This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (WiNG)
- SSID Spanning Multiple VLANs
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SSID Spanning Multiple VLANs
SSID Spanning Multiple VLANs
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-09-2018 02:43 PM
We are a small IT department, so I don't have anybody in the office to bounce ideas off of. On top of that, I'm just starting to get comfortable with wireless. I hope this is an appropriate place for this type of conversation.
There is some backstory but I'll try to keep out details that are not needed. I'm working on the first network redesign of our campus since it was first built 10 years ago with most everything (user devices, servers, printers, control systems, etc.) on one /16 network. There are two multiple-floor buildings with edge switches on each floor. They are divided up into 8 distribution areas. When we recently installed IP phones, our Extreme Partner and I designed separate voice VLANs for each of these areas. It has worked so well that they suggested doing the same with our end user data, and I have almost fully completed that project. I'd love to exterminate that VLAN from the vast majority, or even all, of our network.
I'm now looking at our authenticated WiFi and hoping to move that off of the same /16 VLAN that everything else was on. My initial thought was to drop authenticated users onto whatever data VLAN is applicable to area where the AP is located and I have been doing some testing. Everything works fairly well, but I'm concerned about some of our applications when roaming between APs that are on different VLANS. There are a handful of areas that come to mind where overaggressive roaming could be an issue if it occurred because it would cross VLANs.
This VNS is bridged at the AP. We have others that are bridged at the controller, which is a pair of C25s. It has occurred to me that maybe the simplest solution would be to just bridge at the controller, but I wonder if that may cause congestion at the controller as we rely more on WiFi.
We have had Extreme Control on our wish list since I started here, but I don't see it getting approved in the budget any time soon. I feel like that product might give us some better options.
At this point I'm looking at five possibilities.
Thanks in advance for any suggestions you might have.
There is some backstory but I'll try to keep out details that are not needed. I'm working on the first network redesign of our campus since it was first built 10 years ago with most everything (user devices, servers, printers, control systems, etc.) on one /16 network. There are two multiple-floor buildings with edge switches on each floor. They are divided up into 8 distribution areas. When we recently installed IP phones, our Extreme Partner and I designed separate voice VLANs for each of these areas. It has worked so well that they suggested doing the same with our end user data, and I have almost fully completed that project. I'd love to exterminate that VLAN from the vast majority, or even all, of our network.
I'm now looking at our authenticated WiFi and hoping to move that off of the same /16 VLAN that everything else was on. My initial thought was to drop authenticated users onto whatever data VLAN is applicable to area where the AP is located and I have been doing some testing. Everything works fairly well, but I'm concerned about some of our applications when roaming between APs that are on different VLANS. There are a handful of areas that come to mind where overaggressive roaming could be an issue if it occurred because it would cross VLANs.
This VNS is bridged at the AP. We have others that are bridged at the controller, which is a pair of C25s. It has occurred to me that maybe the simplest solution would be to just bridge at the controller, but I wonder if that may cause congestion at the controller as we rely more on WiFi.
We have had Extreme Control on our wish list since I started here, but I don't see it getting approved in the budget any time soon. I feel like that product might give us some better options.
At this point I'm looking at five possibilities.
- Continue with the plan and accept that there might be a few applications that don't preform well roaming between APs.
- Continue with the plan and find a configuration option that I'm not aware of (perhaps something with Inter WLAN Roaming?).
- Create a new VLAN and drop all authenticated WiFi for the SSID on that. (bridge at AP or controller?)
- Some other option that I'm not thinking of.
- Leave it how it is.
Thanks in advance for any suggestions you might have.
13 REPLIES 13
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-09-2018 07:23 PM
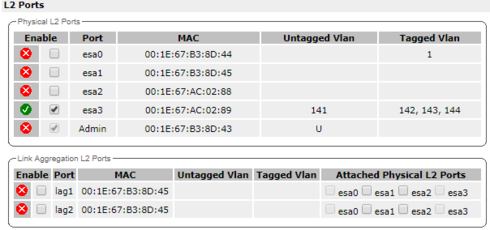
GTAC has always recommend that we disable the administrative L2 port on the controllers. So currently we just have one physical interface. Controller and AP's live on 141 and the rest are wlan segments. For reference:
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-09-2018 07:00 PM
We have 339 AP's bridged to a pair of 5210 controllers. Until recently we had one wireless vlan (/19) across three campuses with a few thousand clients and never had any congestion issues on the controller.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-09-2018 05:24 PM
Hi Rich , there are multiple solutions for your requirements .
1. If you using tunneled topologies (bridged back to controller) we have "VLAN pooling" feature where you can bring multiple VLANs into the same group . If you using default algorithm (MAC address hashing) , then the client will never change the IP address across the campus.
2. If you can to have one large subnet , it is also ok , just make sure (in case you using br@Access Point topology) you enable ARP proxy check box on the topology - in this case you will not see broadcasts/multicasts on the wireless . Just FYI , we do have large amount of installations with very-high-density deployments , and we are using one subnet (/16) and tunneled to controller topology)
3. If you using any sort of authentication (e.g. RADIUS) , you can send Filter-ID back to the controller which will be used to place users in different VLAN . In this case you can separate your users based on the roles they having in the network . Filter-ID should be the same as Role configured on the Controller , so you can have multiple Roles bounded to different VLAN's.
4. If you have Extreme Access Contol in place , then you can leverage the location where the user/end-system coming from (the same SSID , but location can matter ).
1. If you using tunneled topologies (bridged back to controller) we have "VLAN pooling" feature where you can bring multiple VLANs into the same group . If you using default algorithm (MAC address hashing) , then the client will never change the IP address across the campus.
2. If you can to have one large subnet , it is also ok , just make sure (in case you using br@Access Point topology) you enable ARP proxy check box on the topology - in this case you will not see broadcasts/multicasts on the wireless . Just FYI , we do have large amount of installations with very-high-density deployments , and we are using one subnet (/16) and tunneled to controller topology)
3. If you using any sort of authentication (e.g. RADIUS) , you can send Filter-ID back to the controller which will be used to place users in different VLAN . In this case you can separate your users based on the roles they having in the network . Filter-ID should be the same as Role configured on the Controller , so you can have multiple Roles bounded to different VLAN's.
4. If you have Extreme Access Contol in place , then you can leverage the location where the user/end-system coming from (the same SSID , but location can matter ).
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-09-2018 05:24 PM
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-09-2018 05:24 PM
Yury,
Can you point me to where I can find more information about VLAN Pooling? I've found a couple articles that says it is an option, but nothing saying how to use it or where to configure it.
Thanks
Can you point me to where I can find more information about VLAN Pooling? I've found a couple articles that says it is an option, but nothing saying how to use it or where to configure it.
Thanks