- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (WiNG)
- Re: IGMP queries from the AP7532 without settings ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IGMP queries from the AP7532 without settings applied
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-03-2020 11:02 AM
Hello,
Our AP is still sending IGMP queries on the network even if the querier setting is disable on profile.
IGMP queries are sent from the AP on VLAN 5 and cause conflict on the network.
On our architecture, we decided to set the querier on a another switch due to sepecific use cases.
First we needed to deactivate ip spoofing firewall rule beacuse the AP dropped IGMP queries from the switch. But even if ip spoofing is deactivated, sometimes some clients answer to both queriers on the ,network (the AP and the switch) and it can cause brief and total disconnections of clients watching multicast flows (e.g cameras).
Please find below the AP configuration:
!
! Configuration of AP7532 version 5.9.1.4-004R
!
!
version 2.5
!
!
client-identity-group default
load default-fingerprints
!
ip access-list BROADCAST-MULTICAST-CONTROL
permit tcp any any rule-precedence 10 rule-description "permit all TCP traffic"
permit udp any eq 67 any eq dhcpc rule-precedence 11 rule-description "permit DHCP replies"
deny udp any range 137 138 any range 137 138 rule-precedence 20 rule-description "deny windows netbios"
deny ip any 224.0.0.0/4 rule-precedence 21 rule-description "deny IP multicast"
deny ip any host 255.255.255.255 rule-precedence 22 rule-description "deny IP local broadcast"
permit ip any any rule-precedence 100 rule-description "permit all IP traffic"
!
mac access-list PERMIT-ARP-AND-IPv4
permit any any type ip rule-precedence 10 rule-description "permit all IPv4 traffic"
permit any any type arp rule-precedence 20 rule-description "permit all ARP traffic"
!
ip snmp-access-list default
permit any
!
firewall-policy default
no ip dos ipspoof
no ip dos tcp-sequence-past-window
no stateful-packet-inspection-l2
ip tcp adjust-mss 1400
!
!
mint-policy global-default
!
meshpoint-qos-policy default
!
wlan-qos-policy default
rate-limit client to-air rate 5000
rate-limit client from-air rate 5000
qos trust dscp
qos trust wmm
accelerated-multicast 239.1.172.203 classification video
accelerated-multicast 239.1.172.204 classification video
accelerated-multicast 239.1.172.205 classification video
accelerated-multicast 239.1.172.206 classification video
accelerated-multicast 239.1.172.207 classification video
!
radio-qos-policy default
admission-control video max-clients 25
admission-control video max-roamed-clients 256
admission-control video max-airtime-percent 150
admission-control video reserved-for-roam-percent 12
accelerated-multicast max-client-streams 4
accelerated-multicast stream-threshold 500
accelerated-multicast client-timeout 30
!
wlan 1
ssid SSID1
vlan 5
bridging-mode local
encryption-type ccmp
authentication-type none
no fast-bss-transition over-ds
wpa-wpa2 psk 0 123456789
!
wlan 2
ssid SSID2
vlan 11
bridging-mode local
encryption-type ccmp
authentication-type none
no broadcast-ssid
no answer-broadcast-probes
no fast-bss-transition over-ds
wpa-wpa2 psk 0 1234567891
!
wlan 3
ssid SSID3
vlan 1
bridging-mode local
encryption-type ccmp
authentication-type none
no broadcast-ssid
no answer-broadcast-probes
no fast-bss-transition over-ds
wpa-wpa2 psk 0 1234567892
!
wlan CONFIG_ID
ssid 12b25aec52a29c946e21ccbd685c3d93
vlan 1
bridging-mode local
encryption-type ccmp
authentication-type none
no fast-bss-transition over-ds
wpa-wpa2 psk 0 12345EDCBAX
!
dhcp-server-policy WiNGExpressDhcpSvrPolicy
!
!
management-policy default
no telnet
no http server
https server
ssh
user admin password 1 e8aaf41a4b1781b2f65b35e450030684d38ed12bbe3614191c37d192f331e02c role superuser access all
snmp-server manager v2
snmp-server community 0 private rw
snmp-server community 0 public ro
snmp-server user snmptrap v3 encrypted des auth md5 0 admin123
snmp-server user snmpmanager v3 encrypted des auth md5 0 admin123
!
event-system-policy default
!
nsight-policy default
!
profile ap7532 default
no ip igmp snooping
no ip igmp snooping forward-unknown-multicast
autoinstall configuration
autoinstall firmware
crypto ikev1 policy ikev1-default
isakmp-proposal default encryption aes-256 group 2 hash sha
crypto ikev2 policy ikev2-default
isakmp-proposal default encryption aes-256 group 2 hash sha
crypto ipsec transform-set default esp-aes-256 esp-sha-hmac
crypto ikev1 remote-vpn
crypto ikev2 remote-vpn
crypto auto-ipsec-secure
crypto load-management
crypto remote-vpn-client
interface radio1
channel 1
power 20
wlan 1 bss 1 primary
wlan 2 bss 2 primary
wlan 3 bss 3 primary
interface radio2
channel 44
power 20
wlan 1 bss 1 primary
wlan 2 bss 2 primary
wlan 3 bss 3 primary
interface ge1
switchport mode trunk
switchport trunk native vlan 1
no switchport trunk native tagged
switchport trunk allowed vlan 1,5,11
interface vlan1
interface vlan5
interface vlan11
interface pppoe1
use event-system-policy default
use firewall-policy default
use client-identity-group default
logging on
service pm sys-restart
router ospf
adoption-mode controller
!
