This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (EXOS/Switch Engine)
- RE: EXOS configuration for VLAN to connect to Inte...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
EXOS configuration for VLAN to connect to Internet
EXOS configuration for VLAN to connect to Internet
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-03-2017 10:38 PM
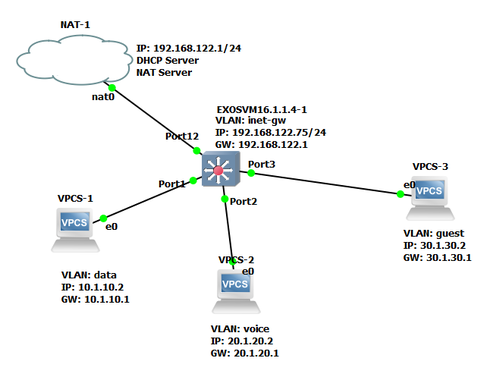
Newbie to networking and Extreme Networks switch and trying to set up a simple config at home. I picked up a Summit 450e defaulted to factory config with a 15.6b image. I have created 4 VLANs - data,voice, guest and inet-gw. Port 1 is data, Port 2 is voice, Port 3 is guest, Port 12 is inet-gw. PC attached to each of ports 1, 2 and 3 and a verizon router attached to port 12. For purposes of simulating using GNS-3 I used the NAT-1 appliance instead of the actual Verizon router. I am able to ping each PC from each of the other PCs connected to the switch. I am able to ping www.google.com and other publicly accessible internet sites from the inet-gw VLAN on the switch using the console (hence showing that the NAT-1 connection to the switch works). The problem is that i cannot reach the internet from any of the PCs connected to the switch (i.e. from the data, voice, or guest VLANs). I followed Drew C's post that showed a very similar set-up but he did not have any actual configuration commands so obviously I am missing something in my config. Have been messing with it for the last two days but no luck so throwing myself at your mercy now...config schematic below...
* Summit-PC.11 # show vlan ----------------------------------------------------------------------------------------------- Name VID Protocol Addr Flags Proto Ports Virtual Active router /Total ----------------------------------------------------------------------------------------------- data 10 10.1.10.1 /24 -f--------------------------- ANY 1 /1 VR-Default Default 1 ------------------------------------------------- ANY 0 /0 VR-Default guest 30 30.1.30.1 /24 -f--------------------------- ANY 1 /1 VR-Default inet-gw 100 192.168.122.175/24 -f--------------------------- ANY 1 /1 VR-Default Mgmt 4095 ------------------------------------------------- ANY 1 /1 VR-Mgmt voice 20 20.1.20.1 /24 -f--------------------------- ANY 1 /1 VR-Default -----------------------------------------------------------------------------------------------Ori Destination Gateway Mtr Flags VLAN Duration
#bo Default Route 192.168.122.1 1 UG-D---um--f- inet-gw 0d:0h:34m:7s
#d 10.1.10.0/24 10.1.10.1 1 U------um--f- data 0d:0h:34m:18s
#d 20.1.20.0/24 20.1.20.1 1 U------um--f- voice 0d:0h:34m:18s
#d 30.1.30.0/24 30.1.30.1 1 U------um--f- guest 0d:0h:34m:18s
#d 192.168.122.0/24 192.168.122.175 1 U------um--f- inet-gw 0d:0h:34m:8s
* Summit-PC.17 # sh dhcp-client state
Client VLAN Protocol Server Current State
--------------- -------- --------------- ---------------------------------------
data None 0.0.0.0
Default None 0.0.0.0
guest None 0.0.0.0
inet-gw DHCP 192.168.122.1 DHCP state; Bound
Mgmt None 0.0.0.0
voice None 0.0.0.0
A total of 6 vlan(s) where displayed.
