- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (Identifi)
- Single SSID mapping to multiple topologies not wor...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Single SSID mapping to multiple topologies not working as expected
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
10-31-2019 11:25 AM
Hi
I’m trying to achieve a simple “map to role based on RADIUS response” setup - there is a single SSID, and I want to place this into either a ‘access_filtered’ or an ‘access_normal’ VLAN. The filtering is all done externally, so as far as the wireless side of the network is concerned it is simply a case of placing the traffic into the correct VLAN. This should be very easy to do, but I’m clearly missing something.
In testing this, I seem to keep finding my traffic bridged at the AP, rather than going back to the controller. Other tests work, but then if I try and switch VLAN, it doesn’t reliably do so.
I can’t work out where I’ve gone wrong here - the documentation (including official EXTR training notes) isn’t great and shows parts of the config in isolation, so I’m not certain I have this correctly configured.
The controllers are C35s running 10.31.03.0012 software - I appreciate that’s a bit old now but still I’d expect this to work.
I have the following setup:
- Topology: access_120 on VLAN 120, B@EWC Layer 2: The unfiltered access VLAN.
- Topology: accessfiltered_122 on VLAN 122, B@EWC Layer 2: The filtered access VLAN.
- Roles: A corresponding role for each, however, in the roles screen, they show as “Bridge at AC” - which is, I think, where things are going wrong. I have a role called “access_filtered” and “access_normal” these (in the advanced screen) map to the relevant VLANs for each of them. I also have an “Allow_All” role that permits everything without any kind of VLAN mapping.
- In the WLAN Service for the SSID I’m using, I have no default topology set.
- In the Global RFC3580 options screen, I have tried the following:
- Filter-ID only, and specified a VLAN ID of 120 mapping to role access_normal, and a VLAN ID of 122 mapping to a role of access_filtered. In this setup, if I reply with a Filter-ID of “120” or “122” (as a string) my client seems to end up on the untagged VLAN of the AP itself.
- Both Filter-ID and Tunnel-Private-Group-IP; returning a filter ID of “Allow_All” and a Private-Grp-Id of “access_filtered” - the client ends up in no network at all. I’ve also tried a Private-Grp-Id of “122” and that seems to work, but if I then try and change to a Private-Grp-Id of “120” it doesn’t reliably change to the other VLAN. The problem here isn’t DHCP remembering the old lease either - I’ve released/renewed to no avail.
I know that the correct attributes are being returned by the RADIUS server (NPS, which is its own pile of pain) as I’m capturing the traffic relating to each test to be sure - the controllers certainly get the right responses in the Access-Accept packets from the RADIUS server.
What am I doing wrong here?
As a bonus followup question (because doing what I want in NPS is hard work) is there a way to set one topology in the WLAN services (for example, my access_filtered topology) and override that with a FIlter-Id/Private-Grp-Id in the Access-Accept for specific users? The end result being that if a user didn’t specify anything in their RADIUS response, they’d get the default filtered topology but if there was a (correct) Filter-Id/Private-Grp-Id in the response they would end up in the VLAN specified?
Paul.
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-01-2019 07:13 AM
Roles: A corresponding role for each, however, in the roles screen, they show as “Bridge at AC” - which is, I think, where things are going wrong.
bridge@AC is the same as bridge@EWC so that is OK.
Here a example of a role - you don’t need to set anything in the advanced settings of the roles.
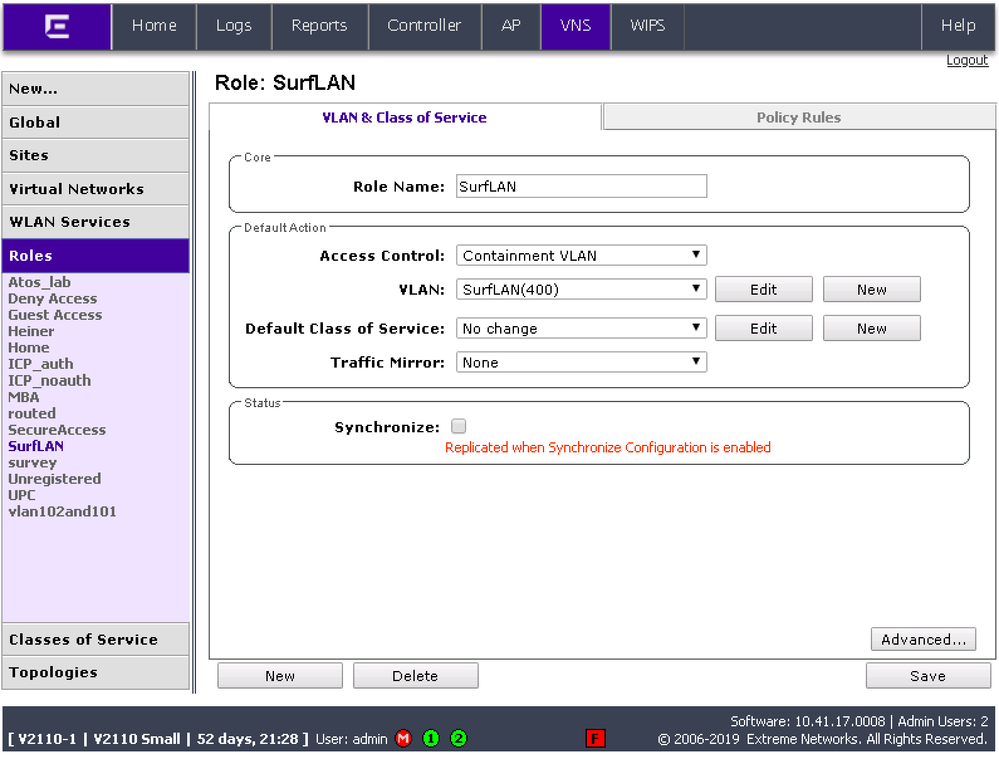
NPS filter ID - just set the controller to RADIUS fiter ID and make sure that the role and topology have the same name as the returned filter ID from the NPS.
-Ron
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-01-2019 08:15 PM
A followup for the archives.
When I was creating the role, I hadn’t selected ‘Containment VLAN’ - I was using the advanced option to set the VLAN. This didn’t work.
Once configured correctly, setting the Filter-Id to the role’s name just works as expected.
It also works as expected when you set a default topology in the WLAN service screen; and then override it with a Filter-Id in the Access-Accept.
Thanks to Ron for the steer in the right direction.
Paul.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
11-01-2019 07:13 AM
Roles: A corresponding role for each, however, in the roles screen, they show as “Bridge at AC” - which is, I think, where things are going wrong.
bridge@AC is the same as bridge@EWC so that is OK.
Here a example of a role - you don’t need to set anything in the advanced settings of the roles.

NPS filter ID - just set the controller to RADIUS fiter ID and make sure that the role and topology have the same name as the returned filter ID from the NPS.
-Ron
