
Accesspoint is autenticated by MAC and applied role contains one nativ vlan for AP management and multiple egress vlans.
Additionally when im connecting to wireless network im reciveing proper role on AP whitch my Xtreme Campus controler apply to that connection - but when im looking at Xtreme Network Management End systems it looks like after few minutes my session was deautenticated by switch
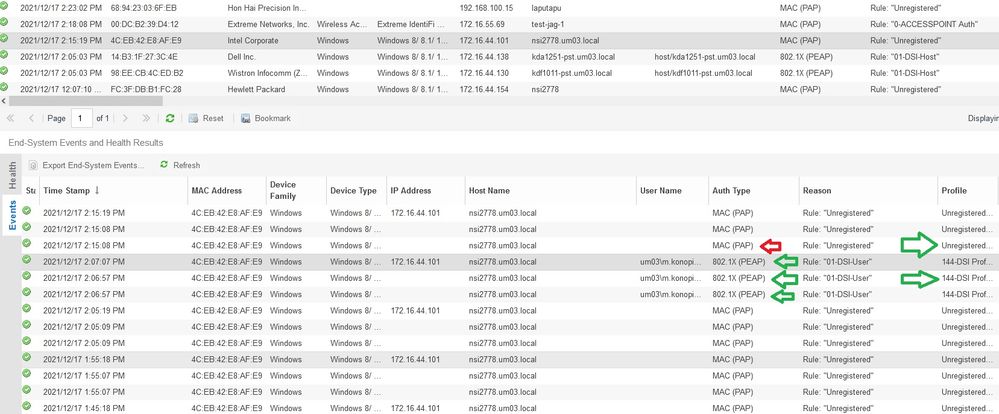
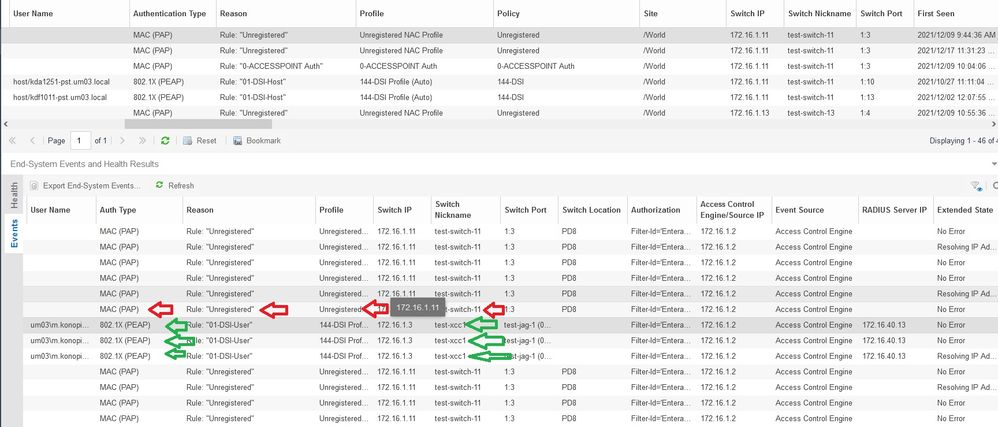
I dont know how to fix it to make 802.1x stable and autenticate user only by it
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-18-2021 05:57 PM
How did you learn the mac addresses on the switch when you had AP Aware disabled?
