- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeControl
- Extreme Control Machine + User authentication fail...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Extreme Control Machine + User authentication fails
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-05-2021 01:21 PM
Hi,
This Topic is a a follow up to
Although, I hopefully configured everything as advised and discussed in above thread,
Machine + User authentication fails. (Machine auth ONLY works fine, now!)
Below is a screenshot of the EvaluationTool result:
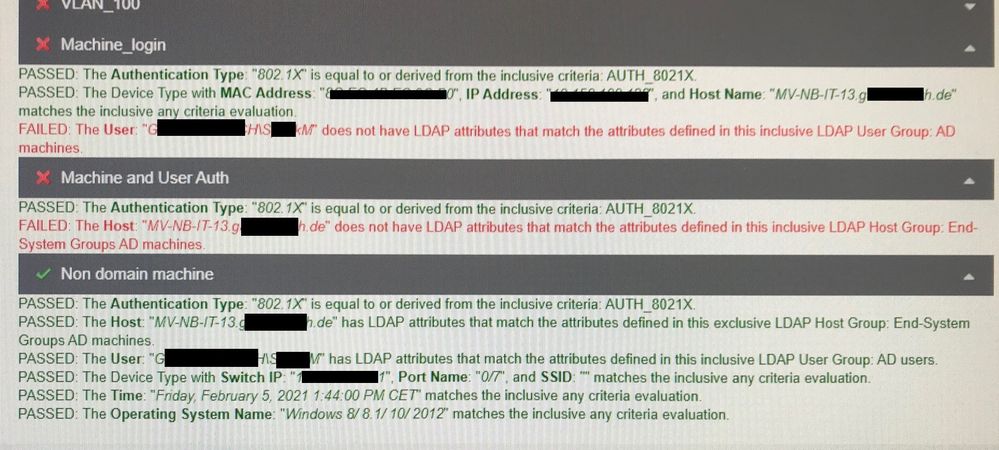
I don´t see the mistake….
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-26-2021 10:35 AM
Dear all,
today customer tested the solution/correction and it worked.
Below my solution/explanation:
In an earlier mentioned documentation (https://extremeportal.force.com/ExtrArticleDetail?an=000080814) I primarily followed it was advised to use “cn” as Host Search Attibute (within the LDAP-configuration of “Domain users”
At least in my environment, this did not work (as shown in above screenshots). The solution was to use “dNSHostName” as Host Search Attibute (which is the default).
Changing this, the configuration worked. Machine AND User-Authentication are passed successfull.
Unfortunately, this solution is already described in https://extremeportal.force.com/ExtrArticleDetail?an=000082479 which I found during my troubleshooting.
In addition to this modification of the solution, I changed the advised order of the Rules.
Instead of
- Authenticate and authorise a machine
- Authenticate and authorise a machine as a valid domain computer with a valid domain user logged in
- Deny a valid user who is on a non-domain (BYOD) computer
In my environment, Rule “2” never will be verified, after a Machine was successfully authenticated.
So, no user-authentication will ever happen.
For that reason, I switched the order of rule 1 and 2 and afterwards, all variations could be verified and authenticated.
Thanks all for your assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-12-2021 07:44 AM
Good morning all,
I´m quite desperate. I now have remote access and verified everything + also checked with the Eval-Tool + LDAP-Test-Feature.
Without success.
As shown in an earlier Screenshot, the Eval tool claims, that the Host “MV-xxx.de” does not have LDAP-attributes defined in the LDAP Host Group “End System Groups AD machines”.
Verifying this with LDAP-Test : see below:
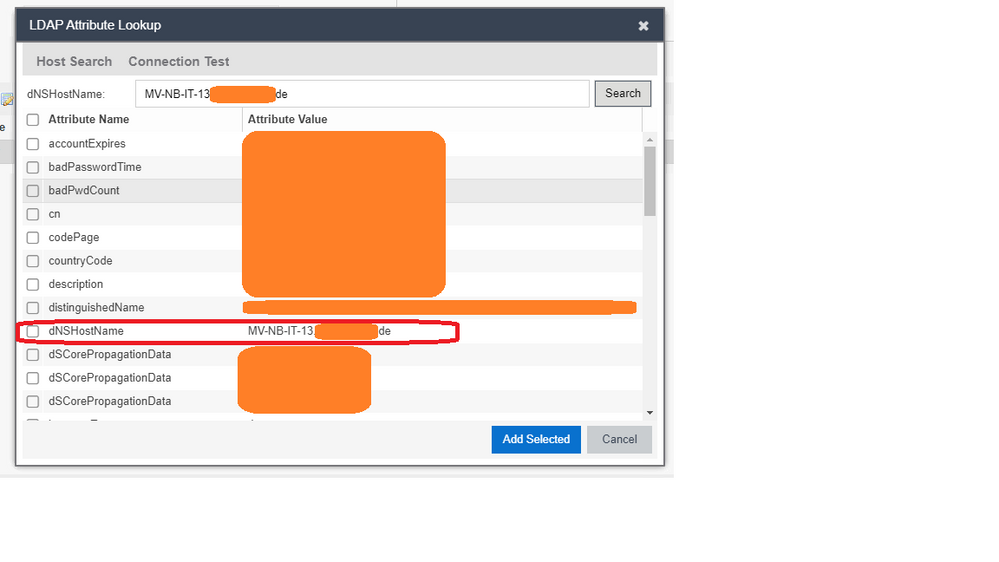
So, there IS such an entry.
