- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeCloud IQ- Site Engine Management Center
- Re: Web Redirect to captive portal for Cisco switc...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Web Redirect to captive portal for Cisco switch with Per-User-ACL (dACL)
Web Redirect to captive portal for Cisco switch with Per-User-ACL (dACL)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-13-2022 11:26 AM
I've defined the new switch in the NAC engine with the follow radius attributes:
 And my Policy mapping for the role were user assume for the web authentication redirection is:
And my Policy mapping for the role were user assume for the web authentication redirection is:
If I try to use the redirect method that use Policy Based Routing as I do for X450-G2, I've got and error that Cisco don't support CoS defined as I do in the redirect rule for EXOS:
When the device is authenticated, is not redirected to the Extreme NAC captive portal (my ip in the lab is 192.168.30.35)
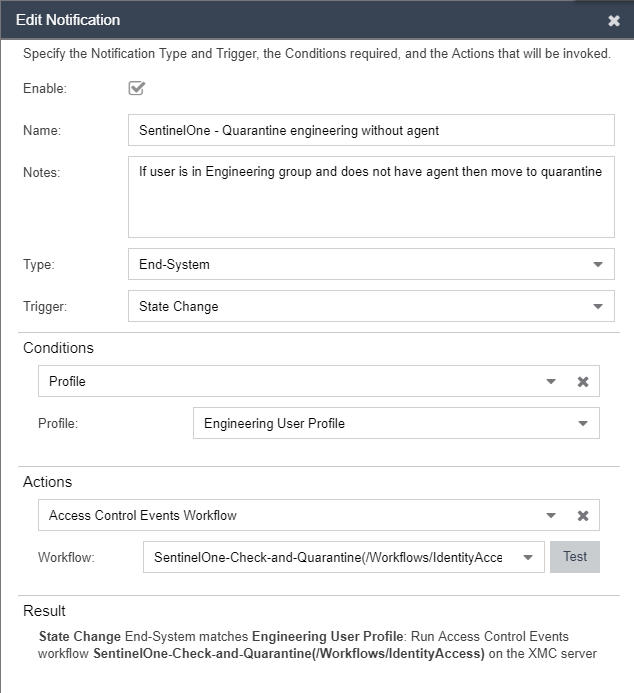
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
06-01-2022 09:04 AM
The problem was my http server on cisco switch with no ip address on the non default vlan ...giving an IP the redirect works.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-26-2022 04:05 PM
now web redirection with Per-User-ACL works in my lab.
My access ports are configured as:
interface GigabitEthernet0/x
switchport access vlan 10
switchport mode access
and the uplink port between my cisco and x450-g2 is
interface GigabitEthernet0/1
description "Uplink with X450-G2 port 16"
switchport trunk native vlan 10
switchport mode trunk
If I use the VLAN 10 in my policy mapping for the Policy Role, and all works well, in the sense that the web redirection works well, and also if I connect with a user with a policy role in where I set a different VLAN, this is correctly set in the port.
But If I use a different VLAN in the Policy role used for the web redirection (for example a different on-boarding vlan that is not the native VLAN defined in my trunk uplink interface) , the redirection on cisco switch in this case don't work.
Any ideas?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-16-2022 05:33 AM
Hi Ryan,
my intention is to use only Per-user-ACL with Cisco in my configuration, so if Custom2 and Custom3 attributes are not necessary with this method, I remove these from my configuration, but in this case I don’t know how to redirect my guest user to the NAC porta using only the Policy Roles and services associated to my Redirect Role Profile (I’m using PBR only for the Extreme’s switches and I use the CoS in the http rule in the Policy Domain associated to these switches only).
Do you have and example on how use dACL with web redirect?
Thanks,
Antonio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
05-15-2022 08:59 PM
Hello,
I have a few questions based on your screenshots.
If you check the "Authorization" column in control what was actually sent for authorization? Did Control actually send the per-user ACL lines or did it send the custom2 and customer3 AVPs which is typically what we seen when using cisco.
These custom2 and custom3 attributes use a web based redirect and not a PBR. You should only need one or the other, so if you're using the redirect ACL with URL redirect you don't need PBR to redirect as well. You won't need to redirect packets that have already been redirected to NAC URL.
If you take a packet capture on a client in this state do you see the clients web packets get a 307 Temporary Redirect with the URL you configured?
Yes we have per-user-ACL capabilities with Cisco where we can send the ACL lines through RADIUS attributes, but you appear to not be using that by using the cisco-avipair=redirecturl attribute.
Thanks
-Ryan
