- Extreme Networks
- Community List
- Switching & Routing
- ExtremeSwitching (VSP/Fabric Engine)
- Re: VOSS: Clustered Core VIST MLT to Firewall (HA)...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
VOSS: Clustered Core VIST MLT to Firewall (HA) LACP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-06-2022 02:24 AM - edited 11-06-2022 02:26 AM
Hi All,
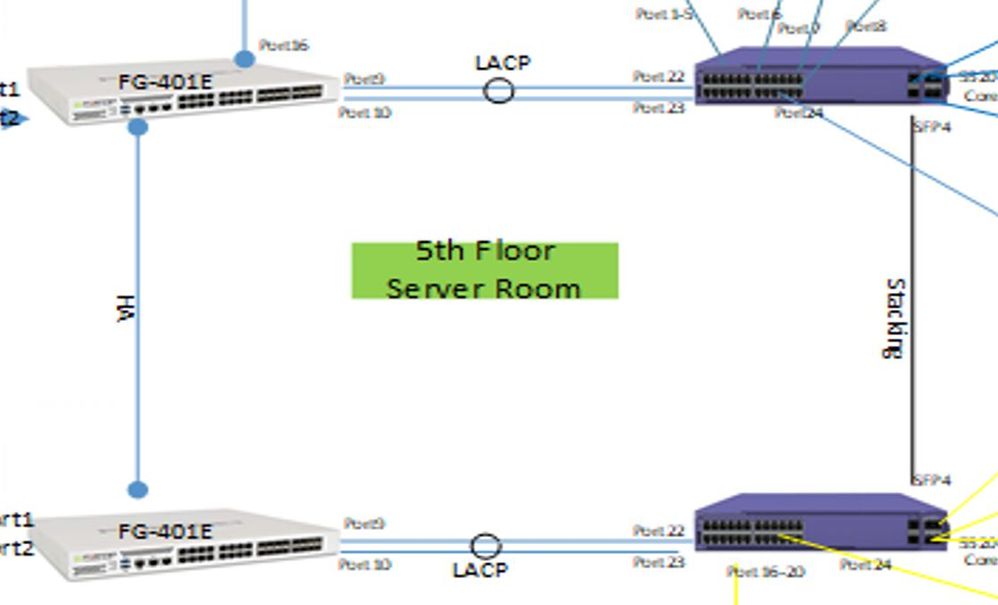
We are planning to add a redundant CORE and FW to the current setup of our client using VIST for the CORE to be clustered and then for the CORE to FW connection we're going to use MLT and LACP for added resilience if ever one port goes down and also before it switches back to CORE2.
May I know if this is feasible (loop-free)? And if there any best practices regarding VOSS implementation for this?
Hoping to hear any suggestions on this. Thank you in advance.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-07-2022 01:58 AM
Hello gklyde17,
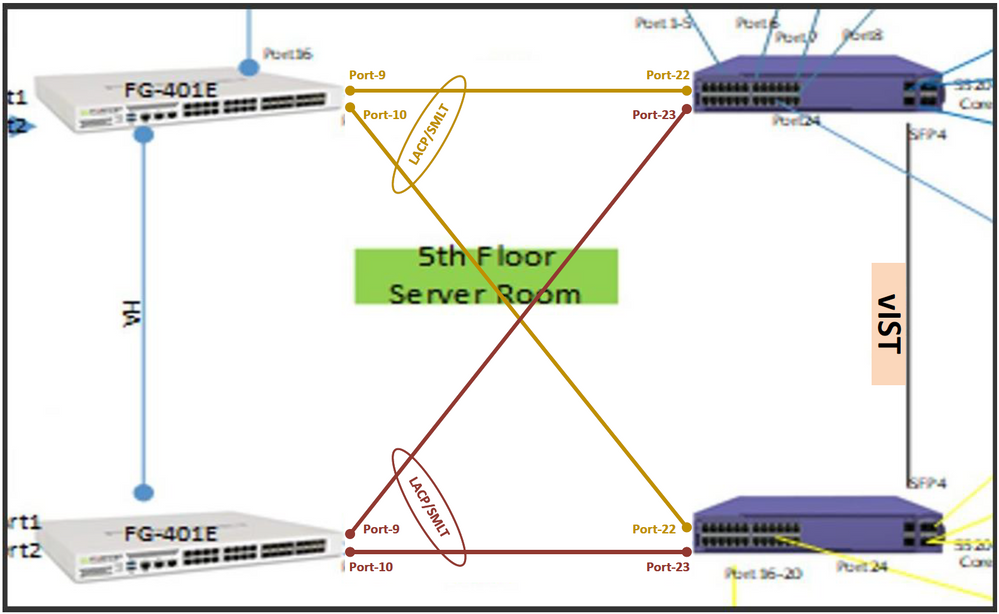
I would prefer to do it as in drawing below
When VSP's are in SMLT/vIST cluster configuration you can connect other devices, eg. a FireWall, servers, switches, ... with a LAG (active or static (LACP active or LACP static or MLT, Etherchanel, ...)) to both VSP switches.
When one of the VSP's fails, both FW's still have one active link.
On the VSP switches you would have a configuration like this.
Only configuration for VSP port 22 / SMLT-22 is shown.
The same configuration must be applied to both SMLT cluster members for both ports/SMLT's.
On both VSP SMLT cluster switches :
mlt 22 enable name "SMLTxyz"
interface mlt 22
smlt
lacp enable key 22
exit
interface GigabitEthernet 22
encapsulation dot1q
exit
interface GigabitEthernet 22
name "SMLT-PORTxyz"
no shutdown
lacp key 22 aggregation enable
lacp enable
no spanning-tree mstp force-port-state enable
exit
Hope it helps
WillyHe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-07-2022 01:58 AM
Hello gklyde17,
I would prefer to do it as in drawing below
When VSP's are in SMLT/vIST cluster configuration you can connect other devices, eg. a FireWall, servers, switches, ... with a LAG (active or static (LACP active or LACP static or MLT, Etherchanel, ...)) to both VSP switches.
When one of the VSP's fails, both FW's still have one active link.
On the VSP switches you would have a configuration like this.
Only configuration for VSP port 22 / SMLT-22 is shown.
The same configuration must be applied to both SMLT cluster members for both ports/SMLT's.
On both VSP SMLT cluster switches :
mlt 22 enable name "SMLTxyz"
interface mlt 22
smlt
lacp enable key 22
exit
interface GigabitEthernet 22
encapsulation dot1q
exit
interface GigabitEthernet 22
name "SMLT-PORTxyz"
no shutdown
lacp key 22 aggregation enable
lacp enable
no spanning-tree mstp force-port-state enable
exit
Hope it helps
WillyHe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-07-2022 12:55 AM
How are the Firewalls configured? Are they in L2 mode bridging traffic between VLANs? If so, then the switches likely will get their own MACs back on the MLT/SMLT ports on a different VLAN than they have sent traffic out. If this is the setup, then you will need to issue this command:
"no sys control virtual-ist mac-move-protection"
This will ensure that the switch MACs are not moved to the vIST automatically as a switch in normal cases does not want to see its own, or its peer MACs on SMLT ports.
If the FWs are in pure routing mode, then this command is not required.
Roger