What I am confused about: This entry is found as “dNSHostName”.
According to ealier mentioned guide, “objectcategory” is defined as attribute for the group.
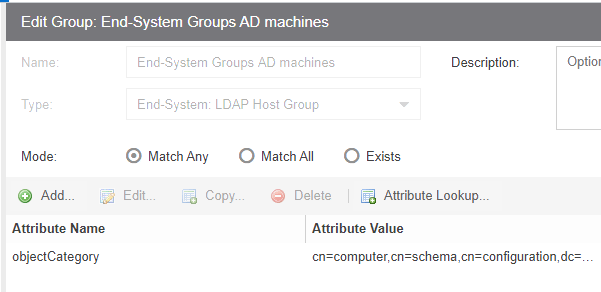
However, changing this to dnsNostName does not work either.
I checke configuration vs. guide several times…..don´t find the mistake.
Hope you can point out the issue….
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-09-2021 04:00 PM
Stefan,
Are you meeting all the requirements for the LDAP groups?
See documentation:
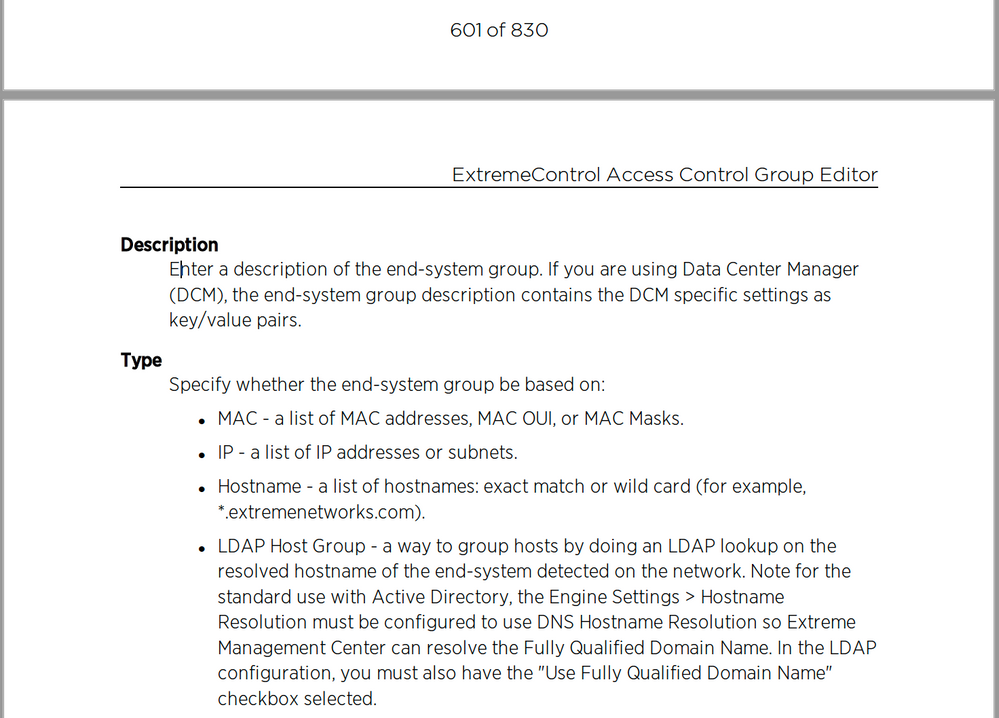
Mig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-09-2021 03:49 PM
Hello Stefan,
as I wrote above. If you have two rules with two different checks (is not and is), this is the point you have to investigate first.
In the LDAP test tool use the user search for rules matching an user and the host search for rules matching the host.
You can check which LDAP rule is used via the Eval tool (second tab = 2. Authentication evaluation).
As result you will receive the groups you user/device is in.
If you play arround with these settings you will have a good understanding what happen during the ldap checks in NAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-09-2021 02:05 PM
Hello Stephan, Mig,
sorry for delay due to private reasons.
- Authenticate Windows CLIENT based on machine being in the AD.
- Authenticate Windows USER on Windows CLIENT based on machine AND User being in the AD.
- Reject Non-domain machine.
According to the documents and you assistance here we managed, that
TOP 1) “Authenticate Windows CLIENT based on machine being in the AD.” works.
TOP 2) does not yet work - as documented by my screenshots.
With regards to
As we have no remote access to the environment at the moment, I cannot test/verify again.
However, pls clearify what/how to test.
I have to verify once again
- if the Host (written exactly like thrown out in the EVAL tool) is found in LDAP-Test (which section? User search? Host search?
- if the User (written exactly like thrown out in the EVAL tool) is found in LDAP-Test (which section? User search? Host search?
As soon as I have the result, i´ll post a screenshot.
Thanks + sorry for confusion, again
Stefan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-05-2021 07:06 PM
That wasn’t my understanding…
SDR, It would be nice to clarify the exact use case and method you are trying to achieve.
Mig
