- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ Controller
- Re: XCC Dynamic VLAN Assignment
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
XCC Dynamic VLAN Assignment
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-13-2021 11:56 AM
Hi Guys,
I'm working on a customer deployment and got some issues using ExtremeControl and XCC (5.36.03).
If I send RFC3580 Vlan Attributes to XCC from the Control, the 802.1x session from the client can't authenticate, even with the VLAN created under Policy > Vlans and the same vlan associated to the Device Group's Profile.
Taking the "Guest Access" role as example, it is configured on the XCC to use the "Default Network VLAN" (as it is in sync with the policy domain, applied to the wired infrastructure too). I've created the VLAN 40 and marked as Bridge@AP Tagged and associated it with the Device Group's Profile (https://extremeportal.force.com/ExtrArticleDetail?an=000094691),
If I send only the FilterID 'policy=Guest Access' the client, the client get's authenticated, but still on the default WLAN VLAN (120). If I send the VTA attributes as follows, the same client can't authenticate:
Filter-Id=Enterasys:version=1:%MANAGEMENT%policy=%POLICY_NAME%
Login-LAT-Port=%LOGIN_LAT_PORT%
Service-Type=%MGMT_SERV_TYPE%
Tunnel-Private-Group-Id=%VLAN_ID%:%VLAN_TUNNEL_TAG%
Tunnel-Type=13:%VLAN_TUNNEL_TAG%
Tunnel-Medium-Type=6:%VLAN_TUNNEL_TAG%
The policy mapping is done on the Control for the dynamic vlan I want to apply.
Any ideas?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-17-2021 01:32 PM
Hi PeterK,
I've just posted the config where I got issues… In summary: B@AC works perfectly, B@AP don't work. Below follows more info...
