- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- Re: wireless BYOD web portal configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
wireless BYOD web portal configuration
wireless BYOD web portal configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-24-2021 01:46 PM
Hello,
We will be replacing our current wireless infrastructure with extreme products (for wireless controllers we will be using XCC, extreme XMC, and a couple of extreme engines for NAC). We are trying to come up with a solution to allows our staff to connect to one of our ssids with their personal devices for internet access only not internal access. We are currently allowing them to user their AD account to connect to our secure wlan and we have a rule that puts them on the outside vlan for internet access only if they use their account to connect. I know we can keep using the same method where if they use their AD account to connect it puts them outside and also limit who can connect but We are looking into using the captive portal - authenticated users options instead to possibly use their work email to get a verification code to connect after being sponsored. We will like to have one public ssid for our guests with captive portal - which we have configured already and we want another ssid with captive portal for our staff and have a way for us to either allow or reject their request and also have a way to monitor the accounts that connect to this ssid. The only document i could find with instructions is for extremecloud IQ.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-28-2021 10:29 AM
In Single SSID BYOD only one SSID is used for both onboardings of devices and later giving full access to the Registered Devices. First, the user connects to the SSID using the user name and password ( MSCHAPv2 ). Once authenticated successfully on ISE, the user gets redirected to the BYOD Portal. Once the Device Registration is done, the end-client downloads the Native Supplicant Assistant (NSA) from ISE . NSA is installed on the end client and downloads the Profile and certificate from ISE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-28-2021 04:14 AM
BYOD flow on Chromebook devices is different from other OS. Unlike other OS where there is no requirement for the endpoints to be pre-registered, the Chromebook devices needs to be enrolled to the Google-Suite before it can go through the ISE BYOD flow. The G-Suite admin needs to configure Chromebook policy on the G-Suite to force installation of NSA Chrome extension. Also, G-Suite admin needs to configure WiFi settings on the Google admin console.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-27-2021 03:39 PM
Hi,
You can use IP address of the NAC instead of FQDN, identity and Shared Secret fields are not necessary. When you use NAC IP address in the ECP URL field, make sure to disable FQDN in the NAC’s Captive Portal settings else the portal won’t load.
Additionally, I would recommend that you use HTTPS instead of HTTP in the ECP URL and enable HTTPS connections in the SSID settings. Likewise enable HTTPS based portal on the NAC. Otherwise most of mobile client devices will throw, security exception errors.
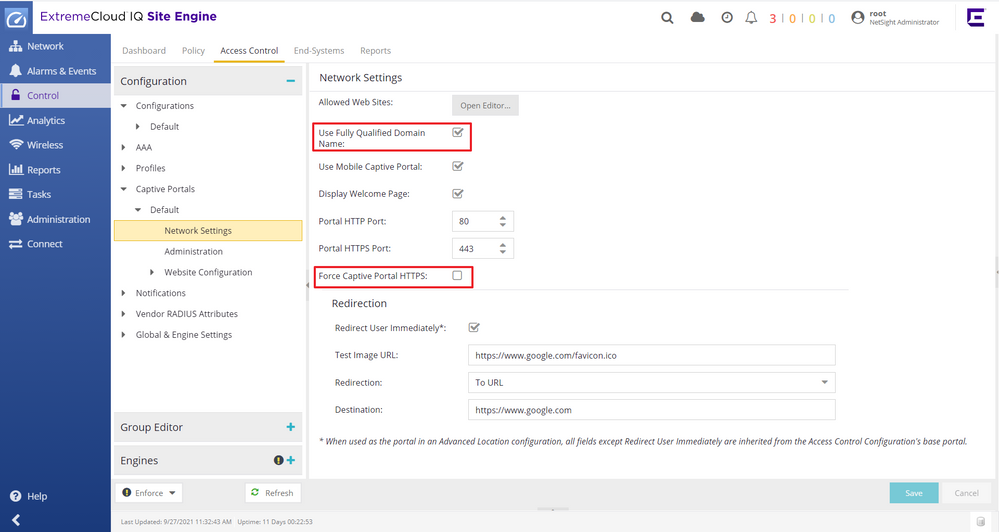
Regards,
Ovais
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-27-2021 01:48 PM
Thanks again for your time!
