This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- RE: Remote AP's fail to connect to controller
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Remote AP's fail to connect to controller
Remote AP's fail to connect to controller
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-27-2014 01:45 PM
This is my first time working with Extreme Networks equipment so excuse any lack of knowledge I may have on these products.
The clinic I work for has 3 locations connected via WatchGuard Remote Office VPN. Subnets are as follows with the WatchGuard firewalls doing the routing:
Main Office: 172.20.1.0/24
Remote Office 1: 172.20.2.0/24
Remote Office 2: 172.20.3.0/24
We have a C25 Controller running v09.12.01.0067 located at the Main Office with IP 172.20.1.25.
We have 13 total AP-3825i AP's with 9 at the Main Office, and 2 at each Remote Office.
The Main Office has a Microsoft DHCP server and the Remote Office's get their DHCP addresses from their respective WatchGuard firewalls.
A security firm has control of the WatchGuard firewalls so I don't have direct access to their configuration and I'm not sure if the WatchGuard supports option 43. Because of this, it is why I took the following steps;
I installed the AP's at the Main Office and they connected up to the controller and are working beautifully! Because I couldn't add the Option 43 to the remote WatchGuard's, I connected the 4 Remote Office AP's to the Main Office network so they would obtain a DHCP address and configuration. Once the software was upgraded, I changed the IP's to manual IP's (172.20.2.x and 172.20.3.x) and set the controller IP as well.
I installed the AP's at the Remote Office locations but they show up on the controller as Inactive Local AP's even though I can ping and SSH into each AP from the Main Office. I can also ping the controller from the Remote Office's. This tells me that they are being seen on the network but something is keeping them from connecting to the controller properly.
Any idea's or suggestions is greatly appreciated!
The clinic I work for has 3 locations connected via WatchGuard Remote Office VPN. Subnets are as follows with the WatchGuard firewalls doing the routing:
Main Office: 172.20.1.0/24
Remote Office 1: 172.20.2.0/24
Remote Office 2: 172.20.3.0/24
We have a C25 Controller running v09.12.01.0067 located at the Main Office with IP 172.20.1.25.
We have 13 total AP-3825i AP's with 9 at the Main Office, and 2 at each Remote Office.
The Main Office has a Microsoft DHCP server and the Remote Office's get their DHCP addresses from their respective WatchGuard firewalls.
A security firm has control of the WatchGuard firewalls so I don't have direct access to their configuration and I'm not sure if the WatchGuard supports option 43. Because of this, it is why I took the following steps;
I installed the AP's at the Main Office and they connected up to the controller and are working beautifully! Because I couldn't add the Option 43 to the remote WatchGuard's, I connected the 4 Remote Office AP's to the Main Office network so they would obtain a DHCP address and configuration. Once the software was upgraded, I changed the IP's to manual IP's (172.20.2.x and 172.20.3.x) and set the controller IP as well.
I installed the AP's at the Remote Office locations but they show up on the controller as Inactive Local AP's even though I can ping and SSH into each AP from the Main Office. I can also ping the controller from the Remote Office's. This tells me that they are being seen on the network but something is keeping them from connecting to the controller properly.
Any idea's or suggestions is greatly appreciated!
21 REPLIES 21
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-01-2014 02:38 AM
Looks like the AP is not approved so go to > AP > Bulk Configuration > Access Approval
If the status is pending select the AP and hit approve.
Then either wait 5minutes (every 5 minutes the AP restarts the discovery) or reboot the AP.
If the status is pending select the AP and hit approve.
Then either wait 5minutes (every 5 minutes the AP restarts the discovery) or reboot the AP.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-01-2014 01:23 AM
John...I agree, they are difficult to deal with and the static IP is just an excuse. I'll get wire shark loaded up this weekend and I'll run what you suggested.
Ron...I set the AuthIP address and I started getting some entries in the controller log (they keep repeating);
The AP Log now looks more like your example;
The controller is still showing the AP as inactive.
