This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (Other)
- NAC + Active Directory + Wifi Users authentication
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NAC + Active Directory + Wifi Users authentication
NAC + Active Directory + Wifi Users authentication
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-16-2018 02:47 PM
Hello, everybody,
please, let me know whether goals below are possible or not and answer some of my questions:
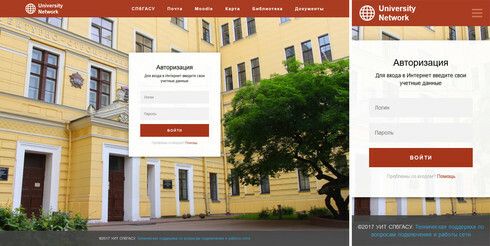
1) I would like to create NAC authorization portal for desktop and mobile users like this (I mean - exactly the same):
2) I would like to authorize Internet access for wired and wireless (V2110) users using their AD credentials (so, NAC has to get AD account information from several domains)
3) I would like to see AD account names for authorized users in Netsight > Control > Endpoints (like OS type and version data)
4) I would like to send these usernames to Fortigate FG-600 and get all possible benefits from Extreme&Fortinet integration
Is it all possible?
My questions are:
1) Are there any separated or combined step-by-step manuals for all goals above? Please, share them!
2) How to make wired users get authenticated through NAC? For wireless I just set in V2110: VNS > WLAN Services > Auth & Acct > Mode: Authentication type External and set Redirection URL, but how about wired users?
3) How could I make NAC to authorize AD users account in several domains?
4) And the most difficult question: how could I make Netsight NAC to send usernames in Fortigate? I want get benefits described by Kurt Semba here: https://community.extremenetworks.com/extreme/topics/does-extreme-still-have-technological-partnersh...
I had already bought all the hardware - there are about 100 Summits + Netsight + NAC + V2110 + 100APs + Fortigate FG-600.
At the moment authorization portal is on FG-600. It gets user names but, I want to see them in Netsight!
Please, help!
Many thanks in advance,
Ilya
please, let me know whether goals below are possible or not and answer some of my questions:
1) I would like to create NAC authorization portal for desktop and mobile users like this (I mean - exactly the same):
2) I would like to authorize Internet access for wired and wireless (V2110) users using their AD credentials (so, NAC has to get AD account information from several domains)
3) I would like to see AD account names for authorized users in Netsight > Control > Endpoints (like OS type and version data)
4) I would like to send these usernames to Fortigate FG-600 and get all possible benefits from Extreme&Fortinet integration
Is it all possible?
My questions are:
1) Are there any separated or combined step-by-step manuals for all goals above? Please, share them!
2) How to make wired users get authenticated through NAC? For wireless I just set in V2110: VNS > WLAN Services > Auth & Acct > Mode: Authentication type External and set Redirection URL, but how about wired users?
3) How could I make NAC to authorize AD users account in several domains?
4) And the most difficult question: how could I make Netsight NAC to send usernames in Fortigate? I want get benefits described by Kurt Semba here: https://community.extremenetworks.com/extreme/topics/does-extreme-still-have-technological-partnersh...
I had already bought all the hardware - there are about 100 Summits + Netsight + NAC + V2110 + 100APs + Fortigate FG-600.
At the moment authorization portal is on FG-600. It gets user names but, I want to see them in Netsight!
Please, help!
Many thanks in advance,
Ilya
4 REPLIES 4
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-16-2018 03:19 PM
That´s all possible !
1. You need to understand what you do. Step-by-step guides can help you to setup the solution but the don´t help you troubleshooting this. User a qualified partner for that or take trainings.
2. You can use policies or policy based routing to redirect traffic from wired ports to the NAC portal.
3. NAC gateway can deal with domain prefix and contact different LDAP servers
4. It´s included in the OneFabric connect install guide
Option: Use the FG-600 Portal and redirect RADIUS to NAC-Gateway. You will see the users in XMC.
You will need some experience and knowledge of the interfaces to other systems, but it will work.
br
Volker
1. You need to understand what you do. Step-by-step guides can help you to setup the solution but the don´t help you troubleshooting this. User a qualified partner for that or take trainings.
2. You can use policies or policy based routing to redirect traffic from wired ports to the NAC portal.
3. NAC gateway can deal with domain prefix and contact different LDAP servers
4. It´s included in the OneFabric connect install guide
Option: Use the FG-600 Portal and redirect RADIUS to NAC-Gateway. You will see the users in XMC.
You will need some experience and knowledge of the interfaces to other systems, but it will work.
br
Volker
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-16-2018 03:19 PM
Hi, Ilya!
NAC gateway - is NAC appliance.
(gateway is exactly NAC, management from XMC GUI)
Thank you!
NAC gateway - is NAC appliance.
(gateway is exactly NAC, management from XMC GUI)
Thank you!
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-16-2018 03:19 PM
Hi Ilya !
NAC-Gateway is the appliance (virtual or HW) working as a authentication proxy. That means you confg wifi , switch, FW etc. to connect via RADIUS to the NAC-GW. Using the NAC rules you configure via XMC and push it to all NAC-GW, it will connect via RADIUS or LADP to directory services based on the user match rules you define (\* to AD1, \* to AD2 and so on). Radius proxy means that NAC-GW can change the authentication protocol or use internal DB(f.e. for MAC-Auth) . NAC-GW provide also a web portal with different options: splash, account, sponsoring, social media login, self service.
We use NAC for brach office authentication on FG-50/60..., Juniper, ...
All is absolutely conform with the standards (802.1X, PEAP, TLS, RADIUS, RFC3580, ...)
So you will have a lot of options that makes XMC/NAC/Analytics a pearl in infrastructure&security management and monitoring. No other vendor can beat this !
br
Volker
NAC-Gateway is the appliance (virtual or HW) working as a authentication proxy. That means you confg wifi , switch, FW etc. to connect via RADIUS to the NAC-GW. Using the NAC rules you configure via XMC and push it to all NAC-GW, it will connect via RADIUS or LADP to directory services based on the user match rules you define (
We use NAC for brach office authentication on FG-50/60..., Juniper, ...
All is absolutely conform with the standards (802.1X, PEAP, TLS, RADIUS, RFC3580, ...)
So you will have a lot of options that makes XMC/NAC/Analytics a pearl in infrastructure&security management and monitoring. No other vendor can beat this !
br
Volker
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-16-2018 03:19 PM
Thanks, Volker!
What the NAC-Gateway is?
You mean, from FG-600 side set NAC as radius server, so FG-600 will authorize users not with AD Domain controllers directly, but through NAC?
Am I right?
What the NAC-Gateway is?
You mean, from FG-600 side set NAC as radius server, so FG-600 will authorize users not with AD Domain controllers directly, but through NAC?
Am I right?