- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeControl
- Re: Extreme Control Machine + User authentication ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Extreme Control Machine + User authentication fails
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-05-2021 01:21 PM
Hi,
This Topic is a a follow up to
Although, I hopefully configured everything as advised and discussed in above thread,
Machine + User authentication fails. (Machine auth ONLY works fine, now!)
Below is a screenshot of the EvaluationTool result:
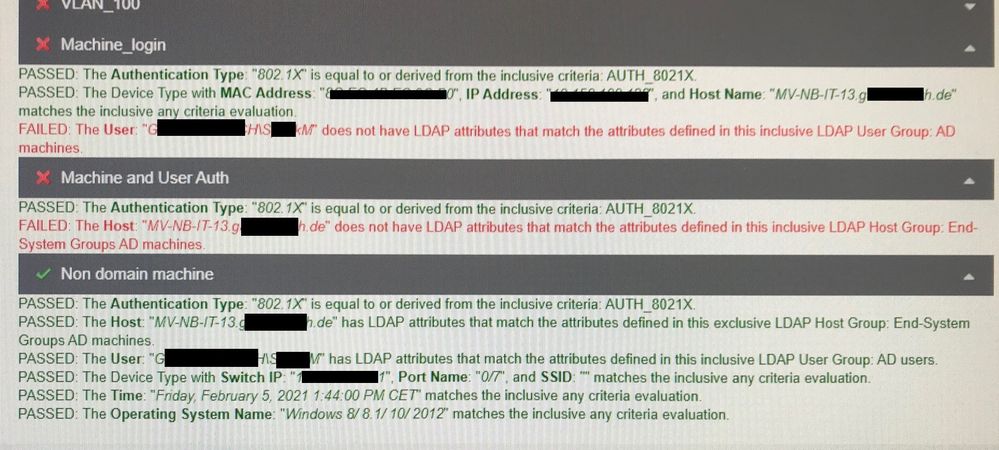
I don´t see the mistake….
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-26-2021 10:35 AM
Dear all,
today customer tested the solution/correction and it worked.
Below my solution/explanation:
In an earlier mentioned documentation (https://extremeportal.force.com/ExtrArticleDetail?an=000080814) I primarily followed it was advised to use “cn” as Host Search Attibute (within the LDAP-configuration of “Domain users”
At least in my environment, this did not work (as shown in above screenshots). The solution was to use “dNSHostName” as Host Search Attibute (which is the default).
Changing this, the configuration worked. Machine AND User-Authentication are passed successfull.
Unfortunately, this solution is already described in https://extremeportal.force.com/ExtrArticleDetail?an=000082479 which I found during my troubleshooting.
In addition to this modification of the solution, I changed the advised order of the Rules.
Instead of
- Authenticate and authorise a machine
- Authenticate and authorise a machine as a valid domain computer with a valid domain user logged in
- Deny a valid user who is on a non-domain (BYOD) computer
In my environment, Rule “2” never will be verified, after a Machine was successfully authenticated.
So, no user-authentication will ever happen.
For that reason, I switched the order of rule 1 and 2 and afterwards, all variations could be verified and authenticated.
Thanks all for your assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-05-2021 06:58 PM
Hello SDR, hello Mig,
I'm a little confused. What are you trying to implement SDR? Based on your ruleset, I assumed you were using the procedure described here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-05-2021 06:36 PM
Hi SDR,
Looking at those screens I see:
- From the rules: “Machine and User Auth” is expecting “End-Systems Groups AD machines”
- From the evaluation tool: “Th Host ...doesn’t have LDAP attributes..in this inclusive LDAP Host Group End-Systems Groups AD machines”
Looking at the the description of the workflows and scripts from Zdenek we see:
"Add MAC to Domain Computers" is executed when the computer authenticates. The MAC address is added to End-System and the timestamp is created (updated). Consequent User authentication can be combined with the condition of the End-System group. "Clear old End-Systems in the group" checks if the timestamp is older than X hours and old End-Systems are deleted from the group.
From the script description, it means that the HOST (read “End-System”) is to be looked into a group of MAC adresses while you defined and LDAP group in the rule for the statement “End-System is in”.
To make it shorter, you’ll store (for a defined period of time) all the MAC addresses from the AD computers (having been authenticated) in a group and check if the authenticating user is with a computer having his MAC in this group.
I know that the way this script works is not very intuitive (looking for a MAC to see if a computer belongs to an AD domain) but there are some technical constrains on the authentication steps that implies this solution.
Mig
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-05-2021 05:47 PM
Hello SDR,
your maschine is matching IS NOT in End-System Groups AD machine
and is not matching IS in End-System Groups AD machine
=> Are you 100% sure that the maschine is in the expacted AD group?
That’s why I ask if you can see if the client is in the group (with the LDAP test tool)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-05-2021 01:40 PM
See below - as we are still testing, we did not focus on the “actions” (profiles)

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-05-2021 01:36 PM
We already did and to my understanding, the tests were sucessfull.