Ron...I set the AuthIP address and I started getting some entries in the controller log (they keep repeating);
The AP Log now looks more like your example;
The controller is still showing the AP as inactive.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-31-2014 12:23 PM
The static config of the AP looks OK... if the IPs are correct....
dhcp mode disable (0)
ip 172.20.3.91
mask 255.255.255.0
gateway 172.20.3.30
Please check whether the AC IP is set with....
cat /home/config/current.cfg | grep "cset auth"
If the output is "cset authIpAddr 1 172.20.1.25" then it's OK if there is no output please set the IP with...
cset authip 1 172.20.1.25
capply
csave
reboot
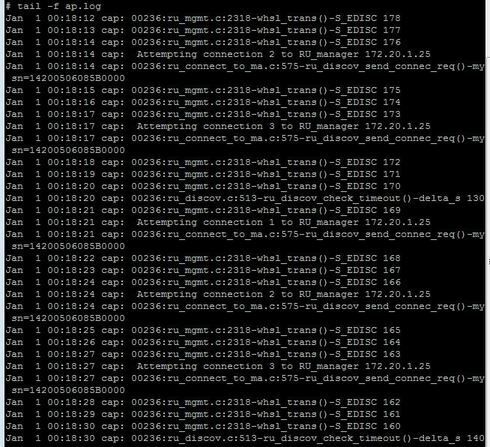
I think the AP didn't know the controller IP as the log should look like this....
As you'd see my AP try to connect to my controller/RUmanager = 20.20.20.20 all the time.
dhcp mode disable (0)
ip 172.20.3.91
mask 255.255.255.0
gateway 172.20.3.30
Please check whether the AC IP is set with....
cat /home/config/current.cfg | grep "cset auth"
If the output is "cset authIpAddr 1 172.20.1.25" then it's OK if there is no output please set the IP with...
cset authip 1 172.20.1.25
capply
csave
reboot
I think the AP didn't know the controller IP as the log should look like this....
As you'd see my AP try to connect to my controller/RUmanager = 20.20.20.20 all the time.
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-31-2014 11:45 AM
The log on the AP doesn't mean much to me. Can you ping the controller from the AP? If yes do you see any UDP traffic hitting your controller from the AP? You can ssh into the controller and do a tcpdump to find out.
Once you login you are in the CLI for the wireless management for the controller. To get to the Linux kernel you have to type 'shell' and submit your admin password again.
Once there you can do an ifconfig to find out the interface name of your management address.
For me it is csi1. So I do a tcpdump -i csi1 -w mypcapfile.pcap and then boot up your AP.
Let that run for a few minutes then FTP that file off of the server and get it onto a box with Wireshark. Then in Wireshark do a filter for the IP address of your AP and see what you get.
It will tell you if the AP is connecting via TCP but not UDP or if it is not connecting at all etc. It will help you when dealing with the 3rd party because you will know exactly what the issue is.
I don't see the logic behind not allowing UDP 13910 if you are getting a DHCP address from the ISP. Your tunnel is either secure or it is not and opening UDP 13910 from your AP to the wireless controller is not going to bring down your network.
Sounds to me like they just want you to have a static IP because it is easier to manage a VPN that way.
John
Once you login you are in the CLI for the wireless management for the controller. To get to the Linux kernel you have to type 'shell' and submit your admin password again.
Once there you can do an ifconfig to find out the interface name of your management address.
For me it is csi1. So I do a tcpdump -i csi1 -w mypcapfile.pcap and then boot up your AP.
Let that run for a few minutes then FTP that file off of the server and get it onto a box with Wireshark. Then in Wireshark do a filter for the IP address of your AP and see what you get.
It will tell you if the AP is connecting via TCP but not UDP or if it is not connecting at all etc. It will help you when dealing with the 3rd party because you will know exactly what the issue is.
I don't see the logic behind not allowing UDP 13910 if you are getting a DHCP address from the ISP. Your tunnel is either secure or it is not and opening UDP 13910 from your AP to the wireless controller is not going to bring down your network.
Sounds to me like they just want you to have a static IP because it is easier to manage a VPN that way.
John
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
07-31-2014 12:23 AM
Thanks Ron and John for the replies!
