This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Training, Documentation, & General Discussions
- General Discussion
- RE: Implement dot1x on EtremSwtich
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Implement dot1x on EtremSwtich
Implement dot1x on EtremSwtich
Anonymous
Not applicable
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-15-2022 05:21 PM
Hello, I am new on ExtremSwitch and am trying to build a port based authentication with Freeradius.
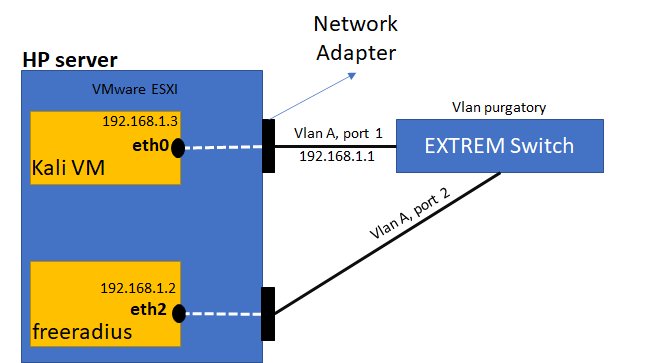
This is my Lab Schematic
This is my switch config that i need your confirmation for it: (is it correct ?)
on the radius side (MD5 authentication) i created a :
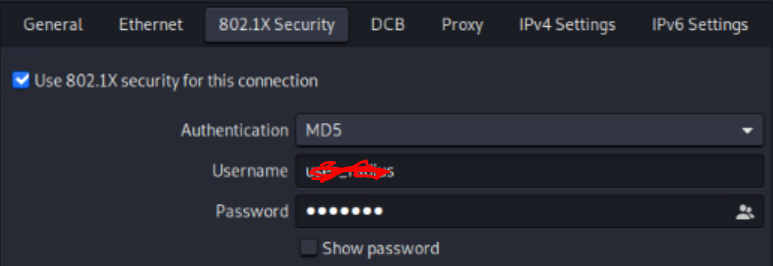
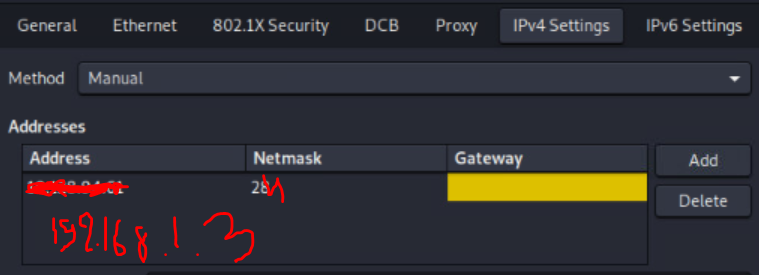
on my kali side i just enable port based authentication from the network setting but am not sure is that enough ?
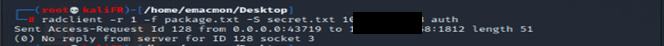
when i send request with radclient, my kali not authenticated on the switch ? do i miss something in my config ?

I hope if i detailed my lab and config well , i will be waiting your answers please, thx
- And i need your confirmation please about my steps for configuring the Extrem switch as authenticator
This is my Lab Schematic

This is my switch config that i need your confirmation for it: (is it correct ?)
create vlan purgatoryconfigure netlogin vlan purgatoryenable netlogin dot1x enable netlogin ports 1 dot1xconfigure netlogin ports 1 mode port-based-vlansconfigure netlogin ports 1 restartconfigure vlan A ipaddress 192.168.1.1/24configure radius netlogin primary server 192.168.1.2 1812 client-ip 192.168.1.1 vr "VR-Default"configure radius netlogin primary shared-secret ilovesecretenable radius netloginon the radius side (MD5 authentication) i created a :
client switch {ipv4add = 192.168.1.1secret = ilovesecret}on my kali side i just enable port based authentication from the network setting but am not sure is that enough ?


when i send request with radclient, my kali not authenticated on the switch ? do i miss something in my config ?