As far as I discovered, the Dynamic VLAN assignment works without a "Role-to-VLAN pair" static creation on XCC, using RADIUS VLAN attributes, on B@AC topologies, but is not working o B@AP or FabricAttach topologies, even with the association of the VLANs to the Device Group's profile.
Creating the "Role-to-VLAN pairs" is not an option, as the customer is using a single Policy Domain for Wired and Wireless, and this solutions "would not fit" on the environment. Using B@AC solution is not an option as well.
Best regards,
-Leo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-17-2021 01:08 PM
I think this is a desgin-problem.
It’s always not a good idea to change vlan/ip-net during a active connection.
In this case, the client wired oder wireless needs a trigger to release the IP and Discovery for a new. In wired enviroment this can be triggered by link down and up. But in wireless, I think that shouldn’t be possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-17-2021 12:14 PM
Hi Z,
When I say "can not authenticate" I mean that the initial role applied is UNREGISTERED, and the client can connect to VLAN 1121, get an IP address, is redirected to the NAC's Captive Portal for registration without problems, BUT, after registration, NAC sends the RADIUS ATTRIBUTES including the VLAN atributes for the new Role and VLAN 101 (B@AP Tagged) and the client simply can't connect.
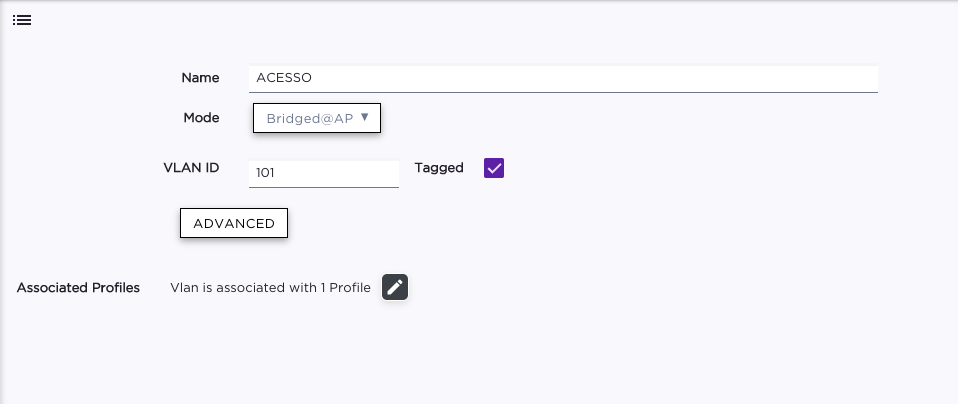
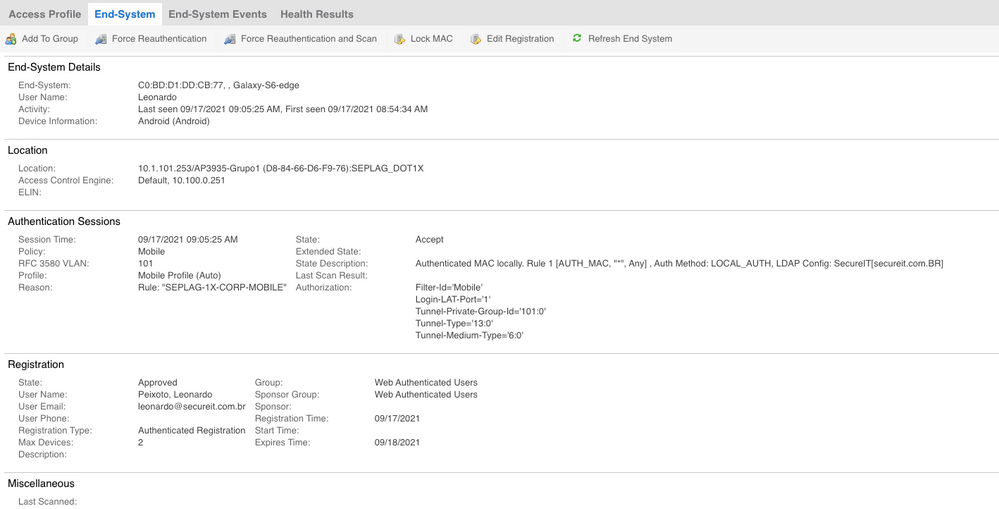
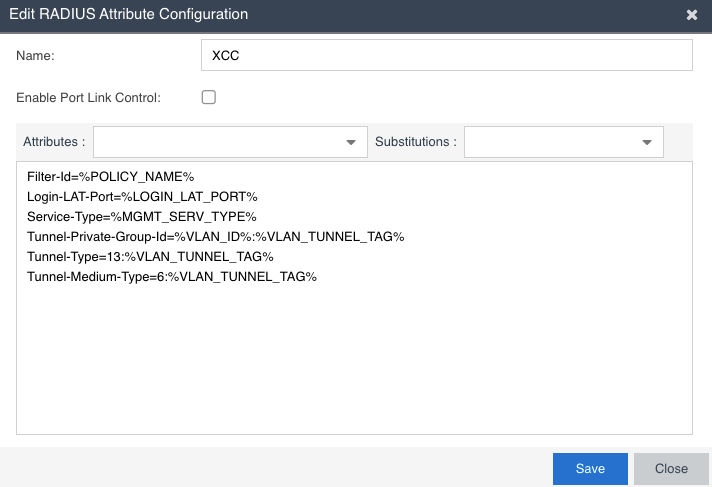
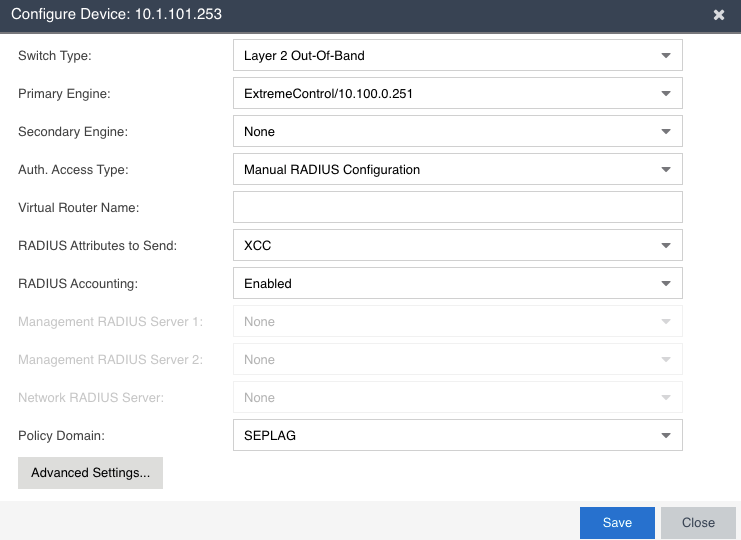
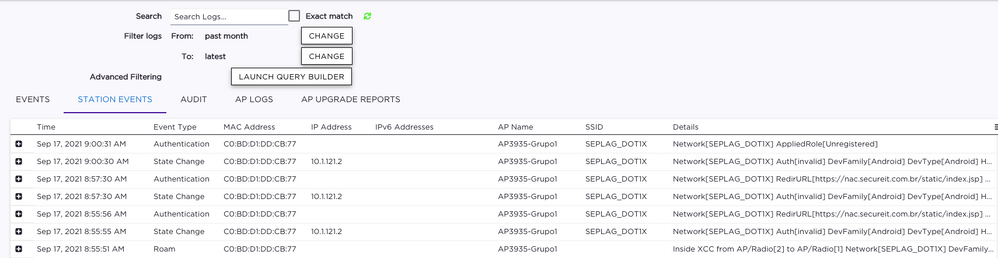
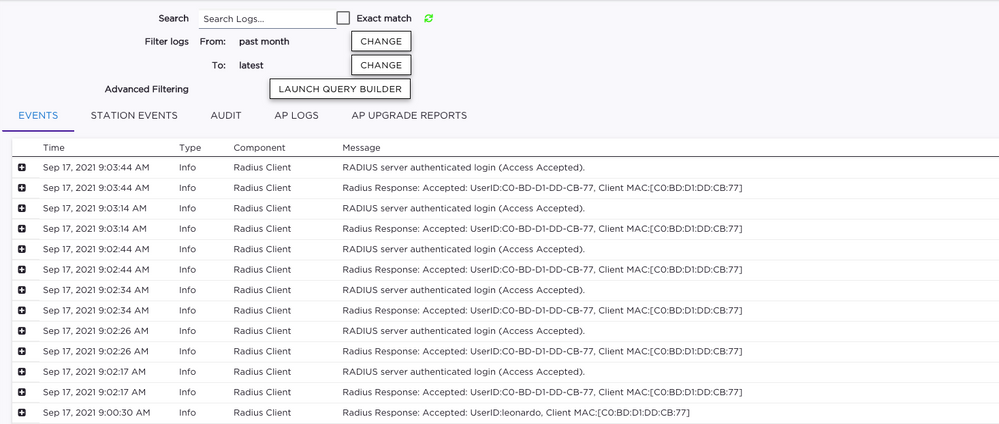
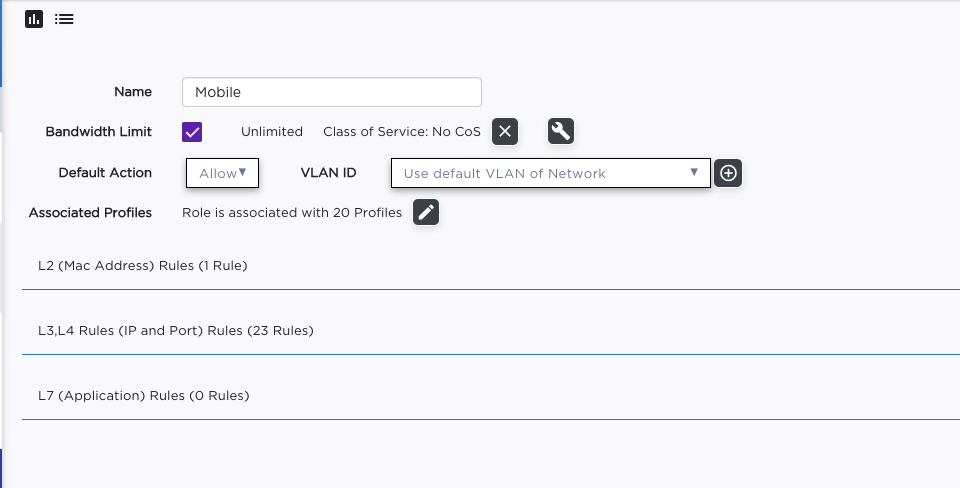
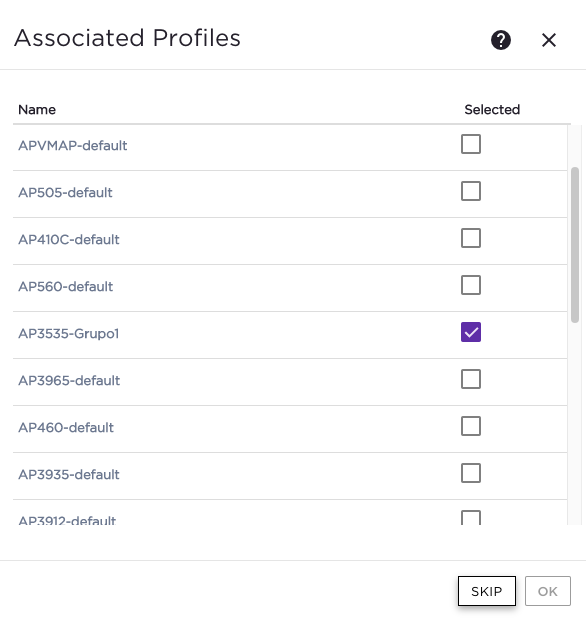
The VLAN is created as B@AP at the XCC and configured on the Switch, as if I set the VLAN on the role statically on the XCC and don't send the VLAN attributes from the NAC it works perfectly.
