- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- Re: Difference betwwen vpls exclude and include
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Difference betwwen vpls exclude and include
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-11-2020 03:33 AM
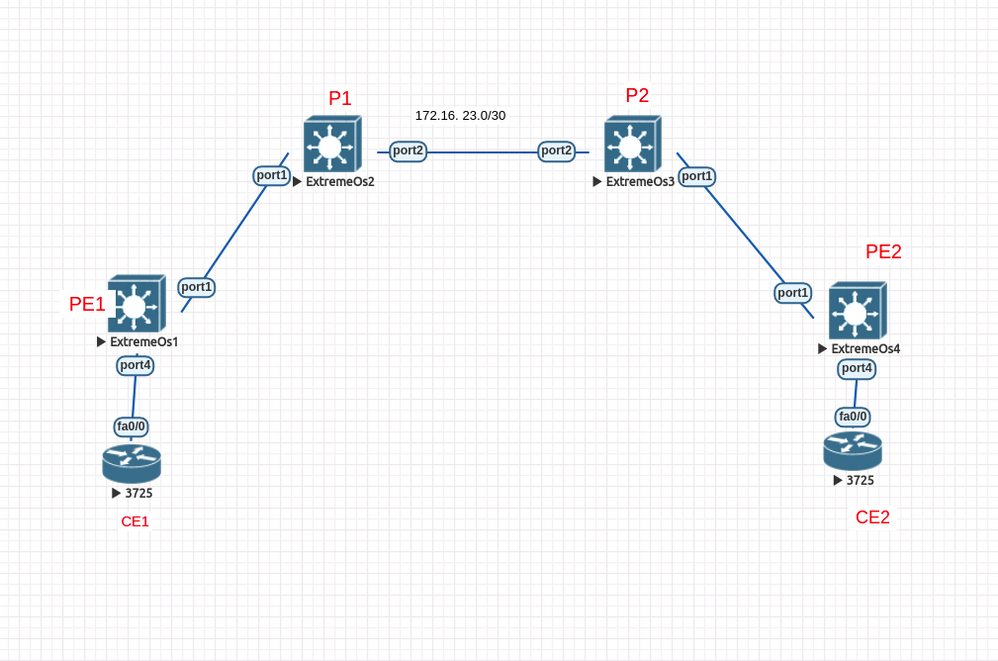
I have test VPLS service as below design
CE1------>>PE1------>>P1-------->>P2-------->>PE2--------->>CE2
PE1 and PE2 are spoke router
P1 and P2 are core router
I have configured vpls spoke to core between PE1 and P1 , PE2 and P2
P1 and P2 has vpls core full mesh
P1 and P2 vpls profile have confiugred dot1q exclude and PE2 and PE1 configured dot1q include
I got ping access between CE1 and CE2
Here ,I have a question
PE1 and PE2 send to P1 and P2 packet with S VMAN tag
P1 and P2 are configured dot1q exclude.
when they recevie packet with S VMAN tag ,how to handle its.
And I have captured packet in wireshark ,only see MPLS VC label and transit label
Can’t see dot1q tag detial in packet and it have data
I need to data packet details .