I hope if i detailed my lab and config well , i will be waiting your answers please, thx
4 REPLIES 4
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-19-2022 12:50 PM
I'd check the FreeRadius output. Try running freeradius in debug mode (-X) and capturing the request coming through and seeing if an access-reject is being sent or not. If you don't even see the request then check your firewall or selinux settings. If you see the request then it should give you an idea on why there is a problem or if you have a problem with the supplicant/backend. If freeradius sends an access-accept then you likely have a network problem.
You won't run radclient from your connecting client/laptop. The RADIUS client in this case is the switch, and radclient acts like a switch trying to authenticate a user.
You won't run radclient from your connecting client/laptop. The RADIUS client in this case is the switch, and radclient acts like a switch trying to authenticate a user.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-19-2022 03:16 PM
Hi Matthew, thanks for your feedback,
whit the same radclient command, i can say no i don't have any output on the server side, the only output i have is on the switch is the kali mac add not authenticated.

But i can get access accept on the radclient (from kali) when i disable netlogin on the switch and i can see logs on radius.
There is no tool to send request from the supplicant (kali VM) ?
so what i understand from you radclient play the authenticator rule so how i should used in my scenrio ?
radclient user pass secret serverip ?
and launch it from where ?
aslo if this switch "ExtremeXOS version 30.2.1.8" support multi host (multi supplicant)
thank you
whit the same radclient command, i can say no i don't have any output on the server side, the only output i have is on the switch is the kali mac add not authenticated.

But i can get access accept on the radclient (from kali) when i disable netlogin on the switch and i can see logs on radius.
There is no tool to send request from the supplicant (kali VM) ?
so what i understand from you radclient play the authenticator rule so how i should used in my scenrio ?
radclient user pass secret serverip ?
and launch it from where ?
aslo if this switch "ExtremeXOS version 30.2.1.8" support multi host (multi supplicant)
thank you
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-19-2022 10:07 PM
When you disable netlogin on the switch, it allows traffic through, which is why the RADIUS message generated by radclient can get through. the end system is not the RADIUS client. you should not be using radclient on your end system. RADIUS is not a protocol used by an end client. it is used by the authenticator (in this case the switch) to verify the end client to a backend service. Hence radclient should not be used on the end system.
Please review how 802.1X and RADIUS works. https://www.networkworld.com/article/2216499/wireless-what-is-802-1x.html
Please review how 802.1X and RADIUS works. https://www.networkworld.com/article/2216499/wireless-what-is-802-1x.html
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-20-2022 01:21 AM
Hi matthew,
it was only miss understanding from me to the tool, i know very well port based authentication how it work (supplicant-authentictor-radius)
I think the problem in my case it could be related that i need to find a way to trigger some request from the virtual kali over the physical adapter NIC of the HP server.
but i don't know how to do that? or even my though is correct ?
Actually I was missing to use wpa_supplicant to configure kali as supplicant and also i can use it to trigger authentication request (https://help.ubuntu.com/community/Network802.1xAuthentication)
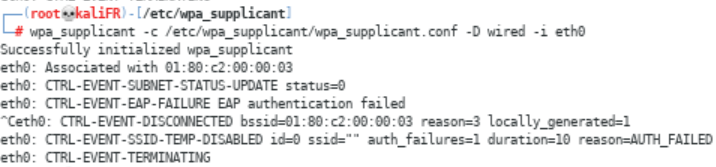
,
it was only miss understanding from me to the tool, i know very well port based authentication how it work (supplicant-authentictor-radius)
I think the problem in my case it could be related that i need to find a way to trigger some request from the virtual kali over the physical adapter NIC of the HP server.
but i don't know how to do that? or even my though is correct ?
Actually I was missing to use wpa_supplicant to configure kali as supplicant and also i can use it to trigger authentication request (https://help.ubuntu.com/community/Network802.1xAuthentication)


,
