This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- Log into switch with LDAP credentials
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Log into switch with LDAP credentials
Log into switch with LDAP credentials
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-02-2018 03:02 PM
Currently, we are using accounts created on each switch in order to be able to login.
We do have Extreme Management Center 8.x installed (we have NAC but don't have it fully configured/deployed yet) and have it configured so that users can login to EMC with their LDAP credentials. I know that a user can then use the "Open Device Terminal" via EMC, but we want to know if it is possible (and how we would configure it) so that we can use LDAP accounts instead when they start up PuTTY and SSH to a switch? I have read lots of different posts/articles on this and my head is swimming and need some guidance/clarity. Thanks!
We do have Extreme Management Center 8.x installed (we have NAC but don't have it fully configured/deployed yet) and have it configured so that users can login to EMC with their LDAP credentials. I know that a user can then use the "Open Device Terminal" via EMC, but we want to know if it is possible (and how we would configure it) so that we can use LDAP accounts instead when they start up PuTTY and SSH to a switch? I have read lots of different posts/articles on this and my head is swimming and need some guidance/clarity. Thanks!
18 REPLIES 18
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-04-2018 03:22 PM
That did work (create an AD account called xmc-cli, add it to the domain 'XOS Administrators" account, and then log into the switch as there is now an account that has the same name).
I guess we then just have to remember to update the PW in AD, update it in the "CLI credentials" section of XMC, and update it on each switch for consistency when we change the PW.
I guess we then just have to remember to update the PW in AD, update it in the "CLI credentials" section of XMC, and update it on each switch for consistency when we change the PW.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-04-2018 03:22 PM
Let's say that the user in the Administration -> Profiles is admin, just create a user admin in the AD XOS_Administrators group with the same password that is set in the profiles.
I'm not sure whether there is another solution to the requirement.
I'm not sure whether there is another solution to the requirement.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-04-2018 11:30 AM
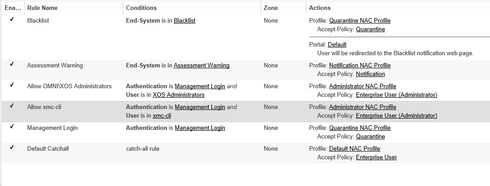
Now I am trying to figure out how to add a second rule that will allow the local xmc-cli account on the switch to be able to login as well. This logic doesn't seem to do it.I don't think that is possible because of the rule before = NAC checks LDAP and it doesn't match and that answer is send back to the switch = failed authentication.
The request never get's to the second rule.
The only thing you'd do is to add the user/pw to the same LDAP group.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-04-2018 11:11 AM
Yes NAC will configure the switch IF you set it correctly and that it's the weird thing in this case.
If you take a look on the last screenshot that you've posted the "auth access type" of the switch is set to network access (= auth for the switch ports but not mgmt access).
That would result in the following switch config...
X440G2.10 # show configuration | i radius
configure radius netlogin 1 server 172.24.24.115 1812 client-ip 172.25.25.156 vr VR-Default
configure radius 1 shared-secret encrypted "#$5gX1NdKu8lL4ySMdBGwB5r1OKu63HA=="
enable radius
disable radius mgmt-access
enable radius netlogin
configure radius timeout 15
As you'd see mgmt-access is disabled.
If you set the NAC switch "auth access type" config to "any acccess" the switch config will also enable radius mgmt-access
X440G2.13 # show configuration | i radius
configure radius 1 server 172.24.24.115 1812 client-ip 172.25.25.156 vr VR-Default
configure radius 1 shared-secret encrypted "#$BqoJkduxAo0xMnKL2uknMYMFLU3Mow=="
enable radius
enable radius mgmt-access
enable radius netlogin
configure radius timeout 15
Some things to keep in mind after some testing...
- it will take 2-3 minutes for NAC to update the switch config - don't test before that is done, check the swtich config
- if you set any auth and then switch back to only network access NAC will not disable back the radius mgmt-access config (not sure whether that is a bug) - in case you'd like to disable it you'd need to do it via switch CLI
If you take a look on the last screenshot that you've posted the "auth access type" of the switch is set to network access (= auth for the switch ports but not mgmt access).
That would result in the following switch config...
X440G2.10 # show configuration | i radius
configure radius netlogin 1 server 172.24.24.115 1812 client-ip 172.25.25.156 vr VR-Default
configure radius 1 shared-secret encrypted "#$5gX1NdKu8lL4ySMdBGwB5r1OKu63HA=="
enable radius
disable radius mgmt-access
enable radius netlogin
configure radius timeout 15
As you'd see mgmt-access is disabled.
If you set the NAC switch "auth access type" config to "any acccess" the switch config will also enable radius mgmt-access
X440G2.13 # show configuration | i radius
configure radius 1 server 172.24.24.115 1812 client-ip 172.25.25.156 vr VR-Default
configure radius 1 shared-secret encrypted "#$BqoJkduxAo0xMnKL2uknMYMFLU3Mow=="
enable radius
enable radius mgmt-access
enable radius netlogin
configure radius timeout 15
Some things to keep in mind after some testing...
- it will take 2-3 minutes for NAC to update the switch config - don't test before that is done, check the swtich config
- if you set any auth and then switch back to only network access NAC will not disable back the radius mgmt-access config (not sure whether that is a bug) - in case you'd like to disable it you'd need to do it via switch CLI
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-04-2018 10:20 AM
Yes, this is a test node. Our SA warned us to not try anything (mgmt access, etc.) on production.
I had not made any of the RADIUS changes from the KB article that I linked, but I didn't have to. I changed the Attribute Value to have the correct OU and now things are working. I guess the RADIUS settings are automatically applied to the switch with no need for the user to make the changes.
Now I am trying to figure out how to add a second rule that will allow the local xmc-cli account on the switch to be able to login as well. This logic doesn't seem to do it.
I had not made any of the RADIUS changes from the KB article that I linked, but I didn't have to. I changed the Attribute Value to have the correct OU and now things are working. I guess the RADIUS settings are automatically applied to the switch with no need for the user to make the changes.
Now I am trying to figure out how to add a second rule that will allow the local xmc-cli account on the switch to be able to login as well. This logic doesn't seem to do it.