I haven't asked GTAC yet, because maybe I'm missing something stupid and decided to ask here before bothering the GTAC Guys.
I've just captured some screenshots and an AP Log (because XCC logs are not good, IMHO)
######################## CONNECTING TO THE SEPLAG_DOT1X WLAN AND RECEIVING THE UNREGISTERED POLICY FROM NAC FOR REGISTRATION #########################
Sep 17 11:57:19 krn: ieee80211_mlme.c:445/wlan_mlme_disassoc_request_with_callback()-ath6/C0:BD:D1:DD:CB:77 wlan_vap_is_pmf_enabled=0
Sep 17 11:57:19 krn: ieee80211_mlme.c:499/wlan_mlme_disassoc_request_with_callback()-ath6/C0:BD:D1:DD:CB:77 defer_cleanup=1 ni_pmf=0 key_valid=1
Sep 17 11:57:19 krn: ieee80211_mgmt.c:993/ieee80211_send_disassoc_with_callback()-ath6 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 11:57:19 krn: ieee80211_node_ap.c:274/_ieee80211_node_leave()-ath6/C0:BD:D1:DD:CB:77 stassoc=1 ni=e6e8fee0 aid=1 kvalid=1 keyix=5 ncount=2 tm=88569 rss=-41 refcnt=2 rtChRegUtil=13
Sep 17 11:57:19 krn: ieee80211_node_ap.c:413/_ieee80211_node_leave()-ath6 C0:BD:D1:DD:CB:77 ieee80211_crypto_delkey AID=1
Sep 17 11:57:19 krn: ieee80211_node_ap.c:80/chk_ic_counters()-wifi0 Correcting ht40_sta_assoc! orig=65535 new=0
Sep 17 11:57:19 krn: ieee80211_node_ap.c:81/chk_ic_counters()-wifi0 num_corrected=1
Sep 17 11:57:19 hostapd0: 1631879839.814660: ath6: STA c0:bd:d1:dd:cb:77 IEEE 802.11: disassociated
Sep 17 11:57:23 krn: ieee80211_mgmt_ap.c:1125/ieee80211_recv_asreq()-ni_flags=a rs_nrates=16
Sep 17 11:57:23 krn: ieee80211_node_ap.c:863/ieee80211_node_join()-ath6/C0:BD:D1:DD:CB:77 sta=1 ni=e6e90f90 aid=1 refcnt=2 ncnt=2 rss=-48 mfp=0
Sep 17 11:57:23 krn: ol_if_mgmt.c:720/ol_ath_net80211_newassoc()-C0:BD:D1:DD:CB:77 ni_flags=1000000a ni_wds_tx_policy=0 isnew=1 ni=e6e90f90
Sep 17 11:57:23 krn: ieee80211_mgmt_ap.c:1359/ieee80211_recv_asreq()-exit
Sep 17 11:57:23 hostapd0: 1631879843.486044: ath6: STA c0:bd:d1:dd:cb:77 IEEE 802.11: associated
Sep 17 11:57:23 hostapd0: 1631879843.486137: ath6: STA c0:bd:d1:dd:cb:77 WPA: wpa_validate_wpa_ie776 key_mgmt 01 num_pmkid=0 pmksa=(nil)
Sep 17 11:57:23 hostapd0: 1631879843.486387: ath6: STA c0:bd:d1:dd:cb:77 WPA: wpa_validate_wpa_ie PW_EAP_PMKID_NOTIFY sent to driver
Sep 17 11:57:23 krn: mu_assoc_tab.c:1206/wassp_mu_assoc_handler()-C0:BD:D1:DD:CB:77 ALLOWED
Sep 17 11:57:23 krn: wassp_mu_assoc_decode: C0:BD:D1:DD:CB:77 transId 1631535228 filter name Unregistered rule num 7
Sep 17 11:57:23 krn: wassp_mu_assoc_decode 3323 unicast filter extentions
Sep 17 11:57:23 krn: decodeFilterRulesExtBlock: Optional tlv EID_FILTER_RULE_FIXED_APP_ID not present
Sep 17 11:57:23 krn: decodeFilterRulesExtBlock: Optional tlv EID_FILTER_RULES_APP_SIG_GROUP_ID not present
Sep 17 11:57:23 krn: decodeFilterRulesExtBlock: Optional tlv EID_FILTER_RULES_APP_SIG_DISP_ID not present
Sep 17 11:57:23 krn: decodeFilterRulesExtBlock: Optional tlv EID_IPV6_ADDR not present
Sep 17 11:57:23 krn: mu_assoc_tab.c:3341/wassp_mu_assoc_decode()-decode topo array len 56
Sep 17 11:57:23 krn: decodeTopologyArray 4004 EID_TOPOLOGY_ARRAY TLV len:56
Sep 17 11:57:23 krn: decodeFilterConfigStruct: EID_FILTER_RULES not present
Sep 17 11:57:23 krn: decodeTopologyStruct 3981 success!
