- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: 802.1x clients transition to MAC auth and back...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
802.1x clients transition to MAC auth and back again, every hour?
802.1x clients transition to MAC auth and back again, every hour?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-25-2020 03:47 PM
Hi There,
Hoping someone can help me explain the behaviour below and say either if it is normal or a means to correct it.
It seems that every hour a re-authentication of 802.1x is triggered, that process initially introduces a MAC auth that temporarily hits the default catch all rule that we have yet to flip into a deny rule.
After that it then re-authenticates correctly using EAP-TLS until the next hour?
Many thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-29-2020 09:28 PM
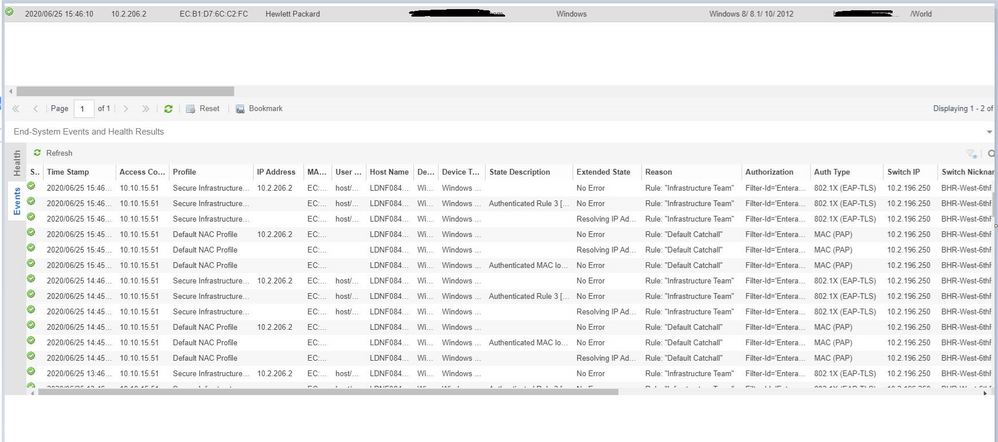
So decided to watch the netlogin session on the switch.
The cycle in the end-system events seems to be:
- Shows authenticated with 802.1x for 1hr
- Switches to showing authenticated with MAC for 19 mins
- Cycle starts again
I watched the whole process and the below session remained the same throughout:
Slot-1 BHR-East-2ndFlr.2 # show netlogin session mac-address ec:b1:d7:6c:94:f8
Multiple authentication session entries
---------------------------------------
Port : 1:5 Station address : ec:b1:d7:6c:94:f8
Auth status : success Last attempt : Sat Jun 27 04:16:19 2020
Agent type : dot1x Session applied : true
Server type : radius VLAN-Tunnel-Attr : None
Policy index : 11 Policy name : Allow All Data (active)
Session timeout : 0 Session duration : 2 days, 16:41:25
Idle timeout : 300 Idle time : 0:00:00
Auth-Override : disabled Termination time : Not Terminated
Port : 1:5 Station address : ec:b1:d7:6c:94:f8
Auth status : success Last attempt : Mon Mar 9 10:54:53 2020
Agent type : mac Session applied : false
Server type : radius VLAN-Tunnel-Attr : None
Policy index : 16 Policy name : Enterprise User (active)
Session timeout : 0 Session duration : 112 days, 10:02:51
Idle timeout : 300 Idle time : 0:00:00
Auth-Override : disabled Termination time : Not Terminated
The station address is showing auth status success for both MAC and 802.1x, with 802.1x taking precedence.
The policy name Enterprise User is whats being assigned by the currently permit Default Catch All rule. Soon this will be disabled, so should show up denied.
The end-system events seemed to show up as the following sequence:
- On the hour the first two lines of MAC(PAP) showed up
- 19 minutes later the 3rd MAC(PAP) lined showed that includes the IP address
- Straight after the 3 lines of 802.1x(EAP-TLS) showed up
So it seems to conclude that the actual session for the device on the switch never changes, so begs the question why XMC is showing otherwise?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-29-2020 06:11 PM
I’ve attached the full detail of the End-System events.
This same pattern is happening on every 802.1x client by the way, but it does on the surface seem to show it legitimately going through a MAC auth, being accepted via the Default Catch All NAC rule.
Need to back this up I guess, by seeing if this mirrors whats happening on the switch also?
There is no reject being applied for MAC auth devices at this time, the tap hasn’t yet been turned off i.e. the Default Catch All rule is still set with the Default NAC Profile that is permit - would that have anything to do with it? Must the device hit some kind of reject on MAC auth?
Still, can’t explain why a 802.1x client will show a MAC authentication?
All the PC’s have had sleep mode disabled via GPO, so that’s not it?
Worth me opening a case?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-29-2020 05:30 PM
Hi Z,
Ok, let me validate the MAC session is actually rejected or disconnected as that screenshot isn’t showing the whole picture.
Will try and post back shortly.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-29-2020 05:24 PM
Hi Martin.
in the ES table you will not see the change = you should not see the change in the switch either.
in the ES history table you should see everything what happens = for auditing and debugging purpose.
example what you can see:
- the ES table is authenticated and “accept” for 802.1X
- in the ES history you can see the authentication is rejected or even disconnected for the mac auth session
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-29-2020 04:08 PM
Hi Zdenek,
Thanks for replying.
Answer is, no, I’m not sure. Just seeing the results as in the End-System events as shown above and wondering:
- Is that normal?
- Why exhibit that behaviour (if normal), as on surface its seems to suggest a momentary MAC auth and ‘Default NAC Profile’ assignment before moving back to 802.1x?
- If not normal, what do I do to fix it?
Many thanks,
Martin
