This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: Loopback on same network unreachable
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Loopback on same network unreachable
Loopback on same network unreachable
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-20-2014 06:25 PM
Hi, I am trying to connect another switch to my network to segregate customer vlan's.
I am announcing my networks as /24's and want to create smaller subnets of these on another switch within my network. So for example create a loopback vlan with a /29 for a single client server connection.
I am testing this in my lab where I have a single network of 192.168.1.1/24. I have created a vlan "InputLB" which is set as loopback and has ipforwarding on. This vlan has 1 port which is active and is connected to the main 192.168.1.1/24 network. This InputLB vlan is assigned the IP address 192.168.1.33/29.
When I try to ping the 192.168.1.33 from any devie on my network, it will not ping. What am I doing wrong? Will this configuration be possible?
Thanks for any help.
I am announcing my networks as /24's and want to create smaller subnets of these on another switch within my network. So for example create a loopback vlan with a /29 for a single client server connection.
I am testing this in my lab where I have a single network of 192.168.1.1/24. I have created a vlan "InputLB" which is set as loopback and has ipforwarding on. This vlan has 1 port which is active and is connected to the main 192.168.1.1/24 network. This InputLB vlan is assigned the IP address 192.168.1.33/29.
When I try to ping the 192.168.1.33 from any devie on my network, it will not ping. What am I doing wrong? Will this configuration be possible?
Thanks for any help.
18 REPLIES 18
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-21-2014 11:44 AM
I have checked this config of using both methods and that seems to work ok. I think I need to step back and draw a network diagram. It's all in my head at the moment.
I think if I use my new switch and link it to my router by a tagged vlan, then create a supervlan on it and split it into multiple vlans with restricted IP's, this would be best.
I can then make this switch use the whole /24 range as required.
Thanks so much for all your help.
I think if I use my new switch and link it to my router by a tagged vlan, then create a supervlan on it and split it into multiple vlans with restricted IP's, this would be best.
I can then make this switch use the whole /24 range as required.
Thanks so much for all your help.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-21-2014 11:29 AM
I see...
There's a couple of features that may help you prevent this:
There's a couple of features that may help you prevent this:
- Disable ARP learning and statically configure the IP to MAC relation, so the customer can't simply change the IP address and keep on working.
- Use ARP validation, forcing all servers to use a secure DHCP server to get their addresses and disallow statically configured IP addresses. In the DHCP server you could then fix the IP address you give each server based on their MAC.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-21-2014 11:29 AM
Thanks for the lengthy explanation, the detail is much appreciated.
This is exactly what I want to do, however the reason that I need to assign an IP address (range) to a loopback vlan port for a client is to restrict their IP addresses so that they do not try and steal IP's. My clients will have full control over their own machines and I want to be sure that the network is secure and no one is going to try and steal each other's IPs.
For example if I am renting a server to a client and the server gets compromised, as they do sometimes, then with this setup the attacker can then take control of all IP's in the range. And then for example start sending spam and get the whole range blacklisted.
A hybrid of both solutions would be ideal. Be able to give them a private vlan and also restrict the IP's they can use like the subvlan method.
This is exactly what I want to do, however the reason that I need to assign an IP address (range) to a loopback vlan port for a client is to restrict their IP addresses so that they do not try and steal IP's. My clients will have full control over their own machines and I want to be sure that the network is secure and no one is going to try and steal each other's IPs.
For example if I am renting a server to a client and the server gets compromised, as they do sometimes, then with this setup the attacker can then take control of all IP's in the range. And then for example start sending spam and get the whole range blacklisted.
A hybrid of both solutions would be ideal. Be able to give them a private vlan and also restrict the IP's they can use like the subvlan method.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-21-2014 11:01 AM
Michael,
I've never used this feature but the way I see it both the private vlans and the network vlan operate at layer 2.
You don't need to use /29 subnets to isolate different customers. The private vlans will do that for you.
The private vlans don't have an IP address, and the network vlan CAN have one, but does not need to have one configured. All the servers in the different pvlans would share the 192.168.1.0/24 subnet and use the router IP address as their default gateway.
Suppose you have one customer (customer1) with 3 servers, another customer (customer2) with 2 servers, and 10 customers (other), each one with a single server. An you want all the servers to be able to reach the router (their default gateway) while not being able to see the servers of other customers (but still be able to reach other servers from the same customer if they have more than one...).
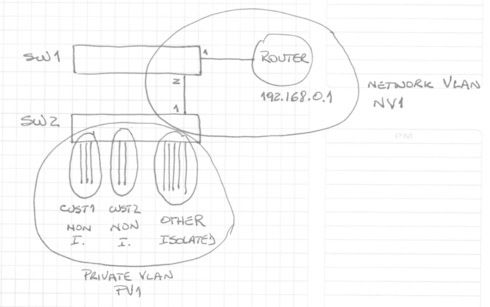
I'm attaching a quick and dirty sketch of what I'd do.
I'd create one vlan for customer 1 with 3 ports, one vlan for customer2 with 2 ports and a vlan for the other customers with 10 (or more) ports.
I would then add these three vlans to a private vlan, the first two as non-isolated so the servers connected to each one of them can see each other (within the vlan), and the third one as isolated so the servers connected to it can't see each other.
I would then create a network vlan to allow all these customer vlans in the private vlan to reach the router (or any other shared services...)