Sep 17 11:57:23 krn: decodeTopologyArray: decoding EID_TOPOLOGY_ARRAY success struct count:1
Sep 17 11:57:23 krn: topology array - entry count:1 p:e2200000
Sep 17 11:57:23 krn: topology struct - vlanId:1121 isBridged:yes isTagged:yes isArpProxy:yes
Sep 17 11:57:23 krn: filterName:VLAN-BAP-CORP-Grupo1 ruleCount:0
Sep 17 11:57:23 krn: sessMgmt_utils.c:4317/ssmHandleAC2APMuIP()-RESP has IP=10.1.121.2 old linger node IP=0.0.0.0
Sep 17 11:57:23 krn: chantry_arppxy_node.c:143/chantry_arppxy_node_add_ipv4()-Setting c0:bd:d1:dd:cb:77 10.1.121.2
Sep 17 11:57:23 krn: wassp_mu_assoc_decode: Success: chantry6: apply filter Unregistered with 7 rules
Sep 17 11:57:23 krn: mu_assoc_tab.c:3509/wassp_mu_assoc_decode()-li_vlanid_count 1 li_controller_vlanid_count 0
Sep 17 11:57:23 krn: dev_ident_drv.c:92/devIdentUpdateLiAndSiteSess()-C0:BD:D1:DD:CB:77 devIdent old 0 0 0 new 290 104 15
Sep 17 11:57:23 krn: [19/1] FWLOG: [84827658] RATE: ChainMask 3, peer_mac cb:77, phymode 8, ni_flags 0x02211006, vht_mcs_set 0xfffa, ht_mcs_set 0xffff, legacy_rate_set 0x0ff0
Sep 17 11:57:23 krn: [31/5] FWLOG: [84827659] RTT_REPORT ( 0x2804, 0x3, 0x479, 0x0, 0x9 )
Sep 17 11:57:29 krn: wassp_mu_update_handler 2404
Sep 17 11:57:29 krn: decodeFilterRulesExtBlock: Optional tlv EID_FILTER_RULE_FIXED_APP_ID not present
Sep 17 11:57:29 krn: decodeFilterRulesExtBlock: Optional tlv EID_FILTER_RULES_APP_SIG_GROUP_ID not present
Sep 17 11:57:29 krn: decodeFilterRulesExtBlock: Optional tlv EID_FILTER_RULES_APP_SIG_DISP_ID not present
Sep 17 11:57:29 krn: decodeFilterRulesExtBlock: Optional tlv EID_IPV6_ADDR not present
Sep 17 11:57:29 krn: decodeTopologyArray 4004 EID_TOPOLOGY_ARRAY TLV len:56
Sep 17 11:57:29 krn: decodeFilterConfigStruct: EID_FILTER_RULES not present
Sep 17 11:57:29 krn: decodeTopologyStruct 3981 success!
Sep 17 11:57:29 krn: decodeTopologyArray: decoding EID_TOPOLOGY_ARRAY success struct count:1
Sep 17 11:57:29 krn: topology array - entry count:1 p:e2200000
Sep 17 11:57:29 krn: topology struct - vlanId:1121 isBridged:yes isTagged:yes isArpProxy:yes
Sep 17 11:57:29 krn: filterName:VLAN-BAP-CORP-Grupo1 ruleCount:0
Sep 17 11:57:29 krn: mu_assoc_tab.c:2592/wassp_mu_update_handler()-chantry6 C0:BD:D1:DD:CB:77 filterName: "Unregistered" numRule 7
Sep 17 11:57:29 hostapd0: 1631879849.972798: ath6: STA c0:bd:d1:dd:cb:77 WPA: pairwise key handshake completed (RSN)
Sep 17 11:57:29 hostapd0: 1631879849.972860: ====> AUTHENTICATED sm_AUTH_PAE_AUTHENTICATED_Enter 342
Sep 17 11:57:29 hostapd0: 1631879849.972860: ====> sm_AUTH_PAE_AUTHENTICATED_Enter 343 sm->eap_type_supp 25 eap_type_authsrv 0
Sep 17 11:57:29 hostapd0: 1631879849.972860: ====> MAC: c0:bd:d1:dd:cb:77
Sep 17 11:57:29 hostapd0: 1631879849.973016: ath6: STA c0:bd:d1:dd:cb:77 IEEE 802.1X: authenticated - EAP type: 0 (unknown)
Sep 17 11:57:29 krn: ieee80211_wireless.c:9160/ieee80211_ioctl_setkey()-ath6 C0:BD:D1:DD:CB:77 keyix=65535
Sep 17 11:57:29 krn: ieee80211_wireless.c:9301/ieee80211_ioctl_setkey()-ath6 C0:BD:D1:DD:CB:77 error=0 keytype=3 keylen=16 keyix=65535
Sep 17 11:57:29 krn: m2MsgApp_TaskletHandler 425 hapd-->tsk-->AP OP_TASKLET_APP_HAPD_AUTH_TYPE from srcTid:36
Sep 17 11:57:29 krn: m3TaskHdlr.c:362/tskHdlr_muAuthType()-C0:BD:D1:DD:CB:77, eap type 25
Sep 17 11:57:29 krn: m3TaskHdlr.c:366/tskHdlr_muAuthType()-c0:bd:d1:dd:cb:77, size 1152
Sep 17 11:57:30 krn: [22/27] FWLOG: [84834297] WAL_DBGID_SECURITY_UCAST_KEY_SET ( 0xcb77, 0x0 )
Sep 17 11:57:30 krn: [22/29] FWLOG: [84834297] WAL_DBGID_SECURITY_ENCR_EN ( )
Sep 17 11:57:30 krn: [22/26] FWLOG: [84834297] WAL_DBGID_SECURITY_ALLOW_DATA ( 0x443ba4 )
Sep 17 11:57:30 krn: [22/35] FWLOG: [84834605] WAL_DBGID_TX_BA_SETUP ( 0x443ba4, 0xcb770006, 0xf, 0x40, 0x1 )
Sep 17 11:57:30 krn: [19/1] FWLOG: [84834606] RATE: ChainMask 3, peer_mac cb:77, phymode 10, ni_flags 0x02211006, vht_mcs_set 0xfffa, ht_mcs_set 0xffff, legacy_rate_set 0x0ff0
Sep 17 11:57:31 krn: [22/35] FWLOG: [84835061] WAL_DBGID_TX_BA_SETUP ( 0x443ba4, 0xcb770000, 0x0, 0x40, 0x1 )
Sep 17 11:57:33 cap: __delta__ deltaCounterUpdate 330 lastRead:0x8589934748 newRead:0x81 32bit roll over:0x200000000!!!
Sep 17 11:57:33 cap: __delta__ deltaCounterUpdate 330 lastRead:0x8589934709 newRead:0x57 32bit roll over:0x200000000!!!
