This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- RE: Generate Emailnotification "Port down" with Po...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Generate Emailnotification "Port down" with Portalias by Netsight
Generate Emailnotification "Port down" with Portalias by Netsight
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-17-2015 09:07 AM
Hi all,
our customer want to modify his email-alarming by netsight.
Today he get's an email information, if an port goes down - this works well.
Now he wants, that the portalias will be displayed in the emailnotification - the real configured alias in EOS ("set port alias ge.1.1 "TEST-Portalias").
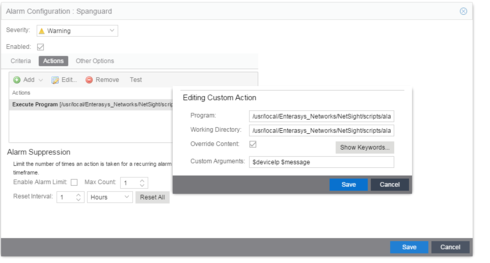
With "action override" in netsight, the parameter $alarmSubcomponent only display the port name (e.g. ge.1.1) but not the alias ("TEST-Portalias).
Did someone has an idea ?
regards,
Carsten
our customer want to modify his email-alarming by netsight.
Today he get's an email information, if an port goes down - this works well.
Now he wants, that the portalias will be displayed in the emailnotification - the real configured alias in EOS ("set port alias ge.1.1 "TEST-Portalias").
With "action override" in netsight, the parameter $alarmSubcomponent only display the port name (e.g. ge.1.1) but not the alias ("TEST-Portalias).
Did someone has an idea ?
regards,
Carsten
4 REPLIES 4
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-05-2016 08:27 AM
Hi Thomas,
i opend a case - the solution is scheduled for NetSight 7.0.
So i will wait until GA for 7.0 in April/Mai.
i opend a case - the solution is scheduled for NetSight 7.0.
So i will wait until GA for 7.0 in April/Mai.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-04-2016 03:54 PM
Use a script to do a bunch of legwork is an option.
Basically take the trap, and use alarm manager to pass deviceIP, and the trap message down to the script. The script would need access to the snmp creds of the device.
The trap message will have the bridge port ID. The script will need to parse the message for the bridge port
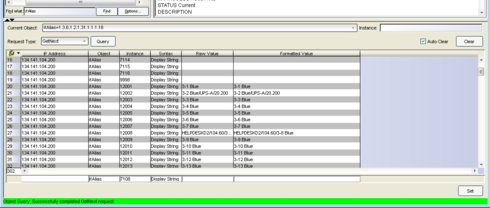
Take the bridge port number, query the ifalias mib: 1.3.6.1.2.1.31.1.1.1.18. That'll give you the port alias.
Use the script to mail out result.
Basically take the trap, and use alarm manager to pass deviceIP, and the trap message down to the script. The script would need access to the snmp creds of the device.
The trap message will have the bridge port ID. The script will need to parse the message for the bridge port
Take the bridge port number, query the ifalias mib: 1.3.6.1.2.1.31.1.1.1.18. That'll give you the port alias.
Use the script to mail out result.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-07-2016 01:04 PM
Hi Ryan,
the gtacnowledge-solution will NOT work.
It will only displayed the Portname ge.1.9 but not the configured Portalias.
Any other idea ?
regards,
Carsten
the gtacnowledge-solution will NOT work.
It will only displayed the Portname ge.1.9 but not the configured Portalias.
Any other idea ?
regards,
Carsten
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-30-2015 07:42 PM
Hello,
Check out the following article and let me know if it helps.
https://gtacknowledge.extremenetworks.com/articles/Solution/Traps-are-not-displaying-port-alias-info...
Thanks
-Ryan
Check out the following article and let me know if it helps.
https://gtacknowledge.extremenetworks.com/articles/Solution/Traps-are-not-displaying-port-alias-info...
Thanks
-Ryan