- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- Re: RE: How to create routed GRE Tunnel from X450G...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to create routed GRE Tunnel from X450G2 to Cisco Router?
How to create routed GRE Tunnel from X450G2 to Cisco Router?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-12-2018 03:32 PM
For proof of concept I am doing my testing on a spare X450G2 running the same 22.5.1.7 code but just the regular edge licence. I have the tunnel created and I can ping the endpoints which are the local and remote LTE router. But the provider of these LTE routers require us to create a GRE tunnel over them.
I created the tunnel on the HQ side which terminates into a Cisco 2901 router with this command:
interface Tunnel5
description LTE TUNNEL TO R BRANCH
ip address 192.168.205.33 255.255.255.252
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source 10.200.0.1
tunnel destination 10.200.0.22
end
The LTE router at this HQ site is 10.200.0.1, and the LTE router at the "R Branch" we will call it, is 10.200.0.22. This Cisco Router can ping 10.200.0.22 without issue. The Extreme test switch can ping 10.200.0.1 without issue, so I know there is LTE connectivity.
Now for creating the GRE tunnels, this Cisco commands above work fine for our other branches that terminate into other Cisco 2901 routers. However this new site does not have any Cisco routers since we are doing routing in the switch.
Here is what I've attempted on the EXOS side for the tunnel:
Tunnel is plugged into port 2
sh port 2 vid
Untagged
Port /Tagged VID(s)
-------- -------- ------------------------------------------------------------
2 Untagged 222
sh vlan
Untagged ports auto-move: Inform
-----------------------------------------------------------------------------------------------
Name VID Protocol Addr Flags Proto Ports Virtual
Active router
/Total
-----------------------------------------------------------------------------------------------
Default 1 10.1.0.111 /16 -f----------T--------------- ANY 1 /26 VR-Default
Mgmt 4095 ------------------------------------------------ ANY 0 /1 VR-Mgmt
LTE 222 10.200.0.21 /30 -f-------------------------- ANY 1 /1 VR-Default
Other vlans excluded from this output...
create tunnel backuptunnel gre destination 10.200.0.22 source 10.200.0.21
configure tunnel backuptunnel ipaddress 192.168.205.34 255.255.255.252
enable ipforwarding tunnel backuptunnel
enable ipforwarding vlan LTE
sh iproute
Ori Destination Gateway Mtr Flags VLAN Duration
#s Default Route 10.1.0.254 1 UG---S-um--f- Default 100d:22h:32m:2s
#d 10.1.0.0/16 10.1.0.111 1 U------um--f- Default 100d:22h:32m:4s
#s 10.200.0.0/24 10.200.0.22 1 UG---S-um--f- LTE 0d:0h:19m:28s
#d 10.200.0.20/30 10.200.0.21 1 U------um--f- LTE 0d:1h:2m:17s
#s 192.168.205.0/24 192.168.205.33 1 UG---S-um--f- backuptunnel 0d:0h:25m:23s
#d 192.168.205.32/30 192.168.205.34 1 U------um--f- backuptunnel 0d:0h:40m:38s
I am expecting that this EXOS switch, 192.168.205.34 should be able to ping the Cisco side of the tunnel at 192.168.205.33, and the Cisco side should be able to ping the EXOS side as well. However the ping is failing.
Obviously the endpoints will be 192.168.205.33 at the branch and 192.168.205.34 at the HQ and we will push traffic over this if the primary WAN goes down (likely using OSPF).
Am I missing something, or did I configure something wrong?
Again this is just a test switch so we can do antying on it and not disrupt connectivity. But once I get it working I want to translate this config to the actual branch and drive the LTE device over there and plug it into port 2:49 (with gigabit SFP port). Port 1:49 is the current WAN handoff in its own transport vlan. The site has no connectivity issues today, but we want to throw in this LTE backup device just in case there is a fiber cut or other issue with our upstream provider. We have this configuration today with other sites, but all of those existing sites use either a Cisco 2901 or 2911 router. We are trying to eliminate that extra piece of equipment if at all possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-02-2022 04:20 AM
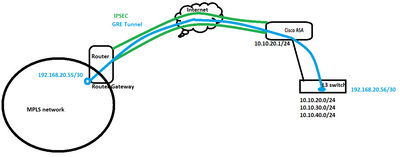
@kjstech - running into the same case as of today,
I have an Extreme L3 switch that need to establish a GRE tunnel with a Cisco router from the ISP side,
but the additional thing here is an IPSEC VPn between an ASA and the same Cisco router to secure the GRE tunnel, the IP I've put is the only thing I have, any suggestion please for the Extreme switch configuration?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-02-2022 06:01 AM
While we got point to point connectivity, we abandoned this a long time ago because at the time (not sure if this is still the case in newer firmwares) - we couldn’t include the GRE tunnel interface in OSPF calculation on the extreme side. We always had to just OSPF to another device that DOES have that capeability, such as a Cisco Router, Server running pfsense with the frr plugin, or Ubiquiti EdgeRouter.
We ended up canceling our LTE backup (too slow and too much latency) and moved to cable modem. Now we OSPF with a higher cost to a pfsense box which establishes IPSEC tunnel over a cable modem to another pfsense box at our HQ.
The local carriers private fiber metro Ethernet is a lower cost route but if it’s cut, OSPF re-converges over to pfsense, out a IPsec tunnel to HQ, then OSPF back into an extreme core.
Overall this back up solution works much faster and the bandwidth with this far greater than a previous LTE solution we were using. Plus it’s cheaper and pfsense is free. We already have a local file and print server at each location so it just spinning up another VM with pfsense on it and using additional Ethernet ports on the 1U server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-02-2022 05:13 AM
Hi,
Below is a very basic example from EXOS:
ExtremeXOS® User Guide (extremenetworks.com)
It sounds like most of the magic in your situation is happening on the Cisco side of things so not sure what additional configuration you would need from EXOS regarding that topology.
Thanks,
Chris Thompson