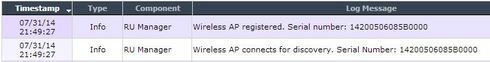
I set the controller log level to information and restarted one of the remote AP's which resulted in nothing being logged. I then restarted one of the local AP's and I received entries like those in your screenshot.
Here are the results from the cget config global query;
AP3825i 09.12.01.0067 interactive shell for service personnel only# cget config global
Reboot is needed due to config change: FALSE
AP authentication is needed due to config change: FALSE
sysName "AP3825i"
acSiteName ""
lastAcIp 172.20.1.25
#site cfg:
site disabled
wipsMode 0
Real capture off
timeServer
LEDMode Normal
macFilterMode Deny
AP ThirdPartyMode 0
AP TunnelMode 0
Wassp VlanVid: -1
countryCode 840
broadcastDisassociation 0
modePersistence 0
linkPersistence 1
pollTimeout 15000
pollInterval 3000
ssh mode enable (1)
ssh timeout 180
password $1$.bwL4$Own82WonXWgXrcl89e7aQ1
slpuRetry 3
slpuTimeout 3
dnsRetry 3
dnsTimeout 3
slpmRetry 3
slpmTimeout 3
globalRetry 3
globalTimeout 3
LLDP disable (0), TimeToLive:120,AnnouncementIntervall:30,AnnouncementDelay:2
logAlarm severity major (4)
apName 14200506085B0000
hostName AP3825i-14200506085B0000
apDesc
Ethernet(Phy): Speed:100 Duplex:full Auto:on Link:on
Ethernet (apcfg): Speed auto
dhcp mode disable (0)
ip 172.20.3.91
mask 255.255.255.0
gateway 172.20.3.30
eth0 MAC 20:B3:99:E4:2B:A2
Static MTU 1500
Jumbo Frame: Disabled
MIC Error Threshold 2
IASDNSPrefix 1
airfairLevel 4
radio 0 antennaType left 0x0 middle 0x0 right 0x0
radio 1 antennaType left 0x0 middle 0x0 right 0x0
radio 2 antennaType left 0x0 middle 0x0 right 0x0
outDoorChan 0
High Throughput HT capability for WEP and TKIP is disable (0)
Sending HT on all Probe Response is disable (0)
lbsSrcIp 0.0.0.0
lbsSrcPort 1144
lbsDstIp 0.0.0.0
lbsDstPort 0
lbsMcast 00:00:00:00:00:00
lbsTagMode 2
SNMP SERVER ENABLE disable
interAPRoam 0
clusterEncryption 1
clusterPassword OmKZlkEg
Band Preference Admin Disabled (raw bitmap 0 0 ) Oper Disabled
radioPreferenceTimeout 300
bandPreferenceAssocThreshold 0
bandPreferenceAssocPeriod 0
AC Mgmt Mac Addr 68:05:ca:23:d9:99
Mesh RSSI Sample Window integer of power 2 3
Mesh Link Quality Check Timer 1
Mesh Stability Factor 20
isMesh 0
Sniffer radio bitmap 0x0
AP role 0
Dual eth wired0 Admin UP Oper UP act
Dual eth wired1 Admin DOWN Oper DOWN
Lag: 0
Multicast Assembly: Disabled
Location Service: Disabled
Location Auto Collect: Disabled
Location Ondemand MAC List is empty, 0 MAC addresses
FixedAppPolicy Table: appId 1 numFields 1
FixedAppPolicy Table: appId 1 index 0 offset 0x0 mask 0x8000 val 0x0
FixedAppPolicy Table: appId 2 numFields 1
FixedAppPolicy Table: appId 2 index 0 offset 0x0 mask 0x8000 val 0x8000
FixedAppPolicy Table: appId 3 numFields 2
FixedAppPolicy Table: appId 3 index 0 offset 0x0 0x1 mask 0xffffffff 0xffffffff val 0x4d2d5345 0x41524348
FixedAppPolicy Table: appId 4 numFields 2
FixedAppPolicy Table: appId 4 index 0 offset 0x0 0x1 mask 0xffffffff 0xffff0000 val 0x4e4f5449 0x46590000
FixedAppPolicy Table: appId 5 numFields 1
FixedAppPolicy Table: appId 5 index 0 offset 0x0 mask 0xffffffff val 0x0
FixedAppPolicy Table: appId 6 numFields 1
FixedAppPolicy Table: appId 6 index 0 offset 0x0 mask 0xffffffff val 0x8400
And the AP Log;
AP3825i 09.12.01.0067 interactive shell for service personnel only# cd /tmp/log
# tail -f ap.log
Jan 1 00:11:14 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 281
Jan 1 00:11:15 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 20
Jan 1 00:11:15 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 280
Jan 1 00:11:16 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 279
Jan 1 00:11:17 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 278
Jan 1 00:11:18 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 277
Jan 1 00:11:19 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 276
Jan 1 00:11:20 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 275
Jan 1 00:11:21 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 274
Jan 1 00:11:22 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 273
Jan 1 00:11:23 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 272
Jan 1 00:11:24 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 271
Jan 1 00:11:25 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 30
Jan 1 00:11:25 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 270
Jan 1 00:11:26 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 269
Jan 1 00:11:27 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 268
Jan 1 00:11:28 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 267
Jan 1 00:11:29 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 266
Jan 1 00:11:30 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 265
Jan 1 00:11:31 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 264
