- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- Re: airdefense ADSP server - Rogue AP not showing ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
airdefense ADSP server - Rogue AP not showing up
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-06-2023 12:05 PM - edited 01-06-2023 12:19 PM
Hello,
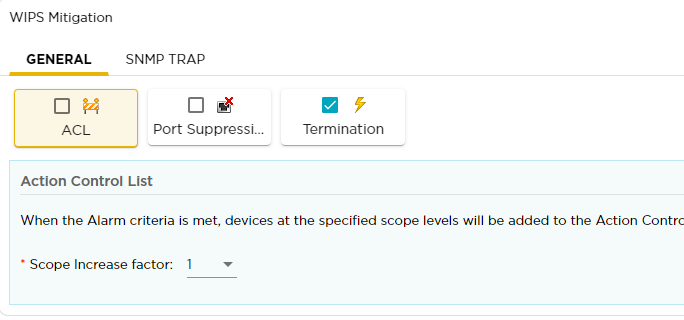
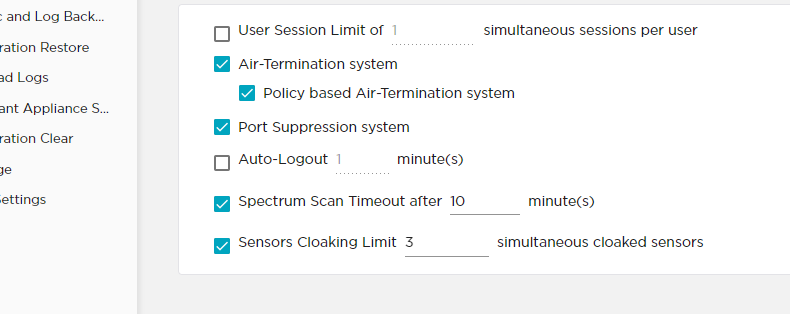
I'm using a Netgear nighthaw wireless router to test airdefense Rogue detection and termination. I get the alarms we configure like unsanctioned bss using sanction bss and sanctioned wpa3 ssid name same as unsanctioned wpa2 bss and a lot other alarms but i never get the alarm of a rogue AP. I verified the AP has the WIPS license and that air termination system and policy based air-termination system options are checked.
Also, after my phone connects to my rogue AP I try to do air termination manually but i get an error "unable to terminate device: FCC check failed or device not authorized or device not rogue".
I'm doing this by clicking on the alarm > 3 dots > and terminate option. I've attached some screenshots.
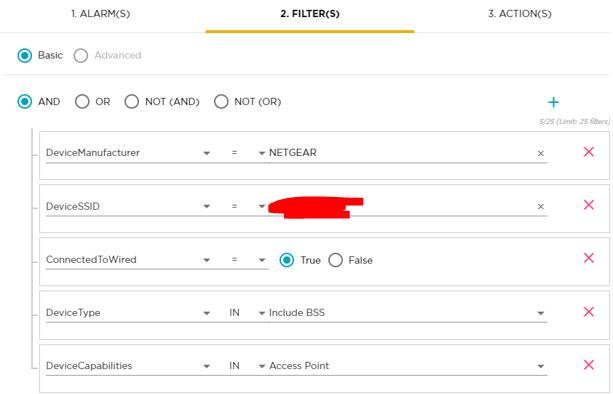
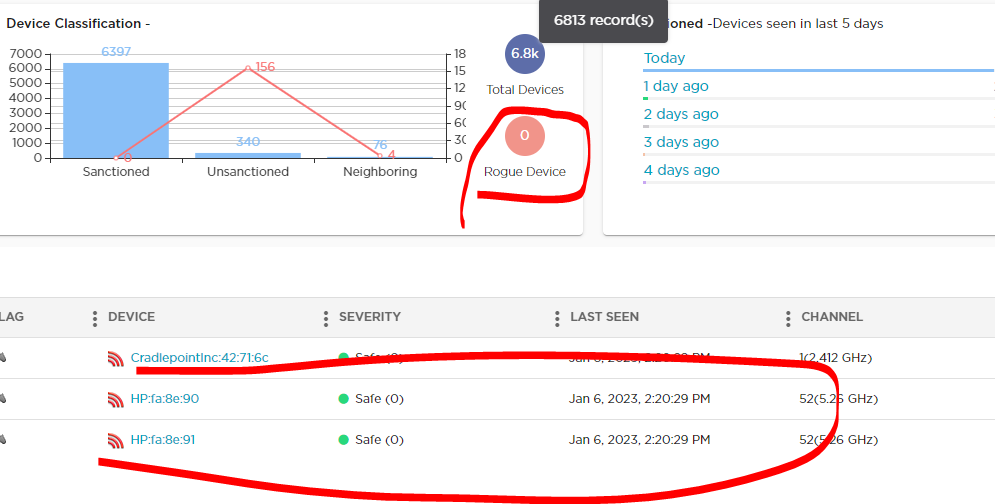
I have some filters on the alarm action manager rule i created that's supposed to trigger airtermination. I'm almost certain that the filters are going be wrong but I think I should at least see this AP showing as a BSS and a Rogue AP?
