- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: 802.1x clients transition to MAC auth and back...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
802.1x clients transition to MAC auth and back again, every hour?
802.1x clients transition to MAC auth and back again, every hour?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-25-2020 03:47 PM
Hi There,
Hoping someone can help me explain the behaviour below and say either if it is normal or a means to correct it.
It seems that every hour a re-authentication of 802.1x is triggered, that process initially introduces a MAC auth that temporarily hits the default catch all rule that we have yet to flip into a deny rule.
After that it then re-authenticates correctly using EAP-TLS until the next hour?
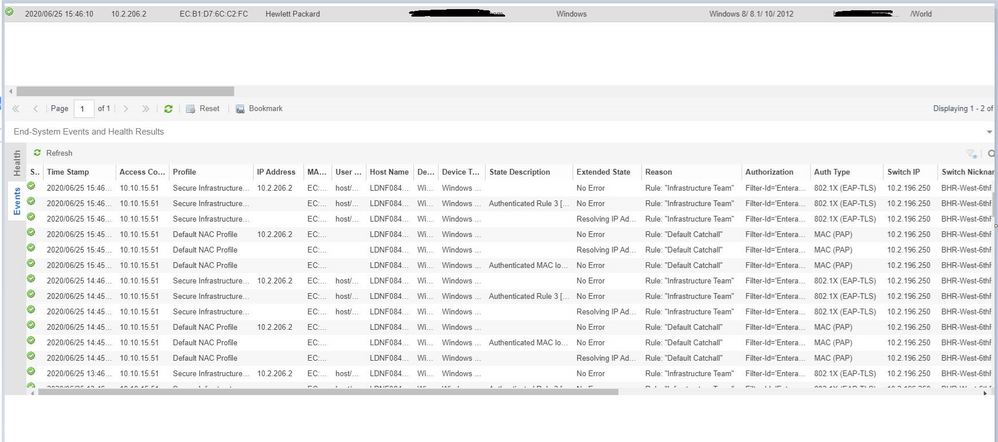
Many thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-30-2020 12:23 PM
Great, Thanks Z.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-30-2020 12:20 PM
Hi Martin.
yes, I agree with your statements/summarization.
cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-30-2020 11:54 AM
Thanks Z,
So I think I have translated this to being the fact that netlogin is showing both a 802.1x and MAC auth for the same device, with obviously 802.1x is taking precedence.
The re-auth for both auth types is set to 3600 seconds.
The end-system events is probably showing the audit logs of these going through re-authentication for each authentication type, 1 hour apart, there being a 19 minute difference between the two.
Whats probably happening is the time between a MAC re-auth and then a 802.1x re-auth (19 minutes) is showing up in the aduit as a MAC Auth, but the reality is the switch always remains authenticated using 802.1x.
Do you think that sums it up?
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-29-2020 10:09 PM
Hi Martin.
you can see the 802.1X takes the precedence = Session applied : true
OneView → Control → End-Systems: In the top table there should be the “actual state” = you see dot1x authentication, IP, ….
If you select the end-system then in the bottom you see end-system events and Health Results = there you see also not active sessions and “audit” of what happens = IP resolution, hostname detection, re-authentications…