Sep 17 11:57:33 cap: __delta__ deltaCounterUpdate 330 lastRead:0x8589966690 newRead:0x11416 32bit roll over:0x200000000!!!
Sep 17 11:57:33 cap: __delta__ deltaCounterUpdate 330 lastRead:0x8589979112 newRead:0x15121 32bit roll over:0x200000000!!!
Sep 17 11:57:33 cap: __delta__ muDeltaEntryEncode 3964 radio mismatch calling:0 map:1 C0:BD:D1:DD:CB:77
Sep 17 11:57:39 krn: vap-8(ath18):ieee80211_send_nulldata[356] cur chan 11 flags 0x10080 is not same as home chan 1 flags 0xa0
Sep 17 11:57:39 krn: vap-8(ath8):ieee80211_send_nulldata[356] cur chan 149 flags 0x100100 is not same as home chan 36 flags 0x140
################ CLIENT REDIRECTED TO THE NAC PORTAL FOR REGISTRATION... REGISTERING ########################
Sep 17 11:58:03 cap: __delta__ muDeltaEntryEncode 3964 radio mismatch calling:0 map:1 C0:BD:D1:DD:CB:77
Sep 17 11:58:30 sensor: excessive dpi packets, 20+21, from 10.1.121.2(45648) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:58:30 sensor: excessive dpi packets, 20+21, from 10.1.121.2(45647) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:58:30 sensor: excessive dpi packets, 19+21, from 10.1.121.2(45646) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:58:30 sensor: excessive dpi packets, 20+19, from 10.1.121.2(45645) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:58:30 sensor: excessive dpi packets, 19+21, from 10.1.121.2(45644) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:58:30 sensor: excessive dpi packets, 18+21, from 10.1.121.2(45641) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:58:33 cap: __delta__ muDeltaEntryEncode 3964 radio mismatch calling:0 map:1 C0:BD:D1:DD:CB:77
Sep 17 11:59:01 timesync: TIMESERVER=pool.ntp.org AP_MODE=0 DISCOV_MODE="On-Prem"
Sep 17 11:59:03 cap: __delta__ muDeltaEntryEncode 3964 radio mismatch calling:0 map:1 C0:BD:D1:DD:CB:77
Sep 17 11:59:33 cap: __delta__ muDeltaEntryEncode 3964 radio mismatch calling:0 map:1 C0:BD:D1:DD:CB:77
Sep 17 11:59:45 sensor: excessive dpi packets, 18+21, from 10.1.121.2(45665) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:59:45 sensor: excessive dpi packets, 20+19, from 10.1.121.2(45664) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:59:45 sensor: excessive dpi packets, 21+20, from 10.1.121.2(45663) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:59:45 sensor: excessive dpi packets, 18+16, from 10.1.121.2(45662) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:59:45 sensor: excessive dpi packets, 18+21, from 10.1.121.2(45661) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 11:59:45 sensor: excessive dpi packets, 21+18, from 10.1.121.2(45648) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 12:00:03 cap: __delta__ muDeltaEntryEncode 3964 radio mismatch calling:0 map:1 C0:BD:D1:DD:CB:77
Sep 17 12:00:31 krn: wassp_mu_update_handler 2404
Sep 17 12:00:31 krn: decodeFilterRulesExtBlock: Optional tlv EID_FILTER_RULE_FIXED_APP_ID not present
Sep 17 12:00:31 krn: decodeFilterRulesExtBlock: Optional tlv EID_FILTER_RULES_APP_SIG_GROUP_ID not present
Sep 17 12:00:31 krn: decodeFilterRulesExtBlock: Optional tlv EID_FILTER_RULES_APP_SIG_DISP_ID not present
Sep 17 12:00:31 krn: decodeFilterRulesExtBlock: Optional tlv EID_IPV6_ADDR not present
Sep 17 12:00:31 krn: decodeTopologyArray 4004 EID_TOPOLOGY_ARRAY TLV len:56
Sep 17 12:00:31 krn: decodeFilterConfigStruct: EID_FILTER_RULES not present
Sep 17 12:00:31 krn: decodeTopologyStruct 3981 success!
Sep 17 12:00:31 krn: decodeTopologyArray: decoding EID_TOPOLOGY_ARRAY success struct count:1
Sep 17 12:00:31 krn: topology array - entry count:1 p:e2200000
Sep 17 12:00:31 krn: topology struct - vlanId:1121 isBridged:yes isTagged:yes isArpProxy:yes
Sep 17 12:00:31 krn: filterName:VLAN-BAP-CORP-Grupo1 ruleCount:0
Sep 17 12:00:31 krn: mu_assoc_tab.c:2592/wassp_mu_update_handler()-chantry6 C0:BD:D1:DD:CB:77 filterName: "Unregistered" numRule 7
Sep 17 12:00:31 hostapd0: 1631880031.103882: ====> AUTHENTICATED sm_AUTH_PAE_AUTHENTICATED_Enter 342
Sep 17 12:00:31 hostapd0: 1631880031.103913: ====> sm_AUTH_PAE_AUTHENTICATED_Enter 343 sm->eap_type_supp 25 eap_type_authsrv 0
Sep 17 12:00:31 hostapd0: 1631880031.103944: ====> MAC: c0:bd:d1:dd:cb:77
Sep 17 12:00:31 hostapd0: 1631880031.104069: ath6: STA c0:bd:d1:dd:cb:77 IEEE 802.1X: authenticated - EAP type: 0 (unknown)
Sep 17 12:00:31 krn: m2MsgApp_TaskletHandler 425 hapd-->tsk-->AP OP_TASKLET_APP_HAPD_AUTH_TYPE from srcTid:36
Sep 17 12:00:31 krn: m3TaskHdlr.c:362/tskHdlr_muAuthType()-C0:BD:D1:DD:CB:77, eap type 25
Sep 17 12:00:31 krn: m3TaskHdlr.c:366/tskHdlr_muAuthType()-c0:bd:d1:dd:cb:77, size 1152
Sep 17 12:00:32 hostapd0: 1631880032.755866: ath6: STA c0:bd:d1:dd:cb:77 WPA: pairwise key handshake completed (RSN)
Sep 17 12:00:32 krn: ieee80211_wireless.c:9160/ieee80211_ioctl_setkey()-ath6 C0:BD:D1:DD:CB:77 keyix=65535
Sep 17 12:00:32 krn: ieee80211_wireless.c:9301/ieee80211_ioctl_setkey()-ath6 C0:BD:D1:DD:CB:77 error=0 keytype=3 keylen=16 keyix=65535
Sep 17 12:00:33 cap: __delta__ muDeltaEntryEncode 3964 radio mismatch calling:0 map:1 C0:BD:D1:DD:CB:77
Sep 17 12:00:33 krn: [22/27] FWLOG: [85021367] WAL_DBGID_SECURITY_UCAST_KEY_SET ( 0xcb77, 0x0 )