rf-domain default
timezone Europe/Paris
country-code fr
use nsight-policy default
!
self
! ap7532 94-9B-2C-2A-68-78
radio-count 2
use profile default
use rf-domain default
hostname ap7532
license AP VIRTUAL_CONTROLLER_DEFAULT_AP_LICENSE
no adoption-site
location default
ip default-gateway 192.168.104.1
interface radio1
shutdown
channel 1
interface radio2
shutdown
channel 44
interface vlan1
no description
ip address 192.168.104.3/24
no ip nat
interface vlan5
no description
ip address 10.224.250.3/12
no use dhcp-server-policy
no virtual-controller
rf-domain-manager capable
no ip dns-server-forward
!
!
end
Please find a Wireshark capture screenshot following a capture done on the AP using the command line, “service pktcap on radio all”:

10.224.250.3 → AP IP address
10.241.14.1 → Switch IP address
I’m quiet new with Wing AP and i’d like to understand what I’am missing or settings to be refine in the configuration.
Thanks for your help !
Regards
Arthur
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-01-2021 06:09 PM
Hi Arthur,
I was finally able to reproduce this in my lab and have a fair bit of idea about what you are seeing in your setup.
I am able to see the IGMP query messages from the AP when the client is getting connected. This query message is getting sent as part of multicast to unicast conversion, this is independent of IGMP configured in VLAN. This IGMP query message is needed if mc2uc conversion is required. So, disable mc2uc to avoid IGMP query messages from the AP. This will degrade the performance of multicast traffic to some extent though.
To add further, in some cases, you might also see an IGMPv1 query even if the configured version is IGMPv3. It is decided based on the version of the IGMP membership report sent by the wireless stations. If the IGMP membership report is not received from the station then IGMPv1 will be used as default. In case of IGMP querier is enabled on the AP then configured IGMP version will be used for sending IGMP query as part of mc2uc conversion.
Regards,
Ovais
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-10-2020 07:16 PM
Hi Arthur,
The previous screenshot sent, shows that IGMP is disabled. You are correct, The default ip acces-list BROADCAST-MULTICAST-CONTROL is used to stop the unwanted broadcast and multicast traffic propagating from wired to wireless interface. You can apply it as it is, or make changes to it according to your network and application usage if you use any VOIP, push to talk and Chrome Cast type applications that may use multicast.
Let us know how it goes.
Regards,
Ovais
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-10-2020 05:39 PM
Hello,
To give you more information on this topic, I found something special on the Wireshark capture regarding the AP IGMP query. The unexpected query is still coming from the AP radio to a device (IOS smart phone), according to MAC adresses:
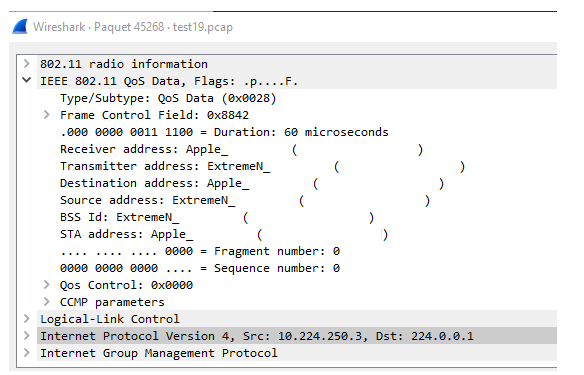
Is there any way to block this traffic ? What I’am thinking today is to use the ip acces-list BROADCAST-MULTICAST-CONTROL to filter this undesired traffic.
Moreover, when I check the IGMP query from the switch, the destination address is the expected one: 224.0.0.1:
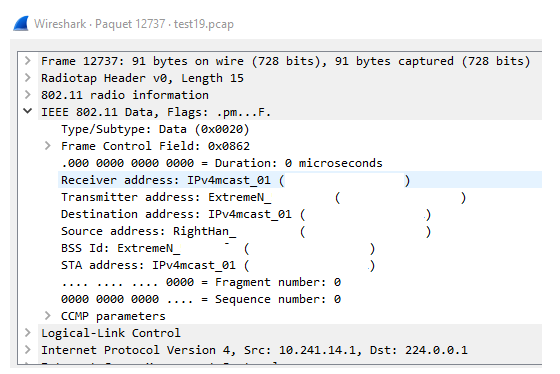
Thanks for your help.
Regards,
Arthur
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-09-2020 08:45 AM
Hello Ovais,
How can I check if it’s an Express unit ?
Please find the “show run include-factory | include ip igmp” result:
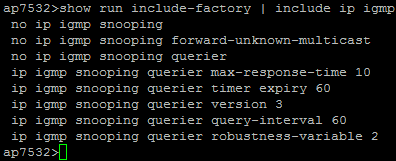
Thanks.
Arthur
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-07-2020 06:39 PM
Arthuroo,
Is it an Express unit? I am asking because I see WiNGExpress in the HDCP policy name.
Please display configuration with “show run include-factory | include ip igmp” and share it here.
Regards,
Ovais
