This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- RE: Log into switch with LDAP credentials
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Log into switch with LDAP credentials
Log into switch with LDAP credentials
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-02-2018 03:02 PM
Currently, we are using accounts created on each switch in order to be able to login.
We do have Extreme Management Center 8.x installed (we have NAC but don't have it fully configured/deployed yet) and have it configured so that users can login to EMC with their LDAP credentials. I know that a user can then use the "Open Device Terminal" via EMC, but we want to know if it is possible (and how we would configure it) so that we can use LDAP accounts instead when they start up PuTTY and SSH to a switch? I have read lots of different posts/articles on this and my head is swimming and need some guidance/clarity. Thanks!
We do have Extreme Management Center 8.x installed (we have NAC but don't have it fully configured/deployed yet) and have it configured so that users can login to EMC with their LDAP credentials. I know that a user can then use the "Open Device Terminal" via EMC, but we want to know if it is possible (and how we would configure it) so that we can use LDAP accounts instead when they start up PuTTY and SSH to a switch? I have read lots of different posts/articles on this and my head is swimming and need some guidance/clarity. Thanks!
18 REPLIES 18
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-03-2018 07:20 AM
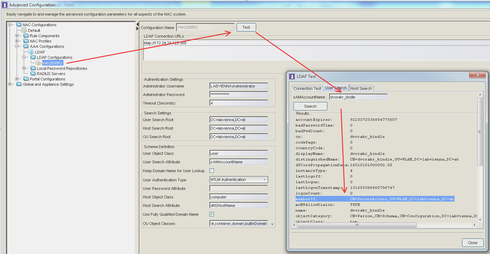
If you don't know the exact attribute string you'd find it very easily...
- open the NAC Manager Java app
- go to advanced config
- select the LDAP server
- click on Test
- User Search and put in the username and click Search
In the output you'd see the full attribute string - copy/paste that in the XOS Admin Group.
- open the NAC Manager Java app
- go to advanced config
- select the LDAP server
- click on Test
- User Search and put in the username and click Search
In the output you'd see the full attribute string - copy/paste that in the XOS Admin Group.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-03-2018 02:38 AM
Please check your Attribute values, it is not complete, it should have the OU .
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-02-2018 09:52 PM
Yes, we are doing this on a test node.
I could not find the specific KB article. I found this one, https://gtacknowledge.extremenetworks.com/articles/How_To/How-to-configure-RADIUS-authentication-for... but I don't think it is the one we want as we are using LDAP and not RADIUS.
I could not find the specific KB article. I found this one, https://gtacknowledge.extremenetworks.com/articles/How_To/How-to-configure-RADIUS-authentication-for... but I don't think it is the one we want as we are using LDAP and not RADIUS.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-02-2018 09:52 PM
NAC is the RADIUS server and NAC is using your AD (LDAP) to access the user/pw information.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-02-2018 07:25 PM
You haven't mentioned whether you've configured the switch for mgmt access authentication via CLI - that would be #2 in the KB article
"Configure the Switches to send management RADIUS requests to the NAC appliance."
As per the last screenshot the config that was done via XMC includes only network access.
!!! don't play around with mgmt access on a production switch - use a test node - or you'd end up with no access in case something is configured not correcty = would be a good idea to configure local fallback !!!
"Configure the Switches to send management RADIUS requests to the NAC appliance."
As per the last screenshot the config that was done via XMC includes only network access.
!!! don't play around with mgmt access on a production switch - use a test node - or you'd end up with no access in case something is configured not correcty = would be a good idea to configure local fallback !!!