Please see my design and configuration
PE1 Config
Loopback ip of PE1 is 22.22.22.22
Lab-PE1.1 # show vpls
L2VPN Name VPN ID Flags Services Name Peer IP State Flags
--------------- ------ ------- --------------- --------------- ----- -------
Test-Vpls 10 EAI-VL- test 1.1.1.1 Up CAs-V-L
VPN Flags: (E) Admin Enabled, (A) Oper Enabled, (I) Include Tag,
(X) Exclude Tag, (T) Ethertype Configured,
(V) VCCV HC Enabled, (W) VPN Type VPWS, (L) VPN Type VPLS,
(M) CFM MIP Configured
Peer Flags: (C) Core Peer, (S) Spoke Peer, (A) Active Core,
(p) Configured Primary Core, (s) Configured Secondary Core,
(N) Named LSP Configured, (V) VCCV HC Capabilities Negotiated,
(F) VCCV HC Failed, (L) LDP Signaled, (T) Static (Not Signaled)
L2VPN Name: Test-Vpls
VPN ID : 10 Admin State : Enabled
Source Address : 22.22.22.22 Oper State : Enabled
VCCV Status : Enabled MTU : 1700
VCCV Interval Time : 5 sec. Ethertype : 0x88a8
VCCV Fault Multiplier : 4 .1q tag : include
L2VPN Type : VPLS Redundancy : None
Service Interface : test
Created By : CLI
--------------------------------------------------------------------------
P1 config
Loopback ip of P1 is 1.1.1.1
P1.1 # show vpls
L2VPN Name VPN ID Flags Services Name Peer IP State Flags
--------------- ------ ------- --------------- --------------- ----- -------
Test-Vpls 10 EAX-VL- test 2.2.2.2 Up C---V-L
22.22.22.22 Up S---V-L
VPN Flags: (E) Admin Enabled, (A) Oper Enabled, (I) Include Tag,
(X) Exclude Tag, (T) Ethertype Configured,
(V) VCCV HC Enabled, (W) VPN Type VPWS, (L) VPN Type VPLS,
(M) CFM MIP Configured
Peer Flags: (C) Core Peer, (S) Spoke Peer, (A) Active Core,
(p) Configured Primary Core, (s) Configured Secondary Core,
(N) Named LSP Configured, (V) VCCV HC Capabilities Negotiated,
(F) VCCV HC Failed, (L) LDP Signaled, (T) Static (Not Signaled)
P1.3 # show vpls Test-Vpls detail
L2VPN Name: Test-Vpls
VPN ID : 10 Admin State : Enabled
Source Address : 1.1.1.1 Oper State : Enabled
VCCV Status : Enabled MTU : 1700
VCCV Interval Time : 5 sec. Ethertype : 0x88a8
VCCV Fault Multiplier : 4 .1q tag : exclude
L2VPN Type : VPLS Redundancy : None
