- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeControl
- Extreme Control Machine + User authentication fail...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Extreme Control Machine + User authentication fails
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-05-2021 01:21 PM
Hi,
This Topic is a a follow up to
Although, I hopefully configured everything as advised and discussed in above thread,
Machine + User authentication fails. (Machine auth ONLY works fine, now!)
Below is a screenshot of the EvaluationTool result:
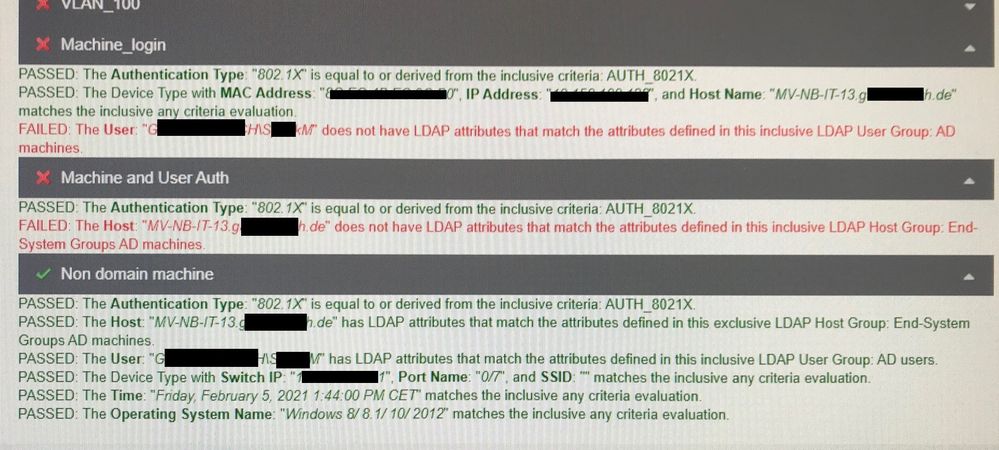
I don´t see the mistake….
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-26-2021 10:35 AM
Dear all,
today customer tested the solution/correction and it worked.
Below my solution/explanation:
In an earlier mentioned documentation (https://extremeportal.force.com/ExtrArticleDetail?an=000080814) I primarily followed it was advised to use “cn” as Host Search Attibute (within the LDAP-configuration of “Domain users”
At least in my environment, this did not work (as shown in above screenshots). The solution was to use “dNSHostName” as Host Search Attibute (which is the default).
Changing this, the configuration worked. Machine AND User-Authentication are passed successfull.
Unfortunately, this solution is already described in https://extremeportal.force.com/ExtrArticleDetail?an=000082479 which I found during my troubleshooting.
In addition to this modification of the solution, I changed the advised order of the Rules.
Instead of
- Authenticate and authorise a machine
- Authenticate and authorise a machine as a valid domain computer with a valid domain user logged in
- Deny a valid user who is on a non-domain (BYOD) computer
In my environment, Rule “2” never will be verified, after a Machine was successfully authenticated.
So, no user-authentication will ever happen.
For that reason, I switched the order of rule 1 and 2 and afterwards, all variations could be verified and authenticated.
Thanks all for your assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-26-2021 10:35 AM
Dear all,
today customer tested the solution/correction and it worked.
Below my solution/explanation:
In an earlier mentioned documentation (https://extremeportal.force.com/ExtrArticleDetail?an=000080814) I primarily followed it was advised to use “cn” as Host Search Attibute (within the LDAP-configuration of “Domain users”
At least in my environment, this did not work (as shown in above screenshots). The solution was to use “dNSHostName” as Host Search Attibute (which is the default).
Changing this, the configuration worked. Machine AND User-Authentication are passed successfull.
Unfortunately, this solution is already described in https://extremeportal.force.com/ExtrArticleDetail?an=000082479 which I found during my troubleshooting.
In addition to this modification of the solution, I changed the advised order of the Rules.
Instead of
- Authenticate and authorise a machine
- Authenticate and authorise a machine as a valid domain computer with a valid domain user logged in
- Deny a valid user who is on a non-domain (BYOD) computer
In my environment, Rule “2” never will be verified, after a Machine was successfully authenticated.
So, no user-authentication will ever happen.
For that reason, I switched the order of rule 1 and 2 and afterwards, all variations could be verified and authenticated.
Thanks all for your assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-18-2021 12:11 PM
Dear all,
I don´t know why, however I missed the last updates from Tomasz + Miguel.
Sorry, that was not intended.
Luckily it seems, that I could solve the issue by myself in the meantime.
At least, the Eval-Tool now shows a match to the according rule.
As i´m pretty unsure in this topic, I would like to wait for customer to test and confirm the solution.
Afterwards, I´ll update this topic.
Thanks @ALL for your help so far.
Stefan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-13-2021 10:46 AM
SDR,
As far as I remeber there were some issue for this config on double authentication (user+computer) using an LDAP validation for the computer. A specific agent could be necessary (Cisco does that) with windows.
This is the reason why an alternative with the workflow and script mentioned in my previous posts was done.
As a reminder this way of working is using MAC check instead of LDAP check to validate the computer during a user auth:
"Add MAC to Domain Computers" is executed when the computer authenticates. The MAC address is added to End-System and the timestamp is created (updated). Consequent User authentication can be combined with the condition of the End-System group. "Clear old End-Systems in the group" checks if the timestamp is older than X hours and old End-Systems are deleted from the group.
Maybe
Mig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-12-2021 04:40 PM
Hi,
Just a quick question, sorry if I misunderstood anything above. Your End-System Group checks if the device’s objectCategory is cn=computer(...). Is that what you need to check? What is the MV-NB-IT-13 objectCategory?
Quite often group membership in LDAP is checked with attribute like memberOf. dNSHostName is something you define in LDAP configurations for host lookup so when NAC receives auth request with a unique hostname, it can search in LDAP for a relevant device’s details (to match authenticating hostname and its LDAP reference).
Hope that helps,
Tomasz
