- Extreme Networks
- Community List
- Hero Community
- Hero Product Suggestions
- 802.1X supplicant on access switches for uplink au...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
802.1X supplicant on access switches for uplink authentication (for security & automation)
802.1X supplicant on access switches for uplink authentication (for security & automation)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-11-2020 10:58 AM
APs are mostly authenticated at a switchport to use an automatic configuration of switchport behaviours (VLANs, port authentication, ..) like I mentioned in my “AP-Aware” idea. We need this function as well for authentication and automation to connect access switches to core/distribution/fabric switches. This ist for security reasons in case of using distributed switches in office, production, IOT/OT, … to prevent unauthorized usage uf the uplink ports as well as a basic function to use automation in a distributed environment.
This is not new to use a 802.1X supplicant on access devices (like APs) to connect to switchports and use automation for on-/offboarding.
More and more small devices in production, healthcare, education environments for headless devices, IOT/OT force us to deliver an easy to deploy and use environment.
br
Volker
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-23-2021 12:41 PM
Better to use MacSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-19-2021 04:06 PM
Gents,
let’s look forward into the future, not back into the past. HP does it because they have nothing else to do, they missed entire fabric play and BTW now are trying to chase it.
Choosing between implementing 802.1x supplicant and Auto-Sensing feature I'd better have latter.
In the picture from HP manual - what is real world use case? Switch A in uncontrolled environment, where anyone can plug/unplug uplink, and concern is that malicious user can gain access to uplink traffic ? But 802.1x doesn’t solve it. Perhaps HP/Aruba lied to customer about it, but in reality I just need little hub between SwA and SwB - and here you go, I have access to all traffic !
What we can do on EXOS to have similar level of protection - LLDP. configure custom LLDP data, and use UPM port to block port unless you see proper string in LLDP.
But it’s a kludge of course, you should use MACSEC if customer is really concerned about security.
Alex
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-21-2021 03:50 PM
Hello,
since this feature is missing we have just failed to replace 140 HP switches with XOS switches. HP (now Aruba) has supported this feature for years.
Specifically, this is a project where Fiber to the Desk is in use and therefore there is a switch in every office. To prevent an employee from being on the network after unplugging the switch, authentication must also be performed on the uplink, not just on the access.
Here a screenshot from the HP manual
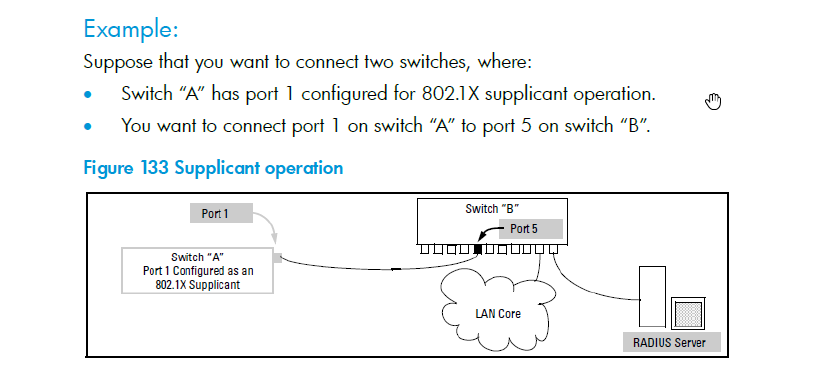
And NO VSP is no option here in the moment for the customer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-22-2020 02:55 PM
Volker, auto-sense does exactly that:
- It turns a port into an NNI when another VSP is connected
- it tuns a port into an FA links if an FA device is connected
- it turns a port into an IP Phone port if an IP phone is detected through LLDP-MED
- it turns a port into a UNI port if non of the above is detected
- as a UNI it can be run without NAC, then all devices end up in the secure guest/onboarding PVLAN 4048, ISID 15999999
- as a UNI with NAC devices can be assigned into their own VLAN/ISID through Radius with MHMV per host (MAC).
- if any of the above devices are removed, then the port turns into default state.
Roger