* Summit-PC.11 # show vlan ----------------------------------------------------------------------------------------------- Name VID Protocol Addr Flags Proto Ports Virtual Active router /Total ----------------------------------------------------------------------------------------------- data 10 10.1.10.1 /24 -f--------------------------- ANY 1 /1 VR-Default Default 1 ------------------------------------------------- ANY 0 /0 VR-Default guest 30 30.1.30.1 /24 -f--------------------------- ANY 1 /1 VR-Default inet-gw 100 192.168.122.175/24 -f--------------------------- ANY 1 /1 VR-Default Mgmt 4095 ------------------------------------------------- ANY 1 /1 VR-Mgmt voice 20 20.1.20.1 /24 -f--------------------------- ANY 1 /1 VR-Default -----------------------------------------------------------------------------------------------Ori Destination Gateway Mtr Flags VLAN Duration
#bo Default Route 192.168.122.1 1 UG-D---um--f- inet-gw 0d:0h:34m:7s
#d 10.1.10.0/24 10.1.10.1 1 U------um--f- data 0d:0h:34m:18s
#d 20.1.20.0/24 20.1.20.1 1 U------um--f- voice 0d:0h:34m:18s
#d 30.1.30.0/24 30.1.30.1 1 U------um--f- guest 0d:0h:34m:18s
#d 192.168.122.0/24 192.168.122.175 1 U------um--f- inet-gw 0d:0h:34m:8s
* Summit-PC.17 # sh dhcp-client state
Client VLAN Protocol Server Current State
--------------- -------- --------------- ---------------------------------------
data None 0.0.0.0
Default None 0.0.0.0
guest None 0.0.0.0
inet-gw DHCP 192.168.122.1 DHCP state; Bound
Mgmt None 0.0.0.0
voice None 0.0.0.0
A total of 6 vlan(s) where displayed.
9 REPLIES 9
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-04-2017 12:25 PM
I agree with Erik. Lets use a device we have more control over.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-04-2017 09:31 AM
You could try one of the free software routers available for GNS3 instead of the NAT-1 device. For example one of the LEDE, OpenWRT, BSDRP or BIRD router appliances. There you can configure static routes towards the client networks.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-04-2017 01:48 AM
Patrick and others,
Thanks for the reply. IP forwarding is enabled on the Vlans. I can ping 192.168.122.175 on port 12 from the other PCs but not 192.168.122.1 - it cannot see that for some reason. The NAT1 device in GNS-3 does not allow for any configuration. Attached below is the config and the message I get back when I ping from VPCS1 (PC 1)...
VPCS> sh ip
NAME : VPCS[1]
IP/MASK : 10.1.10.2/24
GATEWAY : 10.1.10.1
DNS :
MAC : 00:50:79:66:68:02
LPORT : 10012
RHOST:PORT : 127.0.0.1:10013
MTU: : 1500
VPCS> ping 192.168.122.175
84 bytes from 192.168.122.175 icmp_seq=1 ttl=64 time=3.267 ms
84 bytes from 192.168.122.175 icmp_seq=2 ttl=64 time=2.130 ms
84 bytes from 192.168.122.175 icmp_seq=3 ttl=64 time=5.607 ms
84 bytes from 192.168.122.175 icmp_seq=4 ttl=64 time=1.596 ms
84 bytes from 192.168.122.175 icmp_seq=5 ttl=64 time=1.368 ms
VPCS> ping 192.168.122.1
192.168.122.1 icmp_seq=1 timeout
192.168.122.1 icmp_seq=2 timeout
192.168.122.1 icmp_seq=3 timeout
192.168.122.1 icmp_seq=4 timeout
192.168.122.1 icmp_seq=5 timeout
Config File:
configure vlan default delete ports all
configure vr VR-Default delete ports 1-12
configure vr VR-Default add ports 1-12
configure vlan default delete ports 1-12
create vlan "data"
configure vlan data tag 10
create vlan "guest"
configure vlan guest tag 30
create vlan "inet-gw"
configure vlan inet-gw tag 100
create vlan "voice"
configure vlan voice tag 20
configure vlan data add ports 1 untagged
configure vlan guest add ports 3 untagged
configure vlan inet-gw add ports 12 untagged
configure vlan data ipaddress 10.1.10.1 255.255.255.0
enable ipforwarding vlan data
configure vlan voice ipaddress 20.1.20.1 255.255.255.0
enable ipforwarding vlan voice
configure vlan guest ipaddress 30.1.30.1 255.255.255.0
enable ipforwarding vlan guest
#
# Module fdb configuration.
#
#
# Module rtmgr configuration.
#
#
# Module mcmgr configuration.
#
#
# Module aaa configuration.
........
