- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: 802.1x clients transition to MAC auth and back...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
802.1x clients transition to MAC auth and back again, every hour?
802.1x clients transition to MAC auth and back again, every hour?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-25-2020 03:47 PM
Hi There,
Hoping someone can help me explain the behaviour below and say either if it is normal or a means to correct it.
It seems that every hour a re-authentication of 802.1x is triggered, that process initially introduces a MAC auth that temporarily hits the default catch all rule that we have yet to flip into a deny rule.
After that it then re-authenticates correctly using EAP-TLS until the next hour?
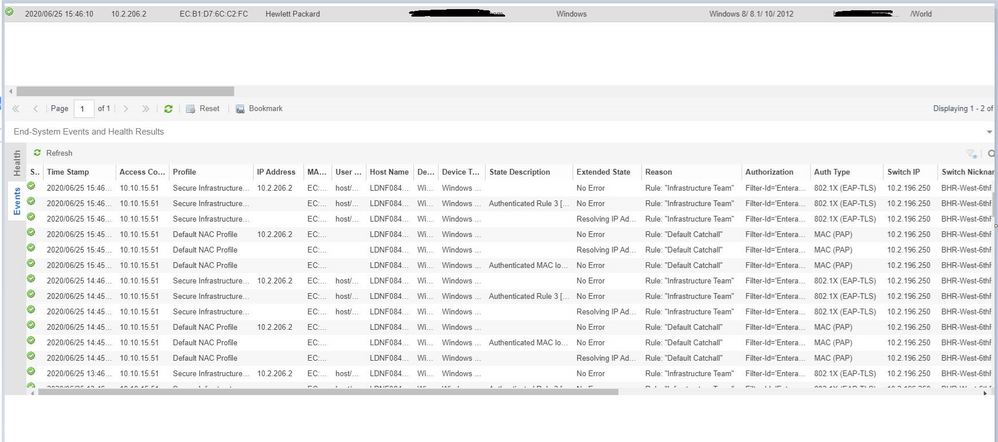
Many thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-29-2020 03:53 PM
Only one session is applied. The default behavior is that MACauth is not applied if 802.1x is applied.
Are you sure there is a macauth authorization applied during the Dot1x reauth?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-25-2020 09:50 PM
Wonder if the answer is in this thread where Zdenek mentions IMHO.
Possibly it is just the end-system going through its steps of re-auth which will include a MAC auth and I’m required to add a rule that will deny it for some reason.
Maybe when the default catch all rule is moved to deny this will help?
Maybe it doesn’t matter?
I imagine there would be a slight drop in service at that time as the policy roles shift?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-25-2020 09:38 PM
Hi Brian,
Thanks for answering.
Yes, it is wired and both MAC and 802.1x are set to re-auth at 3600 seconds, which I expected would explain the 1 hour, and the cycle it goes for that configuration could be natural?
It doesn’t seem efficient or possibly correct switching between authentication methods and temporarily , albeit briefly, move to a catchall rule because of it.
The port has both a PC that is .1x capable and a phone that isn’t, hence both.
If that catch all rule was a deny / reject rule I’m not sure what the result would be?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-25-2020 07:51 PM
Is this wired? If so, do you have reauth settings setup on your ports for every hour?