Sep 17 12:00:33 krn: [22/29] FWLOG: [85021367] WAL_DBGID_SECURITY_ENCR_EN ( )
Sep 17 12:00:33 krn: [22/26] FWLOG: [85021367] WAL_DBGID_SECURITY_ALLOW_DATA ( 0x443ba4 )
Sep 17 12:01:00 sensor: excessive dpi packets, 21+20, from 10.1.121.2(45692) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 12:01:00 sensor: excessive dpi packets, 17+20, from 10.1.121.2(45691) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 12:01:00 sensor: excessive dpi packets, 22+21, from 10.1.121.2(45690) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 12:01:00 sensor: excessive dpi packets, 18+24, from 10.1.121.2(45648) -> 10.100.0.251(443), TCP, dir=0 , displayId=0, are ignored
Sep 17 12:02:03 cap: __delta__ muDeltaEntryEncode 3964 radio mismatch calling:0 map:1 C0:BD:D1:DD:CB:77
############### CLIENT DEVICE REGISTERED, SHOULD RECEIVE ROLE MOBILE AND VLAN 101 B@AP TAGGED ###############
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 cap: 01123:wassp_prot_input.c:1586/wassp_mu_discon_handler()-C0:BD:D1:DD:CB:77 EID_STATUS="DAS_REQ" (15)
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath0 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath0 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath3 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath3 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath4 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath4 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath5 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath5 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath6 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: chantry_export.c:2792/chantry_domlme()-DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: ieee80211_mlme.c:445/wlan_mlme_disassoc_request_with_callback()-ath6/C0:BD:D1:DD:CB:77 wlan_vap_is_pmf_enabled=0
Sep 17 12:02:10 cap: wlanDisconnectClientsR: C0:BD:D1:DD:CB:77, cat VNS_CAT_ALL
Sep 17 12:02:10 cap: Send 22 bytes mu cb 77 disconnect response data to AC
Sep 17 12:02:10 krn: ieee80211_mlme.c:499/wlan_mlme_disassoc_request_with_callback()-ath6/C0:BD:D1:DD:CB:77 defer_cleanup=1 ni_pmf=0 key_valid=1
Sep 17 12:02:10 krn: ieee80211_mgmt.c:993/ieee80211_send_disassoc_with_callback()-ath6 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath7 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath7 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath10 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath10 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath13 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath13 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath14 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath14 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath15 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath15 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath16 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath16 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: chantry_ext_ioctl.c:412/ioctl_kickmacbyattr()-ath17 DISASSOC C0:BD:D1:DD:CB:77 reason=8
Sep 17 12:02:10 krn: Skipping domlme for STA C0:BD:D1:DD:CB:77 (li->li_vap->io_dev ath6 != vns ath17 ) (li->li_vap->dev: chantry6)
Sep 17 12:02:10 krn: ieee80211_node_ap.c:274/_ieee80211_node_leave()-ath6/C0:BD:D1:DD:CB:77 stassoc=1 ni=e6e90f90 aid=1 kvalid=1 keyix=5 ncount=2 tm=286776 rss=-41 refcnt=2 rtChRegUtil=14
Sep 17 12:02:10 krn: ieee80211_node_ap.c:413/_ieee80211_node_leave()-ath6 C0:BD:D1:DD:CB:77 ieee80211_crypto_delkey AID=1
Sep 17 12:02:10 krn: ieee80211_node_ap.c:80/chk_ic_counters()-wifi0 Correcting ht40_sta_assoc! orig=65535 new=0
Sep 17 12:02:10 krn: ieee80211_node_ap.c:81/chk_ic_counters()-wifi0 num_corrected=1
Sep 17 12:02:10 hostapd0: 1631880130.261770: ath6: STA c0:bd:d1:dd:cb:77 IEEE 802.11: disassociated
Sep 17 12:02:17 krn: ieee80211_mgmt_ap.c:1125/ieee80211_recv_asreq()-ni_flags=a rs_nrates=16
Sep 17 12:02:17 krn: ieee80211_node_ap.c:863/ieee80211_node_join()-ath6/C0:BD:D1:DD:CB:77 sta=1 ni=e6e92040 aid=1 refcnt=2 ncnt=2 rss=-47 mfp=0
Sep 17 12:02:17 krn: ol_if_mgmt.c:720/ol_ath_net80211_newassoc()-C0:BD:D1:DD:CB:77 ni_flags=1000000a ni_wds_tx_policy=0 isnew=1 ni=e6e92040
Sep 17 12:02:17 krn: ieee80211_mgmt_ap.c:1359/ieee80211_recv_asreq()-exit
Sep 17 12:02:17 hostapd0: 1631880137.432373: ath6: STA c0:bd:d1:dd:cb:77 IEEE 802.11: associated
Sep 17 12:02:17 hostapd0: 1631880137.432435: ath6: STA c0:bd:d1:dd:cb:77 WPA: wpa_validate_wpa_ie776 key_mgmt 01 num_pmkid=1 pmksa=(nil)
Sep 17 12:02:17 hostapd0: 1631880137.432685: ath6: STA c0:bd:d1:dd:cb:77 WPA: wpa_validate_wpa_ie PW_EAP_PMKID_NOTIFY sent to driver
Sep 17 12:02:17 krn: mu_assoc_tab.c:1206/wassp_mu_assoc_handler()-C0:BD:D1:DD:CB:77 Not allowed
Sep 17 12:02:17 krn: mu_assoc_tab.c:1215/wassp_mu_assoc_handler()-chantry6 C0:BD:D1:DD:CB:77 DEAUTHed from ASSOC RSP! status=0
Sep 17 12:02:17 krn: chantry_export.c:2310/madwifi_send_deauth_imp()-chantry6/C0:BD:D1:DD:CB:77 reason=9
Sep 17 12:02:17 hostapd0: 1631880137.454678: ath6: STA c0:bd:d1:dd:cb:77 IEEE 802.11: disassociated
Sep 17 12:02:17 krn: chantry_export.c:2338/madwifi_send_deauth_imp()-chantry6 wireless_handlers is NULL, will try to convert to a chantry device...