........
#
# Module msdp configuration.
#
#
# Module netLogin configuration.
#
#
# Module netTools configuration.
#
configure dns-client add name-server 4.2.2.1 vr VR-Default
enable dhcp vlan inet-gw
#
# Module ntp configuration.
#
#
# Module ospf configuration.
**************************************************************************
Any other thoughts?
Bhavdeep
Thanks for the reply. IP forwarding is enabled on the Vlans. I can ping 192.168.122.175 on port 12 from the other PCs but not 192.168.122.1 - it cannot see that for some reason. The NAT1 device in GNS-3 does not allow for any configuration. Attached below is the config and the message I get back when I ping from VPCS1 (PC 1)...
VPCS> sh ip
NAME : VPCS[1]
IP/MASK : 10.1.10.2/24
GATEWAY : 10.1.10.1
DNS :
MAC : 00:50:79:66:68:02
LPORT : 10012
RHOST:PORT : 127.0.0.1:10013
MTU: : 1500
VPCS> ping 192.168.122.175
84 bytes from 192.168.122.175 icmp_seq=1 ttl=64 time=3.267 ms
84 bytes from 192.168.122.175 icmp_seq=2 ttl=64 time=2.130 ms
84 bytes from 192.168.122.175 icmp_seq=3 ttl=64 time=5.607 ms
84 bytes from 192.168.122.175 icmp_seq=4 ttl=64 time=1.596 ms
84 bytes from 192.168.122.175 icmp_seq=5 ttl=64 time=1.368 ms
VPCS> ping 192.168.122.1
192.168.122.1 icmp_seq=1 timeout
192.168.122.1 icmp_seq=2 timeout
192.168.122.1 icmp_seq=3 timeout
192.168.122.1 icmp_seq=4 timeout
192.168.122.1 icmp_seq=5 timeout
Config File:
configure vlan default delete ports all
configure vr VR-Default delete ports 1-12
configure vr VR-Default add ports 1-12
configure vlan default delete ports 1-12
create vlan "data"
configure vlan data tag 10
create vlan "guest"
configure vlan guest tag 30
create vlan "inet-gw"
configure vlan inet-gw tag 100
create vlan "voice"
configure vlan voice tag 20
configure vlan data add ports 1 untagged
configure vlan guest add ports 3 untagged
configure vlan inet-gw add ports 12 untagged
configure vlan data ipaddress 10.1.10.1 255.255.255.0
enable ipforwarding vlan data
configure vlan voice ipaddress 20.1.20.1 255.255.255.0
enable ipforwarding vlan voice
configure vlan guest ipaddress 30.1.30.1 255.255.255.0
enable ipforwarding vlan guest
#
# Module fdb configuration.
#
#
# Module rtmgr configuration.
#
#
# Module mcmgr configuration.
#
#
# Module aaa configuration.
........
........
#
# Module msdp configuration.
#
#
# Module netLogin configuration.
#
#
# Module netTools configuration.
#
configure dns-client add name-server 4.2.2.1 vr VR-Default
enable dhcp vlan inet-gw
#
# Module ntp configuration.
#
#
# Module ospf configuration.
**************************************************************************
Any other thoughts?
Bhavdeep
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
12-04-2017 01:48 AM
The reason why the ping is successful when pinging from switch may be the source address of that ping request is switch's local 192.168.122.175 which NAT-1 device also knows this network (192.168.122.0/24) as its direct interface.
I think the ping won't be successful when you ping from switch with different source address for example, "ping 8.8.8.8 from 10.1.10.1".
As long as you want to have separated network for each data, voice and guest, appropriate routing is required.
I think the ping won't be successful when you ping from switch with different source address for example, "ping 8.8.8.8 from 10.1.10.1".
As long as you want to have separated network for each data, voice and guest, appropriate routing is required.