- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Cisco Trunk Interface with Extreme NAC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Trunk Interface with Extreme NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-12-2020 07:33 AM
Dear All
I’m trying to enable Extreme NAC for Cisco switches. It works fine for Clients on Access Ports. For Accesspoints (local breakout), I’m trying to get a trunk interface with management vlan untagged and data VLANs tagged.
For XOS Switches, I would create a Role with the needed VLAN Egress config
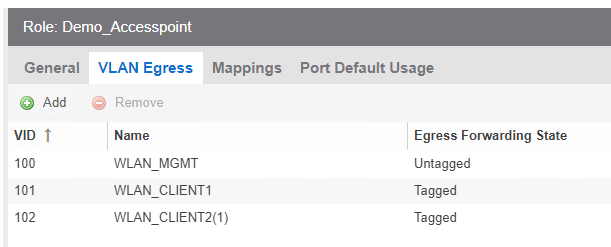
But I cant enforce this role configuration to Cisco switches
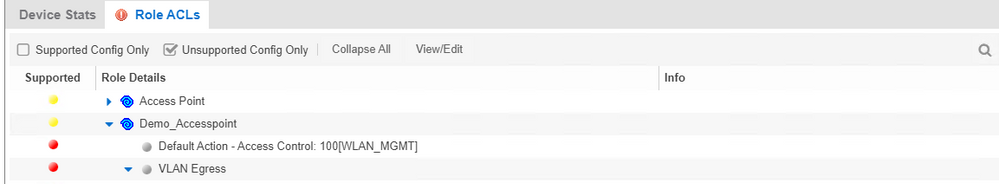
How can I achieve that for Cisco switches with Extreme NAC?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-15-2020 11:53 AM
Hi Miguel
Yes sure, I can share my cisco config. In the meantime, I tested NEAT as well and it seems to be easier than using macro.
Macro
conf t
no macro auto global control device
no macro auto global control trigger
macro auto global processing
macro auto execute AP_TRUNK {
if [[ $LINKUP == YES ]]
then conf t
default interface $INTERFACE
interface $INTERFACE
Description AP_TRUNK
macro description $TRIGGER
switchport trunk allowed vlan ##VLAN-LIST##
switchport trunk native vlan ##VLAN##
switchport mode trunk
spanning-tree portfast trunk
macro auto processing
exit
fi
if [[ $LINKUP == NO ]]
then conf t
default interface $INTERFACE
interface $INTERFACE
description NAC
no switchport trunk allowed vlan
no switchport trunk native vlan
switchport mode access
macro auto processing
authentication control-direction in
authentication event server dead action authorize
authentication event server dead action authorize voice
authentication event server alive action reinitialize
authentication host-mode multi-host
authentication order mab dot1x
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation restrict
mab
snmp trap mac-notification change added
snmp trap mac-notification change removed
dot1x pae authenticator
dot1x timeout tx-period 10
no macro description $TRIGGER
exit
fi
}
int range ##INTERFACE-RANGE##
macro auto processing
Radius Attribute: Cisco-AVPair=auto-smart-port=AP_TRUNK
NEAT
cisp enable
!
template AP_TRUNK
switchport trunk encapsulation dot1q
switchport trunk native vlan 100
switchport mode trunk
Radius Attribute: Cisco-AVPair=interface-template-name=AP_TRUNK
Comparison Smart Port vs. Macro:
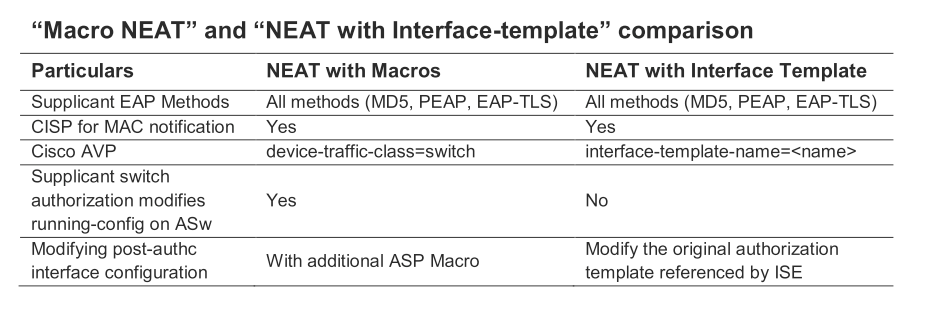
best regards
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-13-2020 01:24 PM
Hello Stefan,
with pleasure.
I am not sure if this is possilbe.
According this guide (https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_8021x/configuration/15-e/sec-usr-8021x-15-...)
“The VSA changes the authenticator switch port mode from access to trunk and enables 802.1X trunk encapsulation and the access VLAN (if any) would be converted to a native trunk VLAN. VSA does not change any of the port configurations on the supplicant.”
it sound there is no vlan change available. But it’s not 100% clear if an additional vsa can send the vlan IDs. Like you configured for vlan 999.
Do you still these lines in the debug from your switch?
Oct 13 08:11:15.165: RADIUS: Vendor, Cisco [26] 19
Oct 13 08:11:15.165: RADIUS: Cisco AVpair [1] 13 "vlan-id=999"
Oct 13 08:11:15.165: RADIUS: Vendor, Cisco [26] 18
This entry point to the vlan send by NAC.
Best regards
Stephan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-13-2020 12:46 PM
Hi Stephan
After changing to “Cisco-AVPair=”, the Ports gets configured as a trunk port. So next step will be to check if I can send native and allowed vlans via Radius attribute.
thanks a lot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-13-2020 08:10 AM
Hello Michael,
one additional point. You can try to change “cisco-avpair=” to “Cisco-AVPair=”.
I think there was at least in the past a dependence on upper and lower case letters.
Regards
Stephan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-13-2020 07:54 AM
Hello Michael,
sorry I saw some of my text is missing on my replay. The following was missing:
Only if you enable “Client Information Signaling Protocol (CISP)” on your switch you can change the port type via Radius according the Network Edge Authentication Topology (NEAT).
Do you have enabled CISP?
Regards
Stephan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-13-2020 06:38 AM
Hello Michael.
the Cisco Ethernet Interface Type (= Access or Trunk Port) can’t configured via Radius attributes.
This is independet of the Radius-Server or NAC-Vendor. Cisco does not offer the possibility to switch over via radius protocol.
This is because unlike other vendors, Cisco explicitly distinguishes the port type, while others simply distribute tagged and untagged VLANs. Which is again provided for in the radius protocol.
If you need an dynamic change between Trunk and Access Port and the standard configuration ist Access Port you can enable authentication, and trigger a script on XMC if a access point is is recognized. This script hast to change the Cisco port Config and do an reauth.
Regards
Stephan