we have a device action rule that classifies our APs as sanction and we have both of our controllers communicating with airdefense and all our APs are showing up. I can see neighbor BSSs and other stuff.
I have this netgear AP set as access point connected to my switch and I am able to connect with my phone using the same ssid as our corporate one.
we are using AP4000 APs with the 3rd radio set as a sensor while the other 2 are being used for client connection.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-10-2023 07:42 AM
Generally, AirDefense will need to see some traffic from the suspected rogue device (AP or Client)....whether it be wired or wireless, in order to trigger one of the rogue alerts. Just plugging in an AP and not associating any clients to it will normally not be enough.
Additionally, for some of the versions of rogue alarms (there are more than 1 type of rogue alarm, based on the method that AirDefense used to perform the recognition that the suspected device is in fact passing traffic onto your wired network) AirDefense needs to have at least 1 of your legitimate APs already classified as Sanctioned and exist on the same network segment as the suspected rogue AP, so that it can 'learn' certain traffic patterns that it can use to compare to the suspected rogue.
So my recommendations:
1) Sanction one of your APs on that same network segment as the Netgear
2) Connect a wireless client to the Sanctioned AP and ensure traffic is being passed back and forth for a short time
3) Connect a wireless client to the Netgear (The Netgear should be classified as Unsanctioned, otherwise it will NEVER generate a rogue alarm) and pass traffic for a short time from the client - browse Internet or something similar.
You should see at least one of the rogue alarm types generate for the Netgear at this point, possibly multiple types.
Once you see those alarms generating, you can then begin constructing your Alarm Action Manager rule, as you've shown, to be specific about when that alarm is acted upon. (Your current rule has filters that I highly suspect are not going to match in the way that you desire)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-13-2023 07:15 AM
To be sure the auto-classification rule is working as intended, do you see your imported BSS's classified as Sanctioned? (Green BSS device icons in the Network Devices page)
1) Right now my test netgear AP is on a different subnet. So can I place the netgear AP on the same vlan as the AP4000 so it can generate the alarms so I can then build the alarm action manager rule base on the alarms?
- To quickly start the testing, the Netgear AP should to be on a subnet where there are Sanctioned BSS's and sensors. So yes, if you move it to a VLAN where you have an AP4000/Sensor operating, that should be sufficient.
2) After the alarm is configure (assuming is correctly configured) will the correct alarm and action be triggered if I connect the netgear AP on a different subnet? if not what can i do so this can happen on a different network segment?
- Yes. AirDefense has multiple methods that it uses to detect if an Unsanctioned device is communicating with your wired network. Placing the Netgear on the same subnet is just a way right now to run a quick test to make sure that everything is setup correctly and working in this scenario.
3) how can I classify the netgear AP as an unsanctioned AP?
- In the Network Devices page, navigate to the tree/site where the Netgear BSS is being seen, then click on the "BSS" tab up near the top to populate the BSS table with the discovered BSS's in this tree scope level. Next, locate the Netgear BSS in the BSS table (you can use the Search bar to look for "netgear" most likely). Once it's found, if the BSS Device icon in the table is colored red, then it's already Unsanctioned. If it's green, then it has become Sanctioned somehow. To Unsanction it, look at the farthest right column for that BSS entry ("Action" column) and click on the three dots and select the "Classification" menu option and then choose "Unsanction". NOTE: All wireless devices that are discovered in AirDefense are initially classified as Unsanctioned, by default. AirDefense doesn't trust anything unless told otherwise (Device Action Manager rule to Sanction imported devices, manual Sanctioning, importing CSV file of devices to Sanction, etc). So if the Netgear is found to be Sanctioned, then something was done (by someone) in the system to classify it that way, which needs to be understood and corrected.
