This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: Limiting inbound BGP routes
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Limiting inbound BGP routes
Limiting inbound BGP routes
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-19-2015 11:17 AM
Hello,
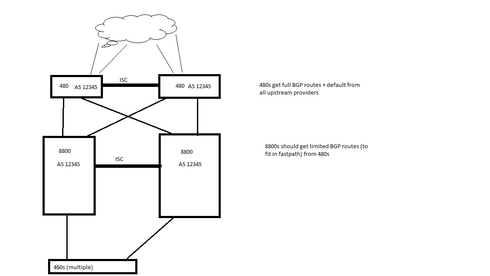
I'm multihomed with several upstream providers over two 480s and get full BGP routes from them. Both 480s are connected to two "core" 8806s that then connect to a bunch of 460s.
The 8806s are the default routers for all of our customers' public IP ranges.
I want to at least "pre-sort" Internet-bound traffic on the 8806s, so that they send the traffic to the right 480, so the 8806s are BGP neighbors to the 480s.
Now, the 8806s with the cards I have aren't necessarily designed to handle full BGP routes in fastpath, so I probably should somehow limit the BGP routes they receive from the 480s. My idea here was to only accept routes to networks that are a /16 or bigger (I may have to adjust the size). That way, I think, I at least pre-sort some of the traffic to the right outbound router, understanding that some traffic will still go from router1 to router2 out to the Internet - and as last resort, there's always the default route 😉
If I use the following policy inbound on the 8806s, would that properly limit my BGP routes on the 8806s to "only blocks from a /0 to /16" (or rather: denying /17 and larger masks, allowing the rest)? And yes, I'd play a similar game with ipv6.
Will the policy work as expected? Is there a better way?
configure bgp neigh 1.2.3.4 route-policy in NoSmallBlocks
File: NoSmallBlocks.pol
entry DenySmallBlocks {
if match any {
nlri any/17;
nlri any-ipv6/33;
} then { deny; }
}
entry AllowRest {
if {
} then { allow; }
}
Thanks for all your help!
Frank
I'm multihomed with several upstream providers over two 480s and get full BGP routes from them. Both 480s are connected to two "core" 8806s that then connect to a bunch of 460s.
The 8806s are the default routers for all of our customers' public IP ranges.
I want to at least "pre-sort" Internet-bound traffic on the 8806s, so that they send the traffic to the right 480, so the 8806s are BGP neighbors to the 480s.
Now, the 8806s with the cards I have aren't necessarily designed to handle full BGP routes in fastpath, so I probably should somehow limit the BGP routes they receive from the 480s. My idea here was to only accept routes to networks that are a /16 or bigger (I may have to adjust the size). That way, I think, I at least pre-sort some of the traffic to the right outbound router, understanding that some traffic will still go from router1 to router2 out to the Internet - and as last resort, there's always the default route 😉
If I use the following policy inbound on the 8806s, would that properly limit my BGP routes on the 8806s to "only blocks from a /0 to /16" (or rather: denying /17 and larger masks, allowing the rest)? And yes, I'd play a similar game with ipv6.
Will the policy work as expected? Is there a better way?
configure bgp neigh 1.2.3.4 route-policy in NoSmallBlocks
File: NoSmallBlocks.pol
entry DenySmallBlocks {
if match any {
nlri any/17;
nlri any-ipv6/33;
} then { deny; }
}
entry AllowRest {
if {
} then { allow; }
}
Thanks for all your help!
Frank
8 REPLIES 8
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-19-2015 02:37 PM
Basic quick-and-dirty picture. Customers are connected on ports on the 460s, 8800s' VRRP IP address as their default gateway, each customer in their own vlan.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-19-2015 01:39 PM
Could you show the topology We can confirm the policy with the topology
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-19-2015 11:38 AM
I do not want to limit the routes on the 480s, which are the edge/egress routers. I want them to have the full route set (well, as full as I can get without blowing up the 480s, given that the current ipv4 routes exceed the limits on most routers out there )
This is only to pre-sort outbound traffic that passes through the 8806s. I want to minimize the 8806s sending traffic to the "wrong" 480, as well as actually actively sending traffic to both 480s (and not just the one that currently holds the VRRP IP)
This is only to pre-sort outbound traffic that passes through the 8806s. I want to minimize the 8806s sending traffic to the "wrong" 480, as well as actually actively sending traffic to both 480s (and not just the one that currently holds the VRRP IP)
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-19-2015 11:28 AM
Who is your service provider AT&T and sprint add route policy by default. In 2 x480 with ibgp peers and each one having Ebgp neighbour to service provider you can add an outbound policy allowing only the lab subnets and deny rest . By doing this we are just blocking a possible transit autonomous loop . Also make sure for Bgp to run properly use 15.x version