This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: How to view ssh public key "fingerprint" on th...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
How to view ssh public key "fingerprint" on the switch?
How to view ssh public key "fingerprint" on the switch?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-04-2016 02:20 PM
Hi Guys,
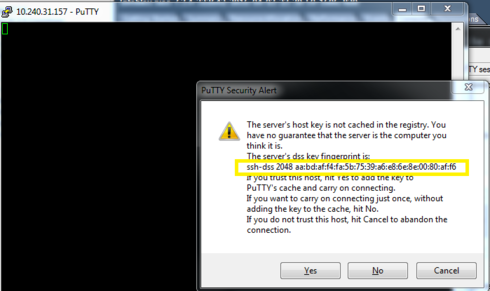
A quick question for you. How do l view ssh public key "fingerprint" on the switch when presented using PuTTy?
A quick question for you. How do l view ssh public key "fingerprint" on the switch when presented using PuTTy?
13 REPLIES 13
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-08-2016 06:49 AM
Hi,
SSH authenticates both communication endpoints, server and client. The server is authenticated with the public host key in a "trust on first use" model. On the first connection, the fingerprint of the server's public key is displayed to the user, who has to decide whether to trust this key or not. This decision is facilitated by checking the server's public host key's fingerprint out-of-band, e.g. when connected via serial console.
Current EXOS does not support checking the host key fingerprint. 😞
To work around this limitation, one can copy the private key of the EXOS switch to e.g. a GNU/Linux system, and then use tools usually available on GNU/Linux to determine the fingerprint. This works for not encrypted private keys only. The private key of a device should not be copied to another system, as such the copied key needs to be securely deleted after generating the fingerprint.
Best regards,
Erik
SSH authenticates both communication endpoints, server and client. The server is authenticated with the public host key in a "trust on first use" model. On the first connection, the fingerprint of the server's public key is displayed to the user, who has to decide whether to trust this key or not. This decision is facilitated by checking the server's public host key's fingerprint out-of-band, e.g. when connected via serial console.
Current EXOS does not support checking the host key fingerprint. 😞
To work around this limitation, one can copy the private key of the EXOS switch to e.g. a GNU/Linux system, and then use tools usually available on GNU/Linux to determine the fingerprint. This works for not encrypted private keys only. The private key of a device should not be copied to another system, as such the copied key needs to be securely deleted after generating the fingerprint.
- Display private host key on EXOSshow ssh2 private-key
- Copy&paste private key to file privkey.exos on GNU/Linux touch privkey.exos chmod 0600 privkey.exos cat > privkey.exos
- Convert EXOS key format to OpenSSH format on GNU/Linux touch privkey.openssh chmod 0600 privkey.openssh tr -dc '[:xdigit:]' < privkey.exos | xxd -p -r > privkey.openssh
- Generate public key from private key on GNU/Linuxssh-keygen -y -f privkey.openssh > pubkey.openssh
- Remove private key files (may not be secure) on GNU/Linuxshred -u privkey.exos privkey.openssh
- Generate fingerprint on GNU/Linuxssh-keygen -l -f pubkey.openssh | cut -d' ' -f2
Best regards,
Erik
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-08-2016 06:49 AM
Hi Erik,
Wow, thanks for this. Really detailed answer.
Thanks all,
Mykhaylo
Wow, thanks for this. Really detailed answer.
Thanks all,
Mykhaylo
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-08-2016 06:49 AM
Very clever Erik. I'll make sure Drew gets this to our Dev team as a point of discussion.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-04-2016 04:04 PM
Hi,
Try:
"show sshd2 user-key"
"show ssh2 private-key"
Try:
"show sshd2 user-key"
"show ssh2 private-key"