Jan 1 00:11:32 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 263
Jan 1 00:11:33 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 262
Jan 1 00:11:34 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 261
Jan 1 00:11:35 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 40
Jan 1 00:11:35 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 260
Jan 1 00:11:36 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 259
Jan 1 00:11:37 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 258
Jan 1 00:11:38 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 257
Jan 1 00:11:39 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 256
Jan 1 00:11:40 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 255
Jan 1 00:11:41 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 254
Jan 1 00:11:42 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 253
Jan 1 00:11:43 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 252
Jan 1 00:11:44 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 251
Jan 1 00:11:45 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 50
Jan 1 00:11:45 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 250
Jan 1 00:11:46 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 249
Jan 1 00:11:47 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 248
Jan 1 00:11:48 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 247
Jan 1 00:11:49 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 246
Jan 1 00:11:50 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 245
Jan 1 00:11:51 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 244
Jan 1 00:11:52 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 243
Jan 1 00:11:53 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 242
Jan 1 00:11:54 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 241
Jan 1 00:11:55 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 60
Jan 1 00:11:55 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 240
Jan 1 00:11:56 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 239
Jan 1 00:11:57 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 238
Jan 1 00:11:58 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 237
Jan 1 00:11:59 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 236
Jan 1 00:12:00 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 235
Jan 1 00:12:01 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 234
Jan 1 00:12:02 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 233
Jan 1 00:12:03 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 232
Jan 1 00:12:04 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 231
Jan 1 00:12:05 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 70
Jan 1 00:12:05 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 230
Jan 1 00:12:06 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 229
Jan 1 00:12:07 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 228
Jan 1 00:12:08 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 227
Jan 1 00:12:09 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 226
Jan 1 00:12:10 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 225
Jan 1 00:12:11 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 224
Jan 1 00:12:12 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 223
Jan 1 00:12:13 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 222
Jan 1 00:12:14 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 221
Jan 1 00:12:15 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 80
Jan 1 00:12:15 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 220
Jan 1 00:12:16 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 219
Jan 1 00:12:17 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 218
Jan 1 00:12:18 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 217
Jan 1 00:12:19 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 216
Jan 1 00:12:20 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 215
Jan 1 00:12:21 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 214
Jan 1 00:12:22 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 213
Jan 1 00:12:23 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 212
Jan 1 00:12:24 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 211
Our firewalls are managed by a 3rd party and I requested that UDP port 13910 be allowed. During discussion with the 3rd party, we've discovered that the 3 clinic firewalls are receiving DHCP addresses from our ISP instead of having static ones assigned. Because of this, they won't open the port until we get static IP's assigned to the firewalls which I'm currently working on. Once that's accomplished, then I'll be able to see if UDP port 13910 will resolve it.
Is there anything in the AP log or config that jumps out?
Thanks again for taking the time to look at this!