Service Interface : test
Created By : CLI
-----------------------------------------------
P2 config
Loopback ip of P2 is 2.2.2.2
Lab-P2.1 # show vpls
L2VPN Name VPN ID Flags Services Name Peer IP State Flags
--------------- ------ ------- --------------- --------------- ----- -------
Test-Vpls 10 EAX-VL- test 1.1.1.1 Up C---V-L
33.33.33.33 Up S---V-L
VPN Flags: (E) Admin Enabled, (A) Oper Enabled, (I) Include Tag,
(X) Exclude Tag, (T) Ethertype Configured,
(V) VCCV HC Enabled, (W) VPN Type VPWS, (L) VPN Type VPLS,
(M) CFM MIP Configured
Peer Flags: (C) Core Peer, (S) Spoke Peer, (A) Active Core,
(p) Configured Primary Core, (s) Configured Secondary Core,
(N) Named LSP Configured, (V) VCCV HC Capabilities Negotiated,
(F) VCCV HC Failed, (L) LDP Signaled, (T) Static (Not Signaled)
Lab-P2.3 # show vpls Test-Vpls detail
L2VPN Name: Test-Vpls
VPN ID : 10 Admin State : Enabled
Source Address : 2.2.2.2 Oper State : Enabled
VCCV Status : Enabled MTU : 1700
VCCV Interval Time : 5 sec. Ethertype : 0x88a8
VCCV Fault Multiplier : 4 .1q tag : exclude
L2VPN Type : VPLS Redundancy : None
Service Interface : test
Created By : CLI
--------------------------------------------------
PE2 config
Loopback ip of PE2 is 33.33.33.33
Lab-PE2.1 # show vpls Test-Vpls
L2VPN Name VPN ID Flags Services Name Peer IP State Flags
--------------- ------ ------- --------------- --------------- ----- -------
Test-Vpls 10 EAI-VL- test 2.2.2.2 Up CAp-V-L
VPN Flags: (E) Admin Enabled, (A) Oper Enabled, (I) Include Tag,
(X) Exclude Tag, (T) Ethertype Configured,
(V) VCCV HC Enabled, (W) VPN Type VPWS, (L) VPN Type VPLS,
(M) CFM MIP Configured
Peer Flags: (C) Core Peer, (S) Spoke Peer, (A) Active Core,
(p) Configured Primary Core, (s) Configured Secondary Core,
(N) Named LSP Configured, (V) VCCV HC Capabilities Negotiated,
(F) VCCV HC Failed, (L) LDP Signaled, (T) Static (Not Signaled)
Lab-PE2.2 # show vpls Test-Vpls detail
L2VPN Name: Test-Vpls
VPN ID : 10 Admin State : Enabled
Source Address : 33.33.33.33 Oper State : Enabled
VCCV Status : Enabled MTU : 1700
VCCV Interval Time : 5 sec. Ethertype : 0x88a8