------------------------------
- Ronald
------------------------------
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-19-2021 01:40 PM
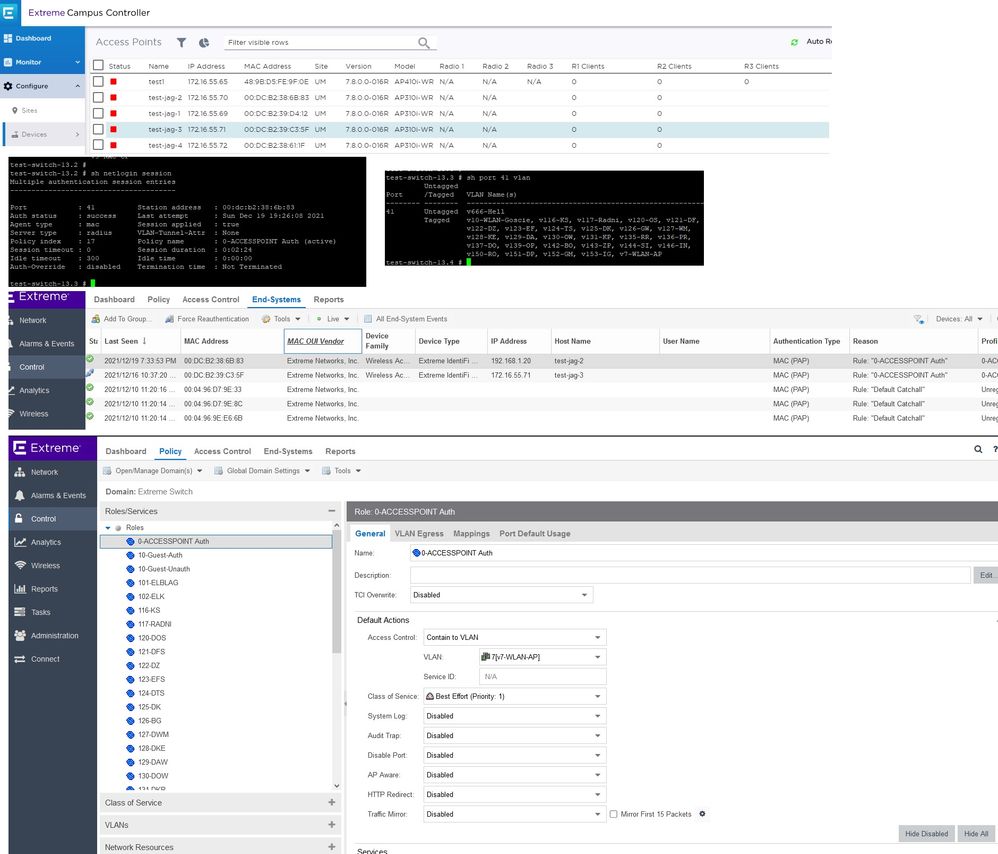 This is my configuration and somehow it stopped work properly
This is my configuration and somehow it stopped work properly- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-19-2021 02:31 PM
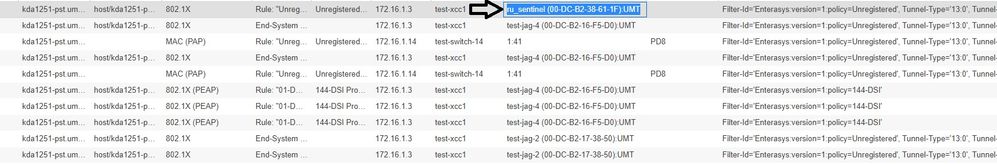
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-19-2021 03:06 PM
OK ive got it.
AP Aware - disabled
on switch - conf netlo idle 0
on switch - ports restarted - and sesion is stable - users stays in proper group 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-20-2021 02:55 AM
better way to send Idle-Timeout attribute (IMO) is to do like in link below
https://extremeportal.force.com/ExtrArticleDetail?an=000079217
by creating new profile od "Radius attributes to send" by copy them from "RFC 3580 - VLAN and Extreme Policy" and adding last line "idle-timeout"
Filter-Id=Enterasys:version=1:%MANAGEMENT%policy=%POLICY_NAME%
Service-Type=%MGMT_SERV_TYPE%
Tunnel-Private-Group-Id=%VLAN_ID%:%VLAN_TUNNEL_TAG%
Tunnel-Type=13:%VLAN_TUNNEL_TAG%
Tunnel-Medium-Type=6:%VLAN_TUNNEL_TAG%
Idle-Timeout=%CUSTOM4%
after that i modiefied custom 4 field by writing "0" only
somehow editing policy mapping custom 4 attribute by placing there "idle-timeout=0" didnt work on every switch - i dont know why