Craig
I set the controller log level to information and restarted one of the remote AP's which resulted in nothing being logged. I then restarted one of the local AP's and I received entries like those in your screenshot.
Here are the results from the cget config global query;
AP3825i 09.12.01.0067 interactive shell for service personnel only# cget config global
Reboot is needed due to config change: FALSE
AP authentication is needed due to config change: FALSE
sysName "AP3825i"
acSiteName ""
lastAcIp 172.20.1.25
#site cfg:
site disabled
wipsMode 0
Real capture off
timeServer
LEDMode Normal
macFilterMode Deny
AP ThirdPartyMode 0
AP TunnelMode 0
Wassp VlanVid: -1
countryCode 840
broadcastDisassociation 0
modePersistence 0
linkPersistence 1
pollTimeout 15000
pollInterval 3000
ssh mode enable (1)
ssh timeout 180
password $1$.bwL4$Own82WonXWgXrcl89e7aQ1
slpuRetry 3
slpuTimeout 3
dnsRetry 3
dnsTimeout 3
slpmRetry 3
slpmTimeout 3
globalRetry 3
globalTimeout 3
LLDP disable (0), TimeToLive:120,AnnouncementIntervall:30,AnnouncementDelay:2
logAlarm severity major (4)
apName 14200506085B0000
hostName AP3825i-14200506085B0000
apDesc
Ethernet(Phy): Speed:100 Duplex:full Auto:on Link:on
Ethernet (apcfg): Speed auto
dhcp mode disable (0)
ip 172.20.3.91
mask 255.255.255.0
gateway 172.20.3.30
eth0 MAC 20:B3:99:E4:2B:A2
Static MTU 1500
Jumbo Frame: Disabled
MIC Error Threshold 2
IASDNSPrefix 1
airfairLevel 4
radio 0 antennaType left 0x0 middle 0x0 right 0x0
radio 1 antennaType left 0x0 middle 0x0 right 0x0
radio 2 antennaType left 0x0 middle 0x0 right 0x0
outDoorChan 0
High Throughput HT capability for WEP and TKIP is disable (0)
Sending HT on all Probe Response is disable (0)
lbsSrcIp 0.0.0.0
lbsSrcPort 1144
lbsDstIp 0.0.0.0
lbsDstPort 0
lbsMcast 00:00:00:00:00:00
lbsTagMode 2
SNMP SERVER ENABLE disable
interAPRoam 0
clusterEncryption 1
clusterPassword OmKZlkEg
Band Preference Admin Disabled (raw bitmap 0 0 ) Oper Disabled
radioPreferenceTimeout 300
bandPreferenceAssocThreshold 0
bandPreferenceAssocPeriod 0
AC Mgmt Mac Addr 68:05:ca:23:d9:99
Mesh RSSI Sample Window integer of power 2 3
Mesh Link Quality Check Timer 1
Mesh Stability Factor 20
isMesh 0
Sniffer radio bitmap 0x0
AP role 0
Dual eth wired0 Admin UP Oper UP act
Dual eth wired1 Admin DOWN Oper DOWN
Lag: 0
Multicast Assembly: Disabled
Location Service: Disabled
Location Auto Collect: Disabled
Location Ondemand MAC List is empty, 0 MAC addresses
FixedAppPolicy Table: appId 1 numFields 1
FixedAppPolicy Table: appId 1 index 0 offset 0x0 mask 0x8000 val 0x0
FixedAppPolicy Table: appId 2 numFields 1
FixedAppPolicy Table: appId 2 index 0 offset 0x0 mask 0x8000 val 0x8000
FixedAppPolicy Table: appId 3 numFields 2
FixedAppPolicy Table: appId 3 index 0 offset 0x0 0x1 mask 0xffffffff 0xffffffff val 0x4d2d5345 0x41524348
FixedAppPolicy Table: appId 4 numFields 2
FixedAppPolicy Table: appId 4 index 0 offset 0x0 0x1 mask 0xffffffff 0xffff0000 val 0x4e4f5449 0x46590000
FixedAppPolicy Table: appId 5 numFields 1
FixedAppPolicy Table: appId 5 index 0 offset 0x0 mask 0xffffffff val 0x0
FixedAppPolicy Table: appId 6 numFields 1
FixedAppPolicy Table: appId 6 index 0 offset 0x0 mask 0xffffffff val 0x8400
And the AP Log;
AP3825i 09.12.01.0067 interactive shell for service personnel only# cd /tmp/log
# tail -f ap.log
Jan 1 00:11:14 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 281
Jan 1 00:11:15 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 20
Jan 1 00:11:15 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 280
Jan 1 00:11:16 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 279
Jan 1 00:11:17 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 278
Jan 1 00:11:18 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 277
Jan 1 00:11:19 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 276
Jan 1 00:11:20 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 275
Jan 1 00:11:21 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 274
Jan 1 00:11:22 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 273
Jan 1 00:11:23 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 272
Jan 1 00:11:24 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 271
Jan 1 00:11:25 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 30
Jan 1 00:11:25 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 270
Jan 1 00:11:26 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 269
Jan 1 00:11:27 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 268
Jan 1 00:11:28 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 267
Jan 1 00:11:29 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 266
Jan 1 00:11:30 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 265
Jan 1 00:11:31 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 264