All of the servers would have addresses in the 192.168.1.0/24 subnet, and all would have ip 192.168.1.1 as their default gateway (assuming that is the ip address of the router...)
The config for each switch would be something like this (just creating it on the fly, may have forgotten something...)
SW1:
#
# always remove ports from vlan default (best practice)
#
configure default delete ports all
#
# create network vlan and assign ports
#
create vlan nv1 tag 100
configure nv1 add ports 1
configure nv1 add ports 2 t
# --------------------------------------------------------------
SW2:
#
# always remove ports from vlan default (best practice)
#
configure default delete ports all
#
# create network vlan and assign ports
#
create vlan nv1 tag 100
configure nv1 add ports 1 t
#
# create customer vlans and assign ports
#
create vlan cust1 tag 201
create vlan cust2 tag 202
create vlan other tag 203
configure cust1 add ports 2-4
configure cust2 add ports 10-11
configure other add ports 15-24
#
# create private vlan and assign network vlan and subscriber vlans
#
create private-vlan pv1
configure private-vlan pv1 add network nv1
configure private-vlan pv1 add subscriber cust1 non-isolated
configure private-vlan pv1 add subscriber cust2 non-isolated
configure private-vlan pv1 add subscriber other
#
# create network vlan and assign ports
#
configure nv1 add ports 1 private-vlan translated
# --------------------------------------------------------------
As you can see, there's not a single ip address in all the config for either switch. It's all a pure layer 2 thing.
What about provisioning?
Daniel
I've never used this feature but the way I see it both the private vlans and the network vlan operate at layer 2.
You don't need to use /29 subnets to isolate different customers. The private vlans will do that for you.
The private vlans don't have an IP address, and the network vlan CAN have one, but does not need to have one configured. All the servers in the different pvlans would share the 192.168.1.0/24 subnet and use the router IP address as their default gateway.
Suppose you have one customer (customer1) with 3 servers, another customer (customer2) with 2 servers, and 10 customers (other), each one with a single server. An you want all the servers to be able to reach the router (their default gateway) while not being able to see the servers of other customers (but still be able to reach other servers from the same customer if they have more than one...).
I'm attaching a quick and dirty sketch of what I'd do.
I'd create one vlan for customer 1 with 3 ports, one vlan for customer2 with 2 ports and a vlan for the other customers with 10 (or more) ports.
I would then add these three vlans to a private vlan, the first two as non-isolated so the servers connected to each one of them can see each other (within the vlan), and the third one as isolated so the servers connected to it can't see each other.
I would then create a network vlan to allow all these customer vlans in the private vlan to reach the router (or any other shared services...)
All of the servers would have addresses in the 192.168.1.0/24 subnet, and all would have ip 192.168.1.1 as their default gateway (assuming that is the ip address of the router...)
The config for each switch would be something like this (just creating it on the fly, may have forgotten something...)
SW1:
#
# always remove ports from vlan default (best practice)
#
configure default delete ports all
#
# create network vlan and assign ports
#
create vlan nv1 tag 100
configure nv1 add ports 1
configure nv1 add ports 2 t
# --------------------------------------------------------------
SW2:
#
# always remove ports from vlan default (best practice)
#
configure default delete ports all
#
# create network vlan and assign ports
#
create vlan nv1 tag 100
configure nv1 add ports 1 t
#
# create customer vlans and assign ports
#
create vlan cust1 tag 201
create vlan cust2 tag 202
create vlan other tag 203
configure cust1 add ports 2-4
configure cust2 add ports 10-11
configure other add ports 15-24
#
# create private vlan and assign network vlan and subscriber vlans
#
create private-vlan pv1
configure private-vlan pv1 add network nv1
configure private-vlan pv1 add subscriber cust1 non-isolated
configure private-vlan pv1 add subscriber cust2 non-isolated
configure private-vlan pv1 add subscriber other
#
# create network vlan and assign ports
#
configure nv1 add ports 1 private-vlan translated
# --------------------------------------------------------------
As you can see, there's not a single ip address in all the config for either switch. It's all a pure layer 2 thing.
What about provisioning?
- If you add a customer with a single server, you just add another port to vlan other.
- If you add another server for a customer that already has a separate vlan, you just add aport to that vlan.
- If a customer that had a single server wants to add another, create a separate vlan for them, add two ports to connect the servers, and add the vlan as susbscriber, non-isolated to the private vlan.
Daniel
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-21-2014 06:29 AM
Thanks again. I'm trying this configuration out and am running into issues with the subscriber vlan ip address.
I have set up the following:
Main loopback VLAN set as private VLAN's network VLAN - tagged 100
second loopback VLAN set as subscriber VLAN of private VLAN - tagged 101
now the second loopback VLAN would be used as an isolated client vlan with a specific IP range, lets say a /29. However I cannot add an ip address to this vlan:
Error: Subscriber VLAN vl_test_1 cannot be configured with IP address.
This seems to be the perfect solution apart from this issue.
I have set up the following:
Main loopback VLAN set as private VLAN's network VLAN - tagged 100
second loopback VLAN set as subscriber VLAN of private VLAN - tagged 101
now the second loopback VLAN would be used as an isolated client vlan with a specific IP range, lets say a /29. However I cannot add an ip address to this vlan:
Error: Subscriber VLAN vl_test_1 cannot be configured with IP address.
This seems to be the perfect solution apart from this issue.