VCCV Fault Multiplier : 4 .1q tag : include
L2VPN Type : VPLS Redundancy : None
Service Interface : test
Created By : CLI
Please see wireshark packets details
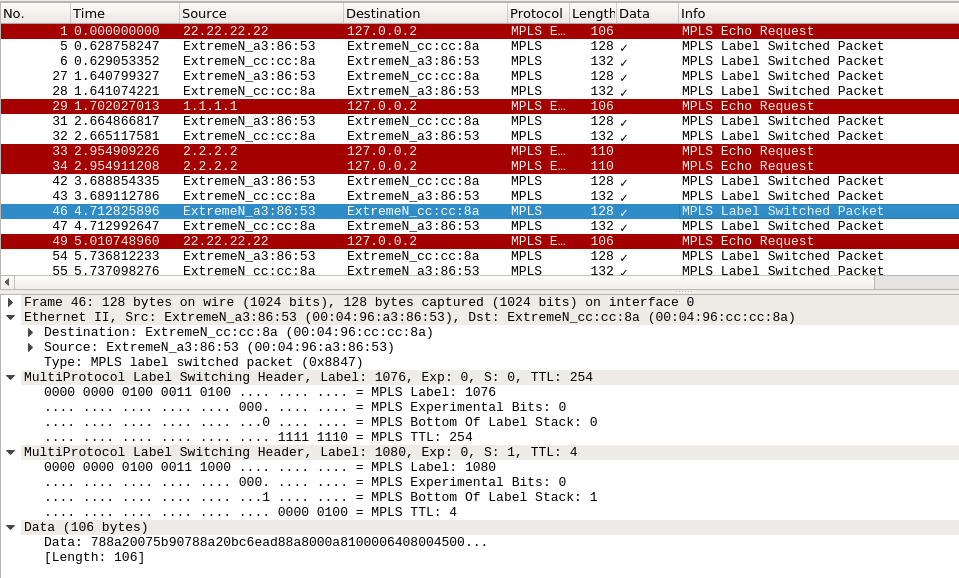
I need to know data packet and what have it under as like below image that is you says
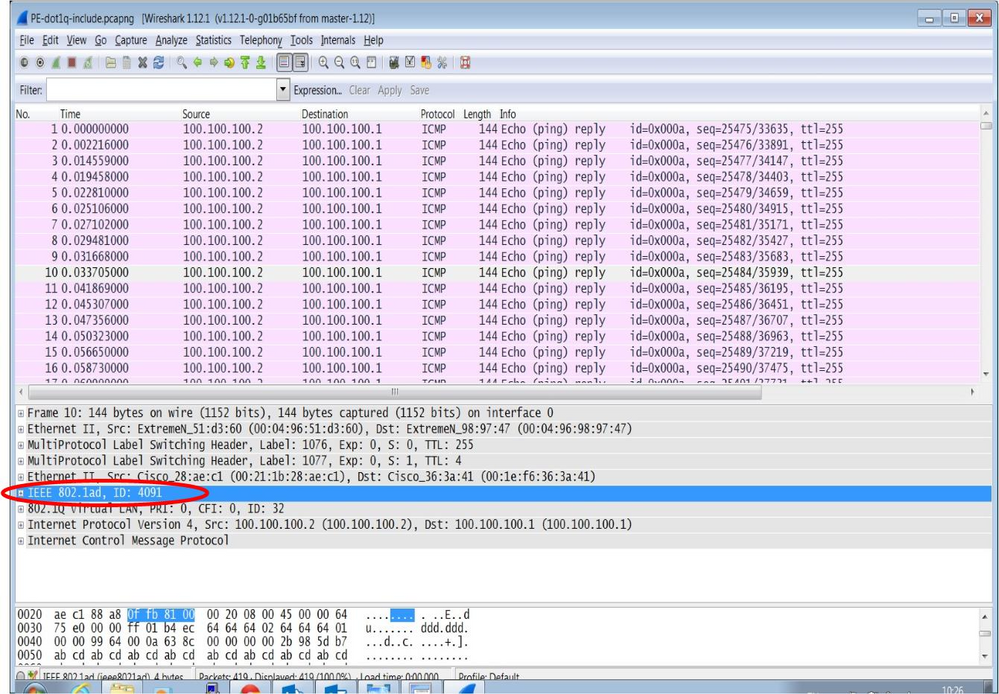
it got from below link
https://extremeportal.force.com/ExtrArticleDetail?an=000077359
Please advice me and thanks
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-17-2020 01:35 PM
Hello Zombie,
Each VPLS is VFI (virtual forwarding instance) with attached VP (virtual port), this VPs might be port/vlan or PWs. In your case packets should be forwarded between 2 PWs. Also in your design P-routers acts as PEs, as they strip off MPLS header and add new one (not only top label). So every PE in your case does encapsulation/decapsulation process. In your test ICMP packets is forwarded within VFI between 2 PWs so packets received from PW1 decapsulate and then encapsulate into PW2, and right now we could not confirm that this dec/enc process is the same as for packet which is received from local attached port/vlan. Probably some hardware registers should not be reprogrammed to keep latency low.
To get more info on this additional tests are required, so if you are interested please raise service case.
Best Regards,
Nikolay
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-12-2020 08:38 AM
Hello Zombie,
The issue itself is not with the packets or EXOS config but with the “wireshark” settings as it could not filter out input correctly and print it like raw data. I’ve taken data from your picture “88 A2 00 77 5B 90 78 8A 20 BC 6E AD 88 A8 00 0A 81 00 00 64 08 00 45 00 00” and decoded it with https://hpd.gasmi.net and got correct data you are looking for
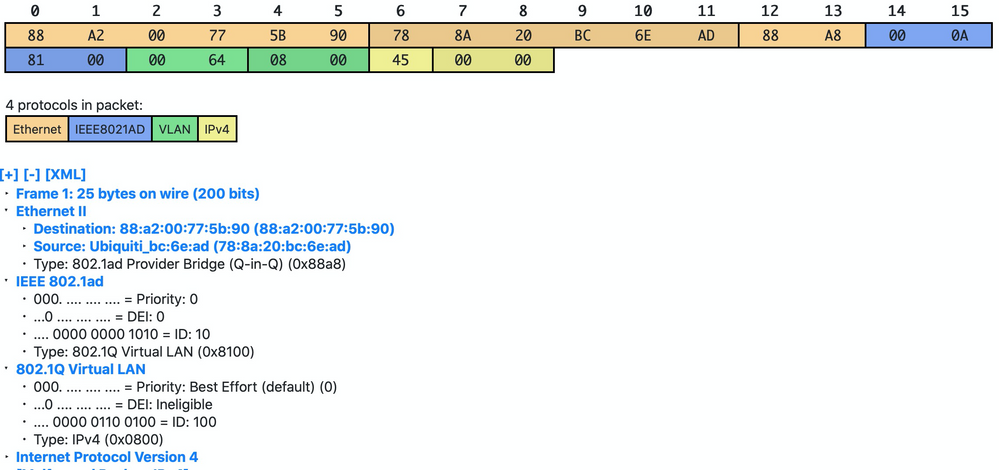
So if you need to know data packet you have to tune wireshark settings or use “editcap” tool, which may strip first n bytes from the packets (mpls part), like in example below:
editcap -C 52 mpls.pcap ## strip first 52 bytes
Best Regards,
Nikolay