Sep 17 12:02:17 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:17 krn: chantry_export.c:2353/madwifi_send_deauth_imp()-Deauthing C0:BD:D1:DD:CB:77 on ath6
Sep 17 12:02:17 krn: ieee80211_wireless.c:2781/ieee80211_ioctl_setmlme()-ath6 DISASSOC/DEAUTH! C0:BD:D1:DD:CB:77 op=3
Sep 17 12:02:17 krn: ieee80211_wireless.c:2823/ieee80211_ioctl_setmlme()-ath6/C0:BD:D1:DD:CB:77 ATH_SUPPORT_DEFERRED_NODE_CLEANUP!
Sep 17 12:02:17 krn: ieee80211_mlme.c:445/wlan_mlme_disassoc_request_with_callback()-ath6/C0:BD:D1:DD:CB:77 wlan_vap_is_pmf_enabled=0
Sep 17 12:02:17 krn: ieee80211_mlme.c:499/wlan_mlme_disassoc_request_with_callback()-ath6/C0:BD:D1:DD:CB:77 defer_cleanup=1 ni_pmf=0 key_valid=0
Sep 17 12:02:17 krn: ieee80211_mgmt.c:993/ieee80211_send_disassoc_with_callback()-ath6 DISASSOC C0:BD:D1:DD:CB:77 reason=9
Sep 17 12:02:17 krn: ieee80211_wireless.c:2835/ieee80211_ioctl_setmlme()-DISASSOC rc=0
Sep 17 12:02:17 krn: ieee80211_node_ap.c:274/_ieee80211_node_leave()-ath6/C0:BD:D1:DD:CB:77 stassoc=1 ni=e6e92040 aid=1 kvalid=0 keyix=65535 ncount=2 tm=22 rss=-47 refcnt=2 rtChRegUtil=11
Sep 17 12:02:17 krn: ieee80211_node_ap.c:80/chk_ic_counters()-wifi0 Correcting ht40_sta_assoc! orig=65535 new=0
Sep 17 12:02:17 krn: ieee80211_node_ap.c:81/chk_ic_counters()-wifi0 num_corrected=1
Sep 17 12:02:17 krn: [19/1] FWLOG: [85128501] RATE: ChainMask 3, peer_mac cb:77, phymode 8, ni_flags 0x02211006, vht_mcs_set 0xfffa, ht_mcs_set 0xffff, legacy_rate_set 0x0ff0
Sep 17 12:02:17 krn: [31/5] FWLOG: [85128501] RTT_REPORT ( 0x2804, 0x3, 0x479, 0x0, 0x9 )
Sep 17 12:02:26 krn: ieee80211_mgmt_ap.c:1125/ieee80211_recv_asreq()-ni_flags=a rs_nrates=16
Sep 17 12:02:26 krn: ieee80211_node_ap.c:863/ieee80211_node_join()-ath6/C0:BD:D1:DD:CB:77 sta=1 ni=e6e930f0 aid=1 refcnt=2 ncnt=2 rss=-44 mfp=0
Sep 17 12:02:26 krn: ol_if_mgmt.c:720/ol_ath_net80211_newassoc()-C0:BD:D1:DD:CB:77 ni_flags=1000000a ni_wds_tx_policy=0 isnew=1 ni=e6e930f0
Sep 17 12:02:26 krn: ieee80211_mgmt_ap.c:1359/ieee80211_recv_asreq()-exit
Sep 17 12:02:26 hostapd0: 1631880146.437465: ath6: STA c0:bd:d1:dd:cb:77 IEEE 802.11: associated
Sep 17 12:02:26 hostapd0: 1631880146.437528: ath6: STA c0:bd:d1:dd:cb:77 WPA: wpa_validate_wpa_ie776 key_mgmt 01 num_pmkid=1 pmksa=(nil)
Sep 17 12:02:26 hostapd0: 1631880146.437777: ath6: STA c0:bd:d1:dd:cb:77 WPA: wpa_validate_wpa_ie PW_EAP_PMKID_NOTIFY sent to driver
Sep 17 12:02:26 krn: mu_assoc_tab.c:1206/wassp_mu_assoc_handler()-C0:BD:D1:DD:CB:77 Not allowed
Sep 17 12:02:26 krn: mu_assoc_tab.c:1215/wassp_mu_assoc_handler()-chantry6 C0:BD:D1:DD:CB:77 DEAUTHed from ASSOC RSP! status=0
Sep 17 12:02:26 krn: chantry_export.c:2310/madwifi_send_deauth_imp()-chantry6/C0:BD:D1:DD:CB:77 reason=9
Sep 17 12:02:26 krn: chantry_export.c:2338/madwifi_send_deauth_imp()-chantry6 wireless_handlers is NULL, will try to convert to a chantry device...
Sep 17 12:02:26 krn: chantry_export.c:2353/madwifi_send_deauth_imp()-Deauthing C0:BD:D1:DD:CB:77 on ath6
Sep 17 12:02:26 krn: ieee80211_wireless.c:2781/ieee80211_ioctl_setmlme()-ath6 DISASSOC/DEAUTH! C0:BD:D1:DD:CB:77 op=3
Sep 17 12:02:26 krn: ieee80211_wireless.c:2823/ieee80211_ioctl_setmlme()-ath6/C0:BD:D1:DD:CB:77 ATH_SUPPORT_DEFERRED_NODE_CLEANUP!
