- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeControl
- Can't send untagged VLAN using FA-VLAN-ISID from N...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can't send untagged VLAN using FA-VLAN-ISID from NAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-04-2023 10:30 PM
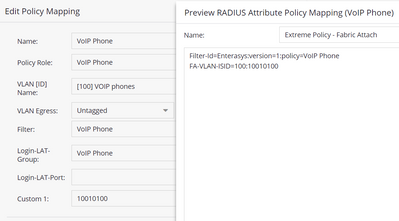
I am moving from using LLDP to send a voice VLAN, to using ExtremeControl to do the same, with Fabric Attach on an EXOS switch. This means sending the VLAN untagged instead of tagged, with FA-VLAN-ISID set to 0:10010100 (where 10010100 is my Voice I-SID) per https://extremeportal.force.com/ExtrArticleDetail?an=000104792 and https://extremeportal.force.com/ExtrArticleDetail?an=000105350
But I can't get NAC to send that value - either it sends FA-VLAN-ISID=100:10010100 (as 100 is the Voice VLAN tag) or if I set the VLAN to None, it doesn't send FA-VLAN-ISID at all. Changing the VLAN egress to Untagged doesn't have the desired effect:
Is there a way to get this to work or do I need to open a case with TAC?
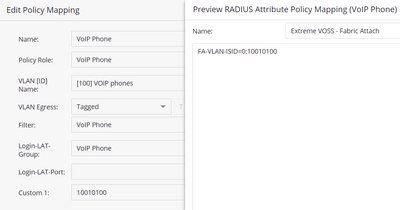
I also want to do this with VOSS instead of NEAP with LLDP, since that doesn't send any information to XIQ-SE (and in XIQ it shows the onboarding VLAN, not the auto-sense voice I-SID/VLAN). Although with VOSS it does the opposite and always sends 0:10010100:
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-06-2023 12:09 AM
Hi James_A
can you please clarify what is your goal? If you send FA-VLAN:ISID=0:10010100 then it should be untagged on egress and on ingress it goes to 10010100 I-SID.
Another approach is the combination of AutoSense and NAC and LLDP:
If you want the phone to appear in XIQ-SE access control end-stations, i.e. the phone to RADIUS authenticate, while still benefiting from LLDP-Med on the switch the recipe is:
- Set the global auto-sense voice I-SID / VLAN-id on the switch
- Let the access ports have auto-sense enabled
- Do not enable LLDP-auth for the phones
- On the RADIUS server side (access control policy mapping or Policy role) DO NOT return ANY VLAN/I-SID via RADIUS
The phone will then:
- Get the Voice VLAN from LLDP as well as other phone related LLDP parameters, like Qos, etc
- The phones’ MAC will be used for RADIUS MAC authentication (or EAP auth if using TLS…)
- The switch auto-sense port will have already positioned the auto-sense Voice I-SID/VLAN on the access port
- When/if the RADIUS server returns “Permit”, then the phone is allowed to send traffic onto the Voice VLAN (NOTE, the RADIUS response must not return any I-SID/VLAN; no need)
- The phone will now show up under Access control end-stations
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-06-2023 12:09 AM
Hi James_A
can you please clarify what is your goal? If you send FA-VLAN:ISID=0:10010100 then it should be untagged on egress and on ingress it goes to 10010100 I-SID.
Another approach is the combination of AutoSense and NAC and LLDP:
If you want the phone to appear in XIQ-SE access control end-stations, i.e. the phone to RADIUS authenticate, while still benefiting from LLDP-Med on the switch the recipe is:
- Set the global auto-sense voice I-SID / VLAN-id on the switch
- Let the access ports have auto-sense enabled
- Do not enable LLDP-auth for the phones
- On the RADIUS server side (access control policy mapping or Policy role) DO NOT return ANY VLAN/I-SID via RADIUS
The phone will then:
- Get the Voice VLAN from LLDP as well as other phone related LLDP parameters, like Qos, etc
- The phones’ MAC will be used for RADIUS MAC authentication (or EAP auth if using TLS…)
- The switch auto-sense port will have already positioned the auto-sense Voice I-SID/VLAN on the access port
- When/if the RADIUS server returns “Permit”, then the phone is allowed to send traffic onto the Voice VLAN (NOTE, the RADIUS response must not return any I-SID/VLAN; no need)
- The phone will now show up under Access control end-stations
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-09-2023 01:58 AM
Hi Zdeněk_Pala,
My goal is to get it working with the least effort. On EXOS I gave up and will just do it the way I had before, with LLDP and a static egress on the port, and no attributes returned via RADIUS. Which is good because that matches how you have suggested to do it for VOSS, I just had to run "no auto-sense eapol voice lldp-auth" and it worked fine, thank you.
Now for a bonus question - how do I get the IP address to show up in the end-stations table?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
04-10-2023 04:59 AM
For VOSS edge the best way is to use DHCP snooping = mirror the DHCP responses to the Acess Control Engine.