This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Trying to setup the most basic MAC based Access Co...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Trying to setup the most basic MAC based Access Control but need help
Trying to setup the most basic MAC based Access Control but need help
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-13-2018 09:09 PM
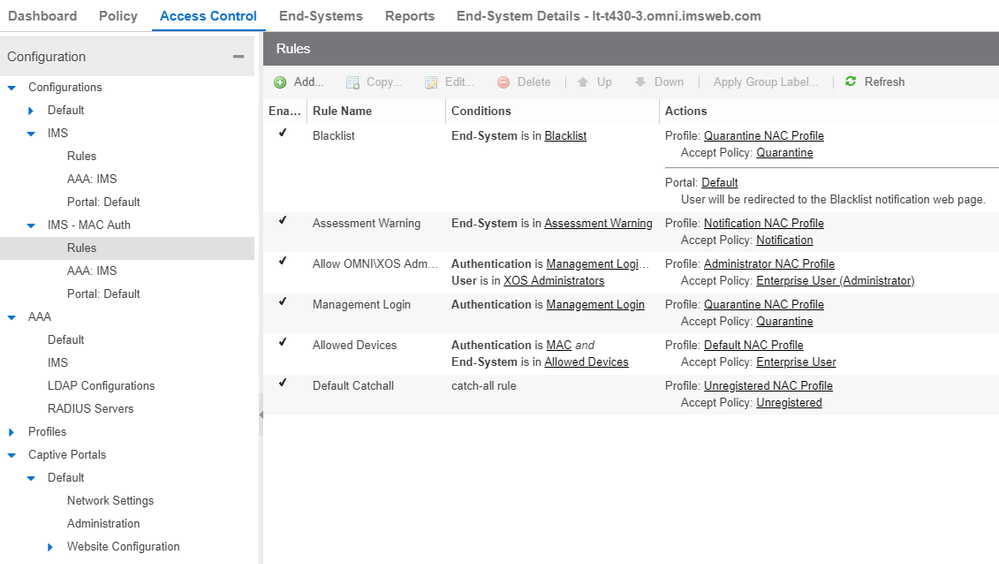
We know that XMC and NAC can do a whole lot, but initially all we want to do is this:
1) A system will be plugged into a port and will show up in the end-systems tab
2) An administrator will then add that to the "Allowed Devices" group which we have created (for simplicity, this group uses the "Default NAC Profile" which uses the "Enterprise User" Accept Policy)
3) All other systems that have not been added to the "Allowed Devices" group are blocked from accessing the network.
I have an isolated non-production switch that I want to test this on, but I have a question about the config and the rules.
1) We have one Configuration (IMS) that is currently in use on all switches. I have made a secondary Configuration (IMS - MAC Auth) which I wanted to use for MAC auth testing, but I can't figure out how to apply that to just the one switch I want to test on (it has been a while since we first deployed XMC/NAC and I don't know if I am just forgetting where the option is or if a whole new Policy Domain is needed to make this happen)?
2) If the other configuration can be assigned to just a switch for testing, will the attached rules accomplish what we want?
I'm new to the NAC side of things and know that it can cause issues when configured incorrectly, so all the help (and clarification to ideas that I am not understanding correctly) you can provide is welcome.
1) A system will be plugged into a port and will show up in the end-systems tab
2) An administrator will then add that to the "Allowed Devices" group which we have created (for simplicity, this group uses the "Default NAC Profile" which uses the "Enterprise User" Accept Policy)
3) All other systems that have not been added to the "Allowed Devices" group are blocked from accessing the network.
I have an isolated non-production switch that I want to test this on, but I have a question about the config and the rules.
1) We have one Configuration (IMS) that is currently in use on all switches. I have made a secondary Configuration (IMS - MAC Auth) which I wanted to use for MAC auth testing, but I can't figure out how to apply that to just the one switch I want to test on (it has been a while since we first deployed XMC/NAC and I don't know if I am just forgetting where the option is or if a whole new Policy Domain is needed to make this happen)?
2) If the other configuration can be assigned to just a switch for testing, will the attached rules accomplish what we want?
- Quarantine anything in the Blacklist group
- Send a notification for anything in the Assessment Warning group
- Allow anyone if the omni\XOS Administrators group to login to the switches (this currently works)
- Quarantine any system from which a user attempts to login to a switch but they are not in the omni\XOS administrators group
- Allow any system that is in the "Allowed Devices" group onto the network
- Block all other devices
I'm new to the NAC side of things and know that it can cause issues when configured incorrectly, so all the help (and clarification to ideas that I am not understanding correctly) you can provide is welcome.
15 REPLIES 15
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-14-2018 12:05 AM
makes sense. so the configuration that is the least restrictive is used when there is more than one configured i am assuming?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-13-2018 11:55 PM
The policy domain is only for policy (manager) = which roles/services/VLAN/portauth config you will upload to the switch.
The rules (e.g. from the screenshot you've provided) are for the whole NAC.
For testing I'd create a new one - you'd copy all settings from the old one > move the test switch to the new domain and then play around - I think that is better so you don't mess up the running domain.
The rules (e.g. from the screenshot you've provided) are for the whole NAC.
For testing I'd create a new one - you'd copy all settings from the old one > move the test switch to the new domain and then play around - I think that is better so you don't mess up the running domain.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-13-2018 11:40 PM
so you can only have one configuration 'live' at a time per domain? If i want to teat a new configuration, I have to assign it to a new domain, and assign that new domain to the single switch for testing?
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-13-2018 11:21 PM
My thoughts....
I don't think that the rule "Management Login" will ever hit.
The rule "Allow OMNI.." is hit for mgmt access and if the user put in a wrong user/pw you just get no login to the switch via e.g. telnet/ssh.
Even if it would hit what should happen - I'd access via telnet/ssh from 10 hops away so you are not able to put me in quarantine.... I'd even telnet/ssh from another switch > will you quarantine the whole switch !?
"default catchall" - how about you set that also to profile Default NAC Profile.
You'd configure anything without blocking anyone > add devices to the correct groups so they end up in Allowed Devices.
After you've put whatever you think should go into Allowed you'd take a closer look for the rest of devices that get catchall > make sure that this devices really should be in catchall = "bad" clients and then you'd turn catchall to unregistered profile and block them > could reduce the calls that you get from angry clients that can't access the network 😉
To add a new domain go to the Policy tab > open/manage domain > create domain.
-Ron
I don't think that the rule "Management Login" will ever hit.
The rule "Allow OMNI.." is hit for mgmt access and if the user put in a wrong user/pw you just get no login to the switch via e.g. telnet/ssh.
Even if it would hit what should happen - I'd access via telnet/ssh from 10 hops away so you are not able to put me in quarantine.... I'd even telnet/ssh from another switch > will you quarantine the whole switch !?
"default catchall" - how about you set that also to profile Default NAC Profile.
You'd configure anything without blocking anyone > add devices to the correct groups so they end up in Allowed Devices.
After you've put whatever you think should go into Allowed you'd take a closer look for the rest of devices that get catchall > make sure that this devices really should be in catchall = "bad" clients and then you'd turn catchall to unregistered profile and block them > could reduce the calls that you get from angry clients that can't access the network 😉
To add a new domain go to the Policy tab > open/manage domain > create domain.
-Ron
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-13-2018 10:47 PM
That would help, wouldn't it. x460-G2 switches