Jan 1 00:11:32 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 263
Jan 1 00:11:33 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 262
Jan 1 00:11:34 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 261
Jan 1 00:11:35 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 40
Jan 1 00:11:35 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 260
Jan 1 00:11:36 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 259
Jan 1 00:11:37 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 258
Jan 1 00:11:38 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 257
Jan 1 00:11:39 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 256
Jan 1 00:11:40 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 255
Jan 1 00:11:41 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 254
Jan 1 00:11:42 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 253
Jan 1 00:11:43 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 252
Jan 1 00:11:44 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 251
Jan 1 00:11:45 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 50
Jan 1 00:11:45 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 250
Jan 1 00:11:46 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 249
Jan 1 00:11:47 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 248
Jan 1 00:11:48 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 247
Jan 1 00:11:49 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 246
Jan 1 00:11:50 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 245
Jan 1 00:11:51 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 244
Jan 1 00:11:52 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 243
Jan 1 00:11:53 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 242
Jan 1 00:11:54 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 241
Jan 1 00:11:55 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 60
Jan 1 00:11:55 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 240
Jan 1 00:11:56 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 239
Jan 1 00:11:57 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 238
Jan 1 00:11:58 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 237
Jan 1 00:11:59 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 236
Jan 1 00:12:00 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 235
Jan 1 00:12:01 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 234
Jan 1 00:12:02 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 233
Jan 1 00:12:03 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 232
Jan 1 00:12:04 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 231
Jan 1 00:12:05 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 70
Jan 1 00:12:05 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 230
Jan 1 00:12:06 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 229
Jan 1 00:12:07 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 228
Jan 1 00:12:08 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 227
Jan 1 00:12:09 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 226
Jan 1 00:12:10 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 225
Jan 1 00:12:11 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 224
Jan 1 00:12:12 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 223
Jan 1 00:12:13 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 222
Jan 1 00:12:14 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 221
Jan 1 00:12:15 cap: 00235:ru_discov.c:513-ru_discov_check_timeout()-delta_s 80
Jan 1 00:12:15 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 220
Jan 1 00:12:16 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 219
Jan 1 00:12:17 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 218
Jan 1 00:12:18 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 217
Jan 1 00:12:19 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 216
Jan 1 00:12:20 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 215
Jan 1 00:12:21 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 214
Jan 1 00:12:22 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 213
Jan 1 00:12:23 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 212
Jan 1 00:12:24 cap: 00235:ru_mgmt.c:2318-whsl_trans()-S_EDISC 211
Our firewalls are managed by a 3rd party and I requested that UDP port 13910 be allowed. During discussion with the 3rd party, we've discovered that the 3 clinic firewalls are receiving DHCP addresses from our ISP instead of having static ones assigned. Because of this, they won't open the port until we get static IP's assigned to the firewalls which I'm currently working on. Once that's accomplished, then I'll be able to see if UDP port 13910 will resolve it.
Is there anything in the AP log or config that jumps out?
Thanks again for taking the time to look at this!
Craig