This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- Switch versus firewall security - I'm not sold... ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Switch versus firewall security - I'm not sold... Thoughts?
Switch versus firewall security - I'm not sold... Thoughts?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-23-2018 12:55 AM
I have a client who recently implemented a managed security platform which places a sensor inline with LAN traffic in order to inspect for threats. The sensors are not able to keep up with all traffic on the LAN and so the suggestion is to move our core routing off of the firewall to the core switch, then capture only north/south traffic from the switch to the firewall for Internet bound traffic.
To me, it's much harder and less secure (although maybe quicker) to implement ACL's on the switch based VR to manage all of the inside VLAN security (guest wireless to internet only, conference rooms to internet only, private wireless to LAN or internet, etc.). I like having application layer filtering between VLAN's, the ability to inspect for threat signatures, etc. I also like being able to look at a common set of rules (same language / platform) to avoid "missing" something when security is split up like this.
My dilemma? I can set up basic ACL's for the trusted networks and keep all of the untrusted networks directly into the firewall, but then I defeat the purpose of the sensor (not really getting a full picture of the network threats). My other option is to add another firewall outside my current one just handle internet/VPN (I'd watch the traffic between the two via the sensor). I think many would just use a router on the outside, but again I'm looking for consistent security/policy management. I'm good with arguments on both sides of that topic.
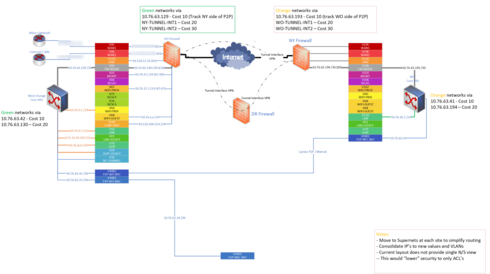
My question - am I off-base on my concerns over trying to have a switch act as a firewall, even though it's arguably a better/faster "router" in this example? I'll add the first part of the visio I'm working on that led me to these concerns. The biggest issue is the number of items on the left- hand side still connected directly to the firewall and therefore they'd not cross the inspected V90 VLAN (north/south traffic).
This is a relatively small network (about 400 stations in total between 2 sites + DR). We're adding L2 circuits between main sites too, so this played into my desire to route there via the switch. We had some issues with ICMP redirects when having the firewall route devices back through those circuits via the remote IP as a gateway.
Over thinking this? Many of these clients started off smaller with only a single firewall (as opposed to dual with a DMZ and or separate N/S VLAN). As they grow I always consider the benefits of going with dual firewalls, but is the switch a better alternative that I'm just not as comfortable with? I appreciate your thoughts and opinions!
To me, it's much harder and less secure (although maybe quicker) to implement ACL's on the switch based VR to manage all of the inside VLAN security (guest wireless to internet only, conference rooms to internet only, private wireless to LAN or internet, etc.). I like having application layer filtering between VLAN's, the ability to inspect for threat signatures, etc. I also like being able to look at a common set of rules (same language / platform) to avoid "missing" something when security is split up like this.
My dilemma? I can set up basic ACL's for the trusted networks and keep all of the untrusted networks directly into the firewall, but then I defeat the purpose of the sensor (not really getting a full picture of the network threats). My other option is to add another firewall outside my current one just handle internet/VPN (I'd watch the traffic between the two via the sensor). I think many would just use a router on the outside, but again I'm looking for consistent security/policy management. I'm good with arguments on both sides of that topic.
My question - am I off-base on my concerns over trying to have a switch act as a firewall, even though it's arguably a better/faster "router" in this example? I'll add the first part of the visio I'm working on that led me to these concerns. The biggest issue is the number of items on the left- hand side still connected directly to the firewall and therefore they'd not cross the inspected V90 VLAN (north/south traffic).
This is a relatively small network (about 400 stations in total between 2 sites + DR). We're adding L2 circuits between main sites too, so this played into my desire to route there via the switch. We had some issues with ICMP redirects when having the firewall route devices back through those circuits via the remote IP as a gateway.
Over thinking this? Many of these clients started off smaller with only a single firewall (as opposed to dual with a DMZ and or separate N/S VLAN). As they grow I always consider the benefits of going with dual firewalls, but is the switch a better alternative that I'm just not as comfortable with? I appreciate your thoughts and opinions!
5 REPLIES 5
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-23-2018 12:58 AM
I should add, the colored blocks represent the core switch and various VLAN's. I've pulled the virtual router (VR1) off to the side to visualize it against the firewall based connections. At the top, the firewall is actually connected back through the switch to the ISP-provided routers so in truth "The Internet" should be connected to them, but it was harder to visualize. Some VLAN's do not have VIP's and are simply used to isolate traffic. In addition, the NY firewall has more active connections - I just didn't get them documented yet. This question came to mind while working on that, so it's still missing quite a bit of detail.