2) since we have multiple vlans across our network - how is this going to work in the future if someone does connect a rogue AP on the network since that rogue AP will be on a different network segment?
- The placement of a rogue device on a particular subnet is not a strict requirement for rogue detection. As mentioned above, AirDefense does use multiple techniques to detect the traffic from potential rogue devices. If you do happen to find a scenario where AirDefense cannot make this determination and can reliably repeat it, we'd love to hear about it! Also, depending on the switch model, you may also be able to make use of another rogue detection technique (rogue on switch) by adding switches into AirDefense so that the system can query those switches for potential rogues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-16-2023 08:26 AM
Thank you!
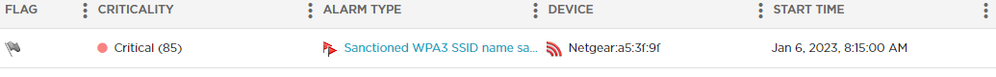
Okay so I moved my netgear AP to the AP4000 vlan and generated the alarms and I was able to do airtermination. I only see two alarms generated, these are:
sanctioned wpa3 ssid name same as unsanctioned wpa2 bss
unsanctioned bss using sanctioned bss using sanctioned ssid
I dont see any alarms generated for unsanctioned ap on wired network or anything like that which im okay with it as long as airtermination works.
My next questions is and hopefully the last one on this topic.
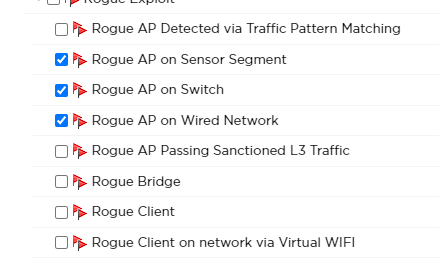
right now i have these alarms configured in one of my alarm action manager rules:
sanctioned wpa3 ssid name same as unsanctioned wpa2 bss
unsanctioned bss using sanctioned ssid
rogue ap on sensor segment
rogue ap on switch
rogue ap on wired network
So my question is, can or should I remove all the other alarms and leave only the two that the netgear Ap generated for it to work on different vlan/network segments?
really need to make sure this works across the hospital and not only on the same vlan as the ap4000 Aps.
I really appreciate your help on this
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-10-2023 07:42 AM
Generally, AirDefense will need to see some traffic from the suspected rogue device (AP or Client)....whether it be wired or wireless, in order to trigger one of the rogue alerts. Just plugging in an AP and not associating any clients to it will normally not be enough.
Additionally, for some of the versions of rogue alarms (there are more than 1 type of rogue alarm, based on the method that AirDefense used to perform the recognition that the suspected device is in fact passing traffic onto your wired network) AirDefense needs to have at least 1 of your legitimate APs already classified as Sanctioned and exist on the same network segment as the suspected rogue AP, so that it can 'learn' certain traffic patterns that it can use to compare to the suspected rogue.
So my recommendations:
1) Sanction one of your APs on that same network segment as the Netgear
2) Connect a wireless client to the Sanctioned AP and ensure traffic is being passed back and forth for a short time
3) Connect a wireless client to the Netgear (The Netgear should be classified as Unsanctioned, otherwise it will NEVER generate a rogue alarm) and pass traffic for a short time from the client - browse Internet or something similar.
You should see at least one of the rogue alarm types generate for the Netgear at this point, possibly multiple types.
Once you see those alarms generating, you can then begin constructing your Alarm Action Manager rule, as you've shown, to be specific about when that alarm is acted upon. (Your current rule has filters that I highly suspect are not going to match in the way that you desire)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-24-2023 10:25 AM
FYI,
I created a new rule with just those two alarms and was able to terminate on different vlan. Thanks for your help.