Sep 17 12:02:26 krn: ieee80211_mlme.c:445/wlan_mlme_disassoc_request_with_callback()-ath6/C0:BD:D1:DD:CB:77 wlan_vap_is_pmf_enabled=0
Sep 17 12:02:26 krn: ieee80211_mlme.c:499/wlan_mlme_disassoc_request_with_callback()-ath6/C0:BD:D1:DD:CB:77 defer_cleanup=1 ni_pmf=0 key_valid=0
Sep 17 12:02:26 krn: ieee80211_mgmt.c:993/ieee80211_send_disassoc_with_callback()-ath6 DISASSOC C0:BD:D1:DD:CB:77 reason=9
Sep 17 12:02:26 krn: ieee80211_wireless.c:2835/ieee80211_ioctl_setmlme()-DISASSOC rc=0
Sep 17 12:02:26 hostapd0: 03897:chantry_client.c:455/ieee8021x_purge_pmk_allhostapd()-EAP PURGE cb 77 at hapd f9 76
Sep 17 12:02:26 krn: ieee80211_node_ap.c:274/_ieee80211_node_leave()-ath6/C0:BD:D1:DD:CB:77 stassoc=1 ni=e6e930f0 aid=1 kvalid=0 keyix=65535 ncount=2 tm=65 rss=-44 refcnt=2 rtChRegUtil=11
Sep 17 12:02:26 krn: ieee80211_node_ap.c:80/chk_ic_counters()-wifi0 Correcting ht40_sta_assoc! orig=65535 new=0
Sep 17 12:02:26 krn: ieee80211_node_ap.c:81/chk_ic_counters()-wifi0 num_corrected=1
Sep 17 12:02:26 hostapd0: 1631880146.502476: ath6: STA c0:bd:d1:dd:cb:77 IEEE 802.11: disassociated
Sep 17 12:02:26 krn: [19/1] FWLOG: [85137717] RATE: ChainMask 3, peer_mac cb:77, phymode 8, ni_flags 0x02211006, vht_mcs_set 0xfffa, ht_mcs_set 0xffff, legacy_rate_set 0x0ff0
Sep 17 12:02:26 krn: [31/5] FWLOG: [85137718] RTT_REPORT ( 0x2804, 0x3, 0x479, 0x0, 0x9 )
################## CLIENT CANT CONNECT ###################
Follows attached some screenshots about my config.
Best regards,
-Leo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-17-2021 06:39 AM
Hi Leo.
probably a stupid question. When you say “can not authenticate” do you refer to the Client state in XCC or to the windows response?
Is the VLAN configured on the switch where the AP is connected? I mean is the L2 path correct?
Another idea: do you have the B@AP topology created in XCC?
Another idea: Have you asked GTAC?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-14-2021 08:01 PM
Hi Guys,
Running more tests, I could find that the VLAN Attributes only work for B@AC Topologies, but not for B@AP.
Maybe I'm still missing something, or there's any "magic trick".
Any ideas?
Best regards,
-Leo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
09-14-2021 12:18 PM
Hi Ovais,
I've just tested your suggestion, but it's not working for me, and now I think I figured out the pinpointed scenario.
The tip about the policy mapping based on location worked perfectly (I never had tested it before, awesome), BUT, when I choose the RADIUS Attributes to send, the client just can't connect, even the NAC sending the attributes…
I've discovered that the config you suggested worked perfectly when I send a Bridge@AC VLAN configured on the XCC, BUT, when I send a BRIDGE@AP VLAN, it doesn't work, even if the VLAN is created on XCC and added to the Device Group's Profile (unchecking the "Additional" don't work as well… I don't know why the SECUREIT Vlan shows as REFERENCED, because it is not configured on any WLAN, ROLE, etc).
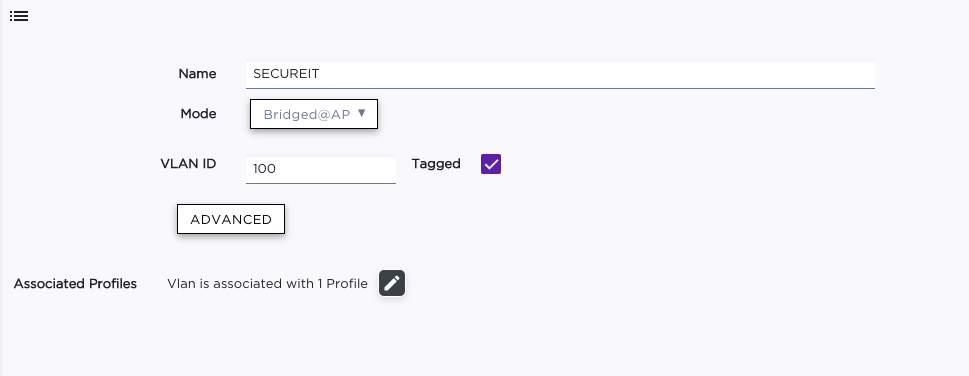
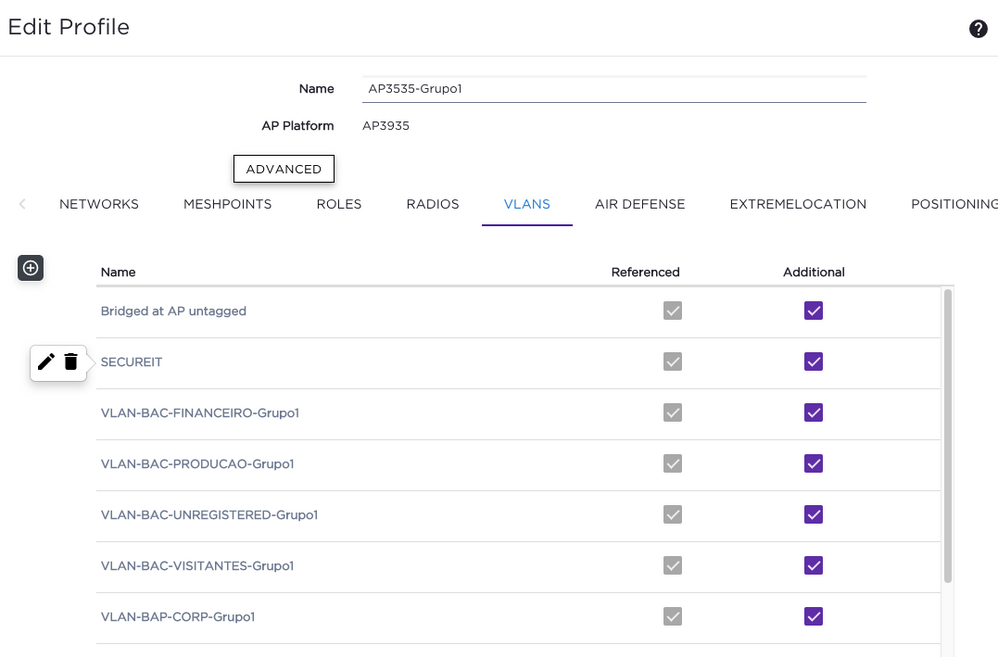
Best regards,
-Leo
